Blind SSRF with out-of-band detection | Mar 1, 2023
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Blind SSRF with out-of-band detection! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded.
To solve the lab, use this functionality to cause an HTTP request to the public Burp Collaborator server.
Exploitation
Home page:
After poking around at the web application, I found nothing we can test with.
Let's take a look at the "hidden" things.
SSRF via the Referer header
Some applications employ server-side analytics software that tracks visitors. This software often logs the Referer header in requests, since this is of particular interest for tracking incoming links. Often the analytics software will actually visit any third-party URL that appears in the Referer header. This is typically done to analyze the contents of referring sites, including the anchor text that is used in the incoming links. As a result, the Referer header often represents fruitful attack surface for SSRF vulnerabilities.
That being said, we can try to leverage the Referer header to perform blind SSRF attacks.
What is blind SSRF?
Blind SSRF vulnerabilities arise when an application can be induced to issue a back-end HTTP request to a supplied URL, but the response from the back-end request is not returned in the application's front-end response.
What is the impact of blind SSRF vulnerabilities?
The impact of blind SSRF vulnerabilities is often lower than fully informed SSRF vulnerabilities because of their one-way nature. They cannot be trivially exploited to retrieve sensitive data from back-end systems, although in some situations they can be exploited to achieve full remote code execution.
How to find and exploit blind SSRF vulnerabilities
The most reliable way to detect blind SSRF vulnerabilities is using out-of-band (OAST) techniques. This involves attempting to trigger an HTTP request to an external system that you control, and monitoring for network interactions with that system.
The easiest and most effective way to use out-of-band techniques is using Burp Collaborator. You can use Burp Collaborator to generate unique domain names, send these in payloads to the application, and monitor for any interaction with those domains. If an incoming HTTP request is observed coming from the application, then it is vulnerable to SSRF.
Note:
It is common when testing for SSRF vulnerabilities to observe a DNS look-up for the supplied Collaborator domain, but no subsequent HTTP request. This typically happens because the application attempted to make an HTTP request to the domain, which caused the initial DNS lookup, but the actual HTTP request was blocked by network-level filtering. It is relatively common for infrastructure to allow outbound DNS traffic, since this is needed for so many purposes, but block HTTP connections to unexpected destinations.
Armed with above information, we can try to indentify blind SSRF vulnerability via the Referer header.
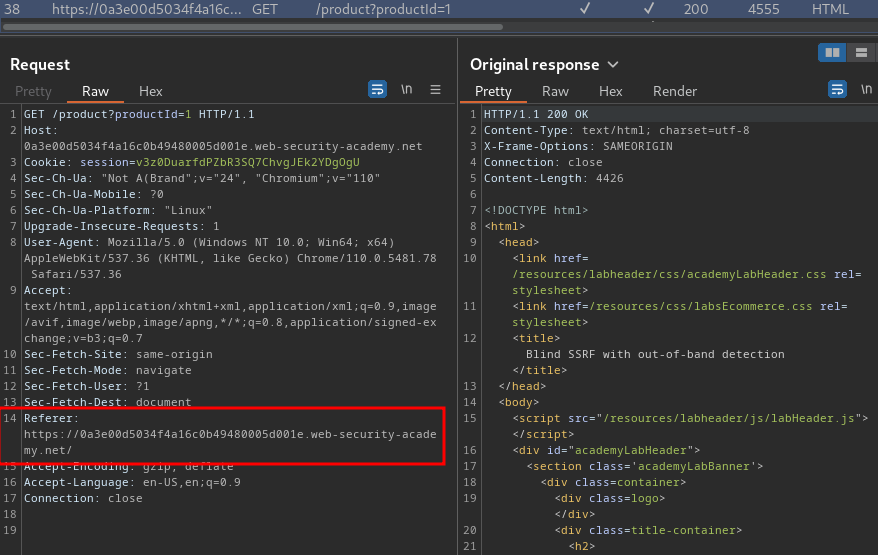
When we go to the product page, it'll include a Referer header:
Now, we can:
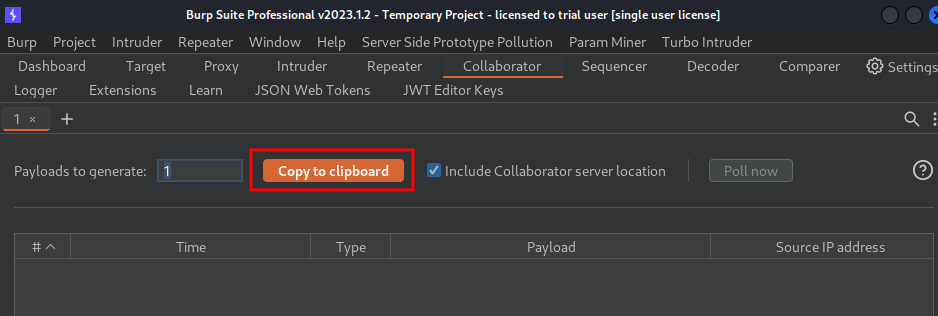
- Go to Burp Suite's Collaborator, and copy the payload:
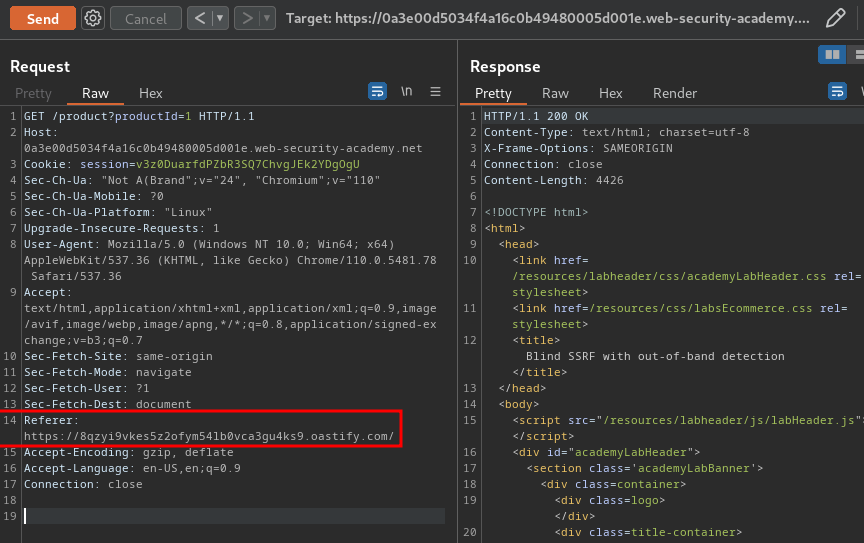
- Add header
Referer, and send the request:
- Go back to Burp Suite's Collaborator, and click "Poll now":
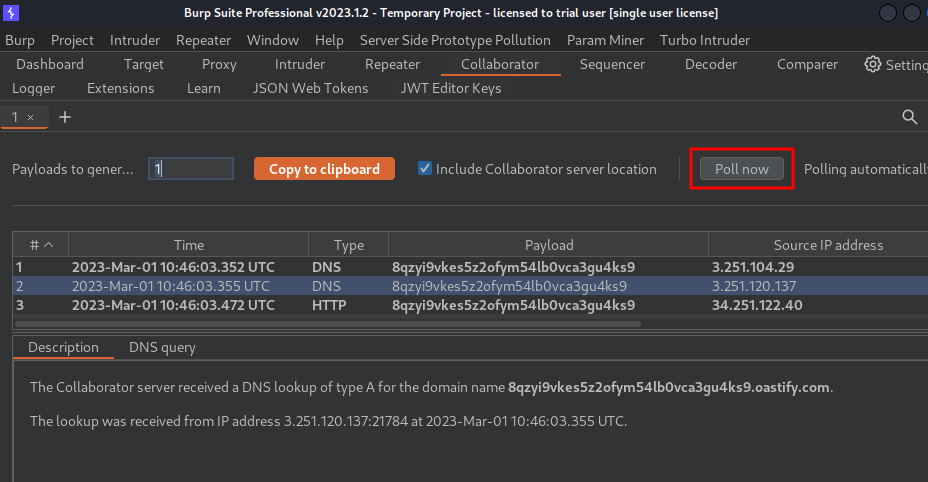
As you can see, we received 2 DNS lookups! Which means the web application is indeed vulnerable to blind SSRF via the Referer header!
What we've learned:
- Blind SSRF with out-of-band detection