SQL injection vulnerability allowing login bypass | Dec 3, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: SQL injection vulnerability allowing login bypass! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab contains an SQL injection vulnerability in the login function.
To solve the lab, perform an SQL injection attack that logs in to the application as the administrator user.
Explotation
Home page:
We can see that there is a My account link, let's enumerate that page!
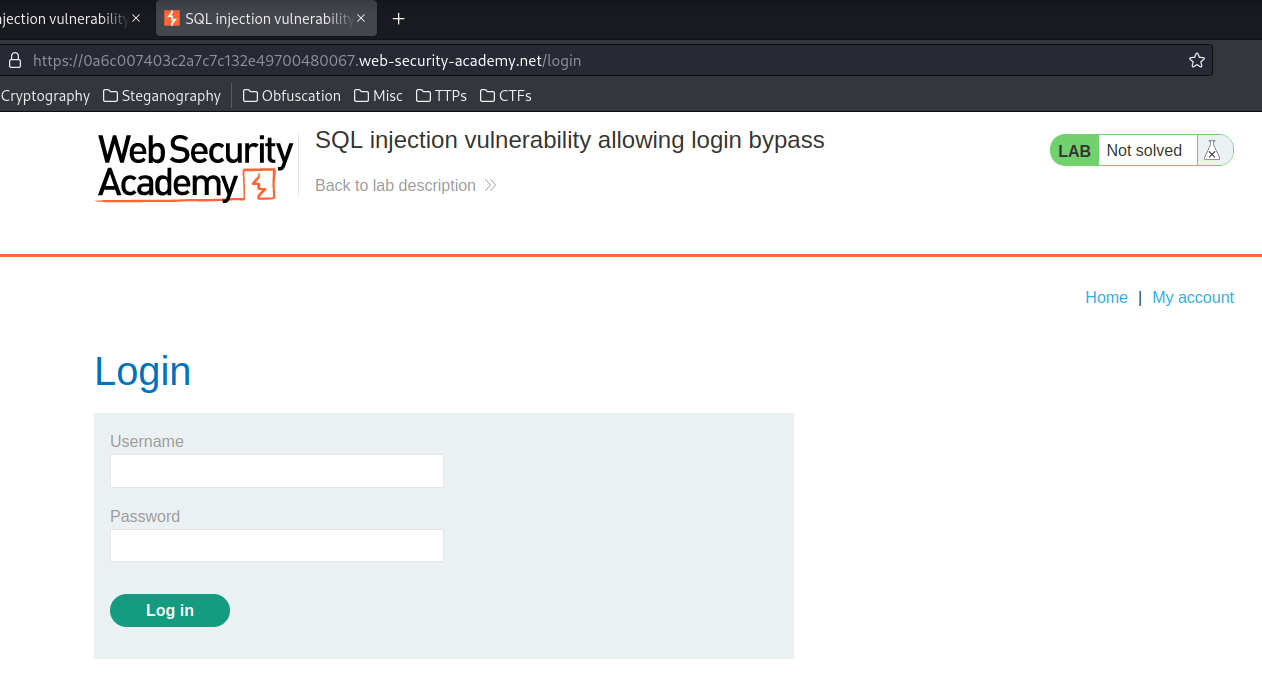
It's a login form!
We can try to guess the administrator user's password! Like administrator:password
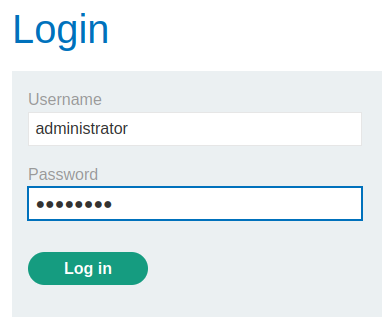
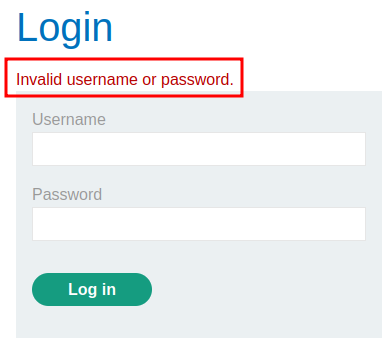
Nope. It didn't work.
Now, let's try to do a SQL injection to bypass the authentication!
Imagine this is the login SQL statement:
SELECT * FROM users WHERE username = '' AND password = ''
Since there is no protection against SQL injection, we can injection some malicious payloads in the username field!
To login as administrator without the password, we can:
Payload:
administrator'-- -
New SQL statement:
SELECT * FROM users WHERE username = 'administrator'-- -' AND password = ''
As you can see, we've commented out the AND clause, which means we don't need the administrator password!
Let's use that payload to bypass the authentication!
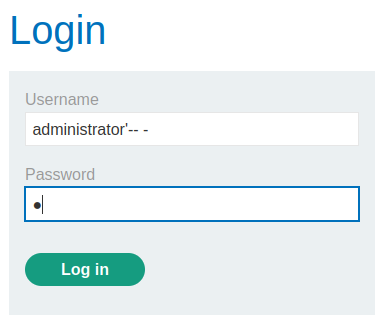
Note: The password can be anything.
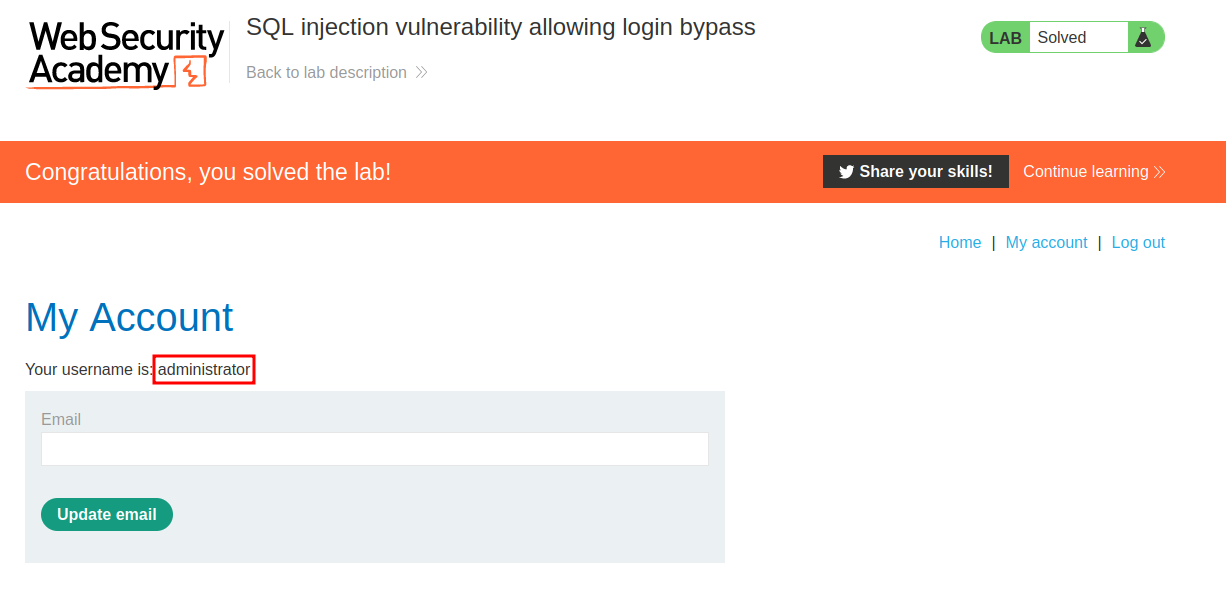
We're logged in as user administrator!
Conclusion
What we've learned:
- SQL injection vulnerability allowing login bypass