Source code disclosure via backup files | Dec 16, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Information disclosure in error messages! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab leaks its source code via backup files in a hidden directory. To solve the lab, identify and submit the database password, which is hard-coded in the leaked source code.
Exploitation
Home page:
In robots.txt, I found something interesting:
┌──(root🌸siunam)-[~/ctf/Portswigger-Labs/Information-Disclosure/ID-3]
└─# curl https://0a130056031f083bc036cc3700250088.web-security-academy.net/robots.txt
User-agent: *
Disallow: /backup
robots.txtis a plaintext file that let robots(crawlers) know which page shouldn't be indexed.
Let's go there:
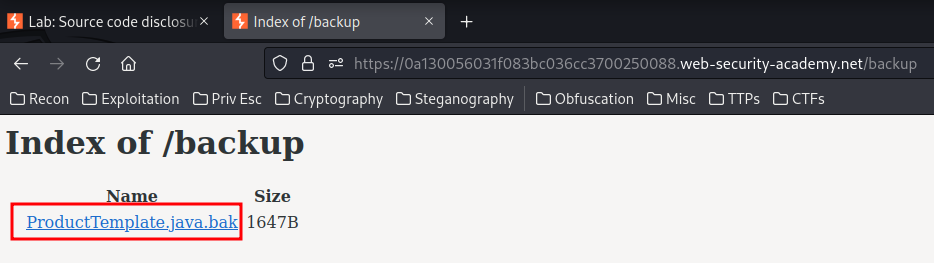
Found a backup file! ProductTemplate.java.bak.
We can download it via wget:
┌──(root🌸siunam)-[~/ctf/Portswigger-Labs/Information-Disclosure/ID-3]
└─# wget https://0a130056031f083bc036cc3700250088.web-security-academy.net/backup/ProductTemplate.java.bak
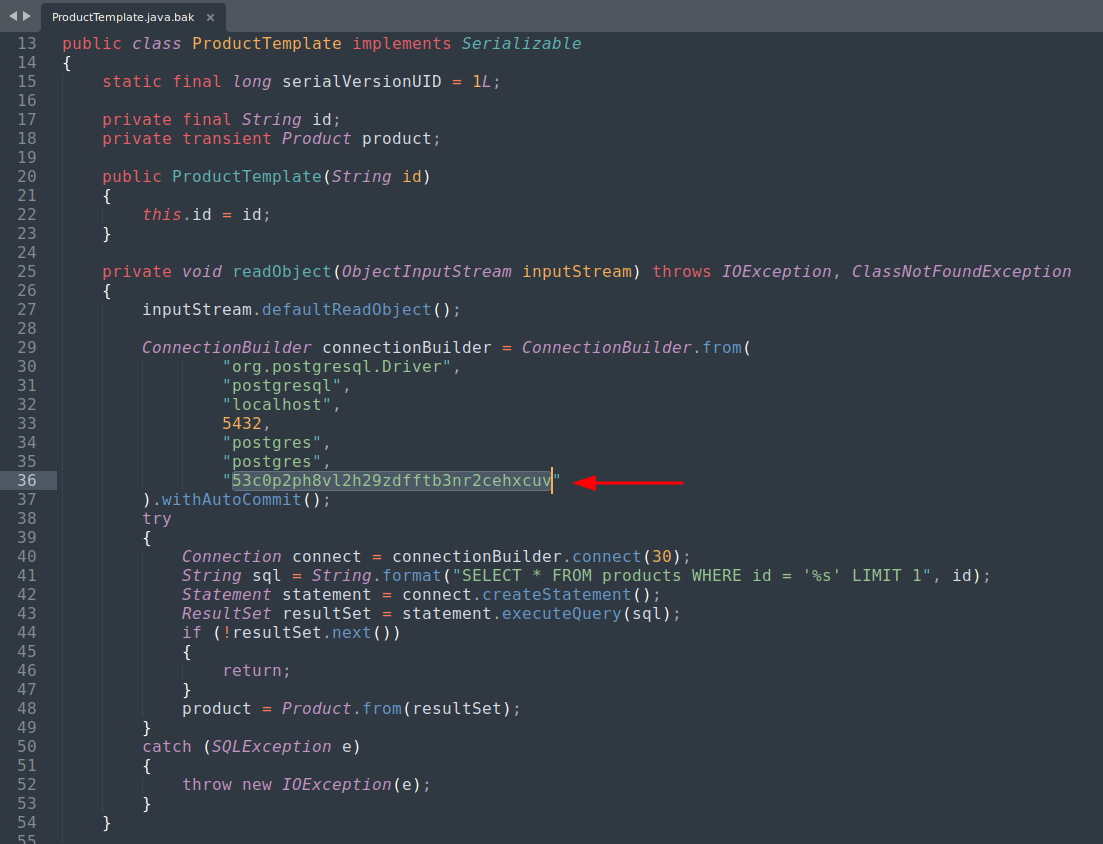
This random string looks like the password for the PostgresSQL database!
What we've learned:
- Source code disclosure via backup files