Stored XSS into anchor href attribute with double quotes HTML-encoded | Dec 29, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Stored XSS into anchor href attribute with double quotes HTML-encoded! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab contains a stored cross-site scripting vulnerability in the comment functionality. To solve this lab, submit a comment that calls the alert function when the comment author name is clicked.
Exploitation
Home page:
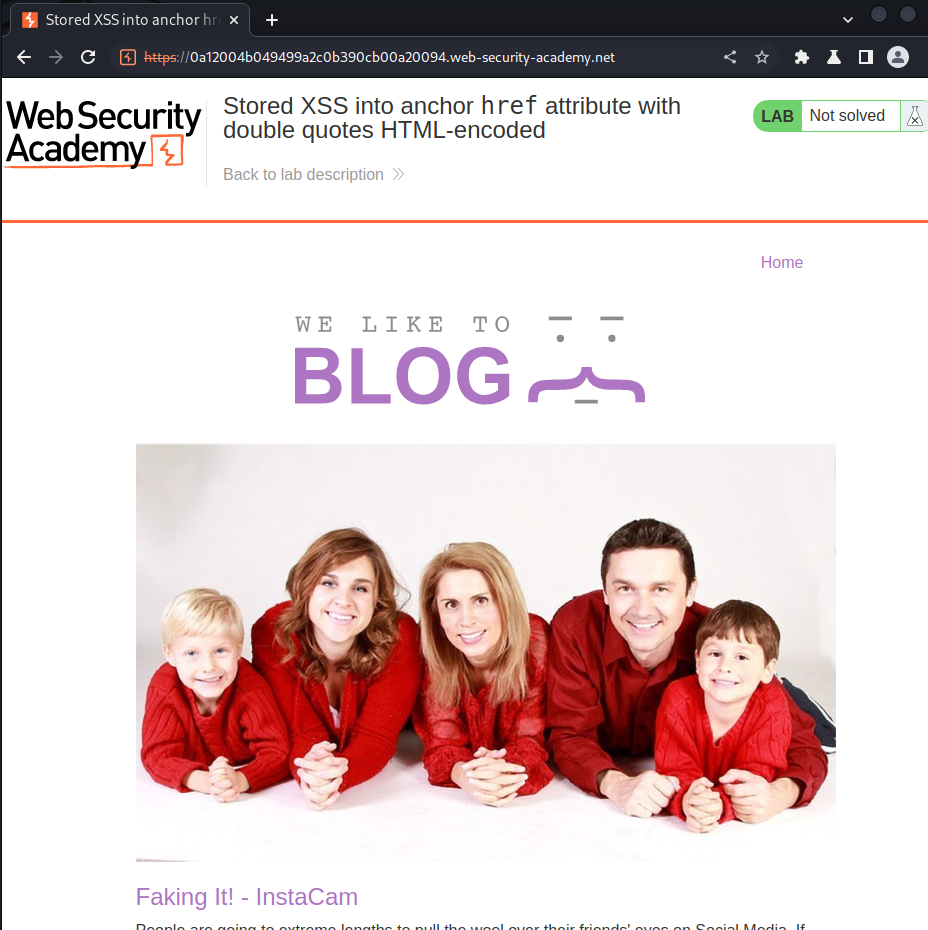
In the home page, we can view other posts:
And we can leave some comments.
Let's try to inject HTML code:
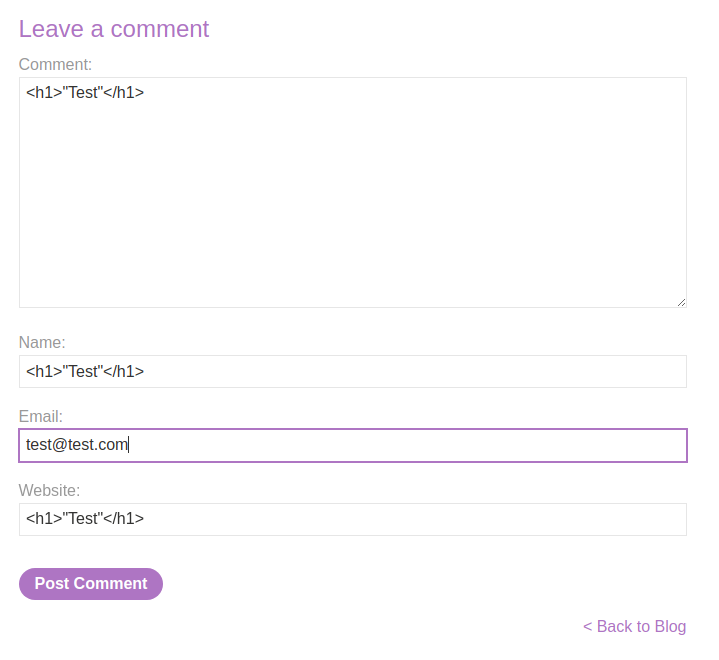
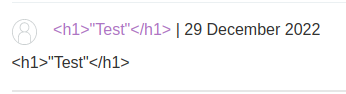
View source page:
<section class="comment">
<p>
<img src="/resources/images/avatarDefault.svg" class="avatar">
<a id="author" href="<h1>"Test"</h1>"><h1>"Test"</h1></a> | 29 December 2022
</p>
<p><h1>"Test"</h1></p>
<p></p>
</section>
As you can see, our <>" is HTML encoded.
However, we can still inject JavaScript code in the <a> tag's href attribute:
javascript:alert(document.domain)
In here, we're using the javascript pseudo-protocol to execute script.
Let's try to exploit it:
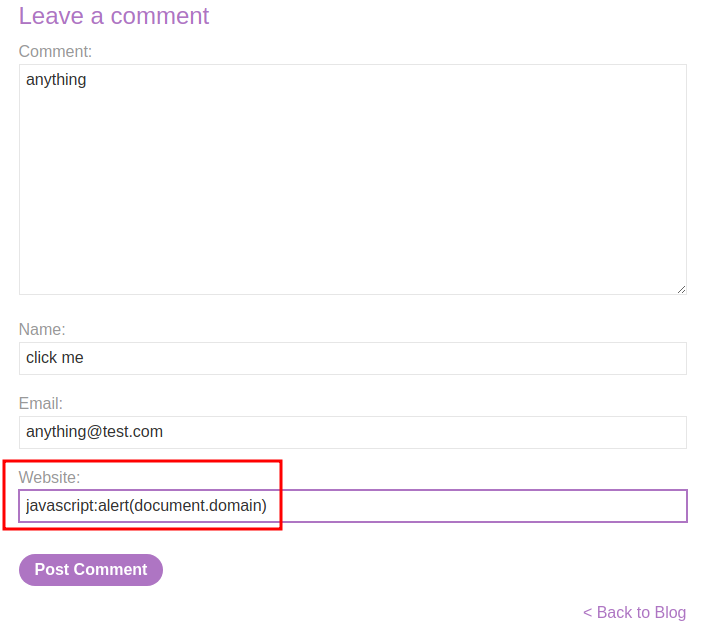
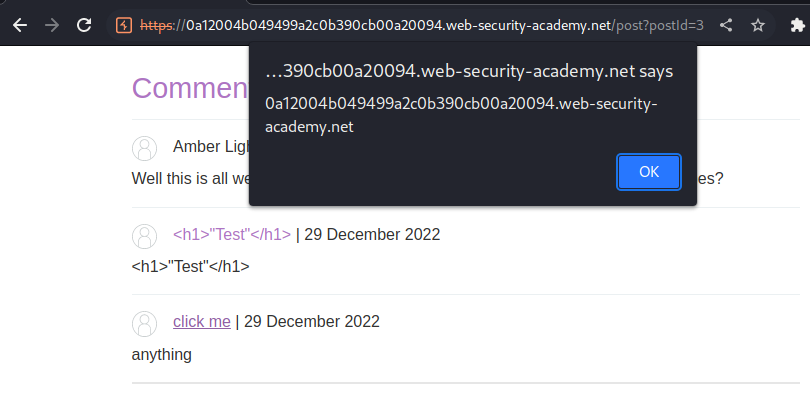
Boom, we successfully exploited stored XSS.
What we've learned:
- Stored XSS into anchor
hrefattribute with double quotes HTML-encoded