Reflected XSS into attribute with angle brackets HTML-encoded | Dec 29, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Reflected XSS into attribute with angle brackets HTML-encoded! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab contains a reflected cross-site scripting vulnerability in the search blog functionality where angle brackets are HTML-encoded. To solve this lab, perform a cross-site scripting attack that injects an attribute and calls the alert function.
Exploitation
Home page:
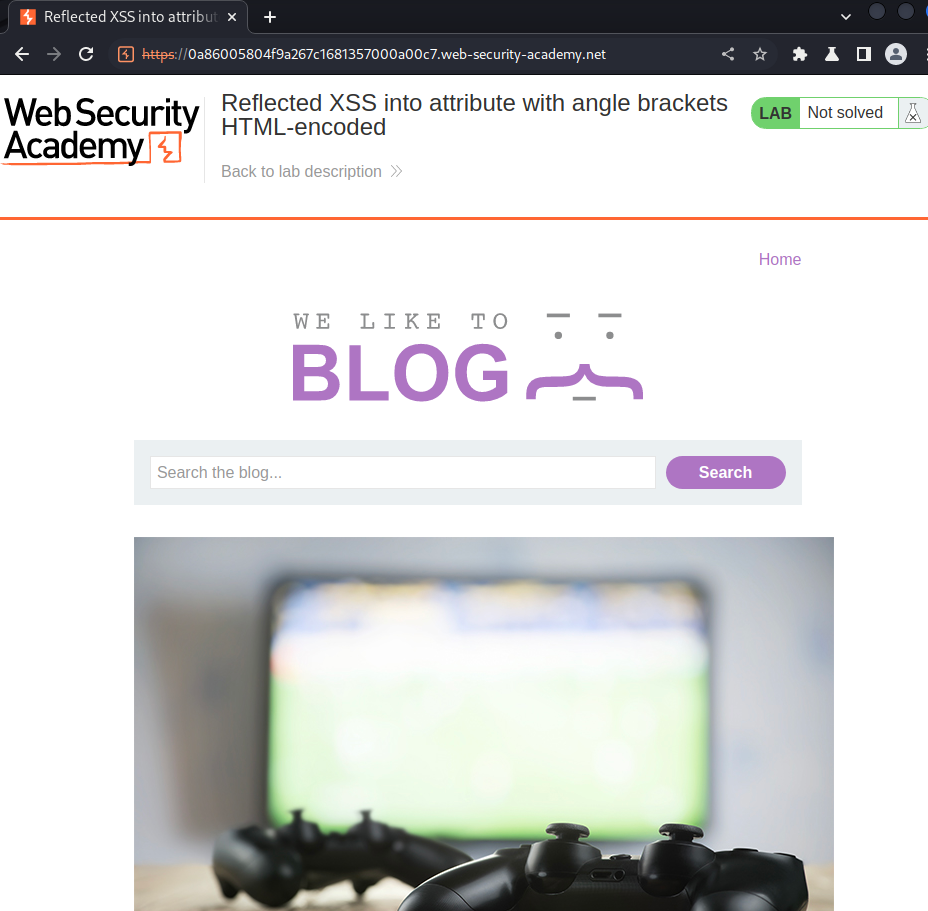
In here, we can see there is a search box.
Let's search something:
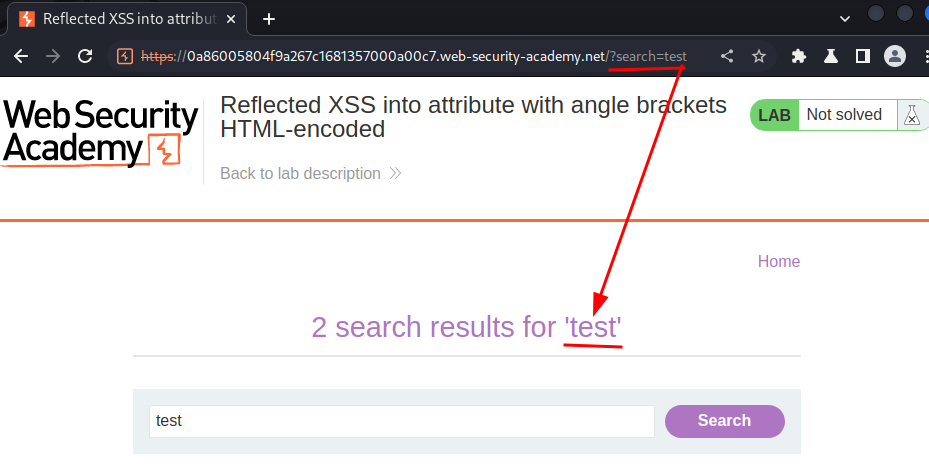
As you can see, our input is reflected to the web page.
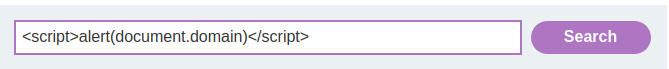
Let's try to inject an XSS payload:
<script>alert(document.domain)</script>
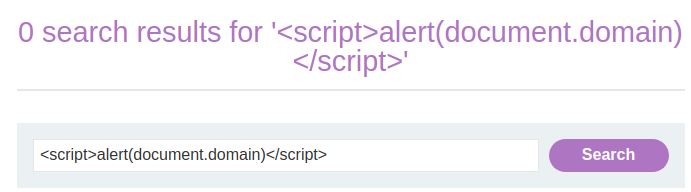
View souce page:
<section class=blog-header>
<h1>0 search results for '<script>alert(document.domain)</script>'</h1>
<hr>
</section>
Hmm… The angle brackets were HTML encoded!
To bypass that, we can use event handler:
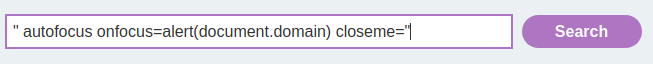
" autofocus onfocus=alert(document.domain) closeme="
The above payload creates an onfocus event that will execute JavaScript when the element receives the focus, and also adds the autofocus attribute to try to trigger the onfocus event automatically without any user interaction. Finally, it adds x=" to gracefully repair the following markup.
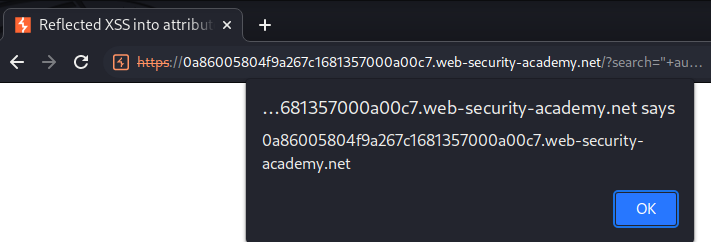
We did it!
What we've learned:
- Reflected XSS into attribute with angle brackets HTML-encoded