WarZone1 | Nov 1, 2022
Introduction
Welcome to my another writeup! In this TryHackMe WarZone1 room, you'll learn: Inspecting malicious traffics in Brim and more! Without further ado, let's dive in.
Background
You received an IDS/IPS alert. Time to triage the alert to determine if its a true positive.
Difficulty: Medium
- Overall difficulty for me: Medium
You work as a Tier 1 Security Analyst L1 for a Managed Security Service Provider (MSSP). Today you're tasked with monitoring network alerts.
A few minutes into your shift, you get your first network case: Potentially Bad Traffic and Malware Command and Control Activity detected. Your race against the clock starts. Inspect the PCAP and retrieve the artifacts to confirm this alert is a true positive.
Your tools:
Task 1 - Your shift just started and your first network alert comes in.
Question 1 - What was the alert signature for Malware Command and Control Activity Detected?
In the Desktop directory, we have Zone1.pcap packet captured file:
Now, we can use Brim to inspect that!
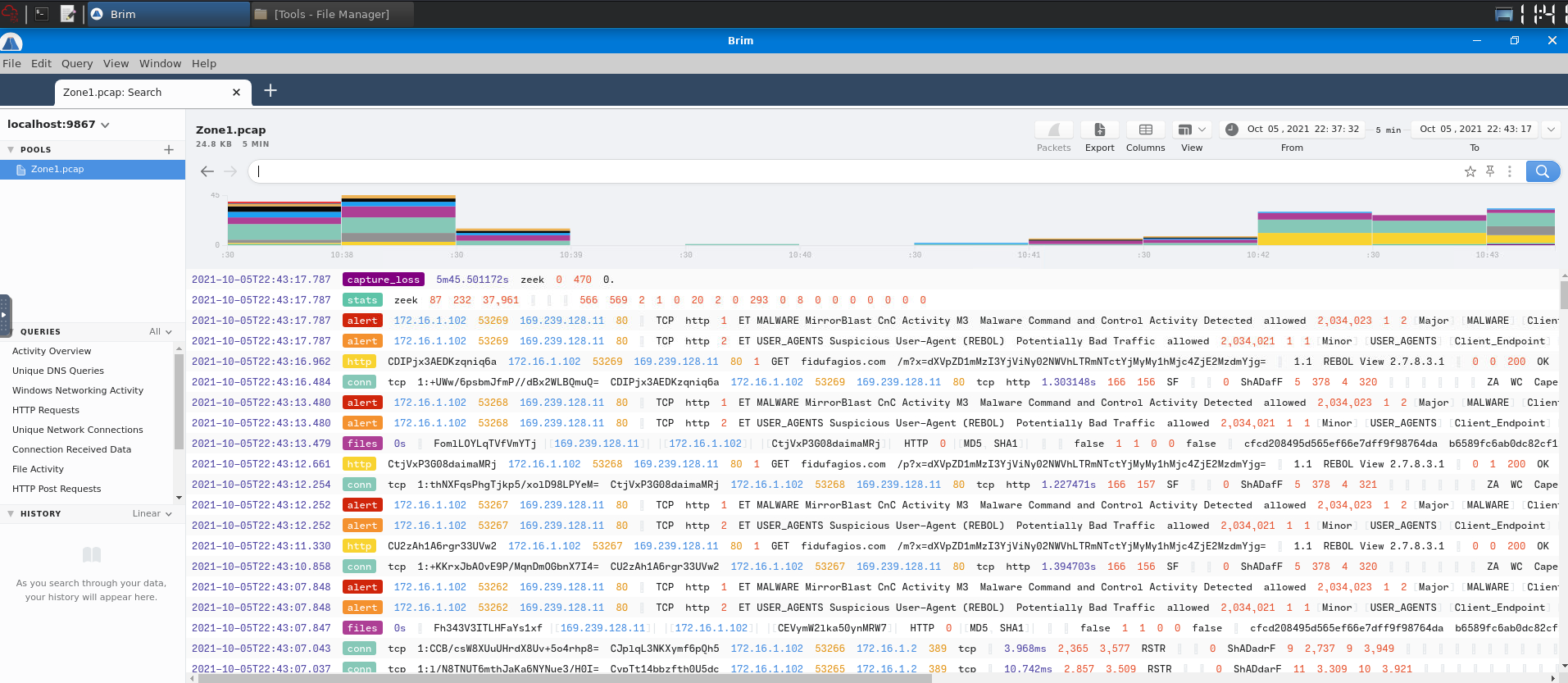
To view all alert signatures, we can use this filter:
alert.signature
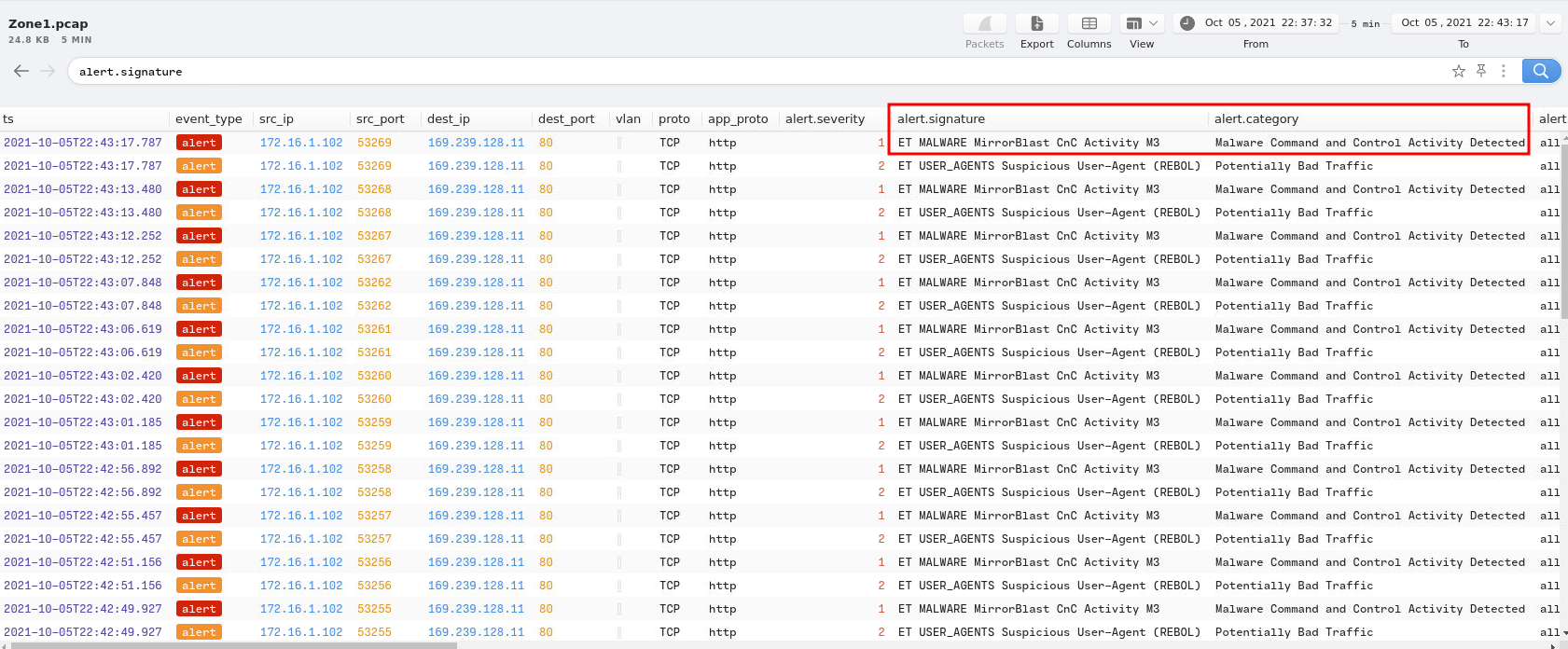
- Answer:
ET MALWARE MirrorBlast CnC Activity M3
Question 2 - What is the source IP address? Enter your answer in a defanged format.

- Answer:
172[.]16[.]1[.]102
Question 3 - What IP address was the destination IP in the alert? Enter your answer in a defanged format.

- Answer:
169[.]239[.]128[.]11
Question 4 - Inspect the IP address in VirsusTotal. Under Relations > Passive DNS Replication, which domain has the most detections? Enter your answer in a defanged format.
Let's go to VirusTotal and submit the attacker IP address!

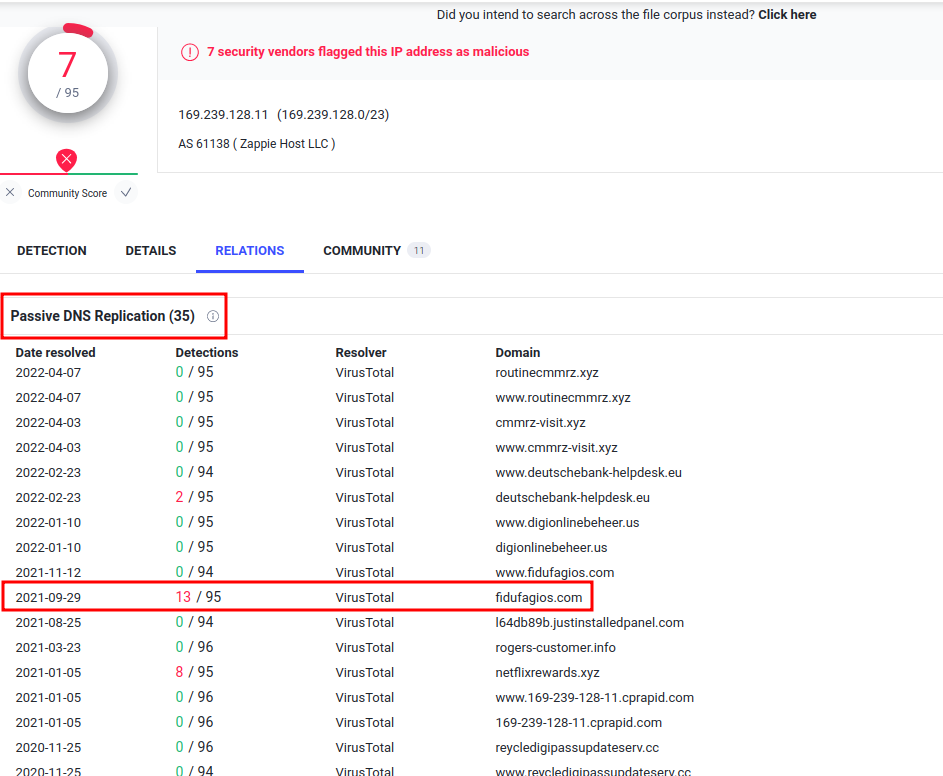
- Answer:
fidufagios[.]com
Question 5 - Still in VirusTotal, under Community, what threat group is attributed to this IP address?
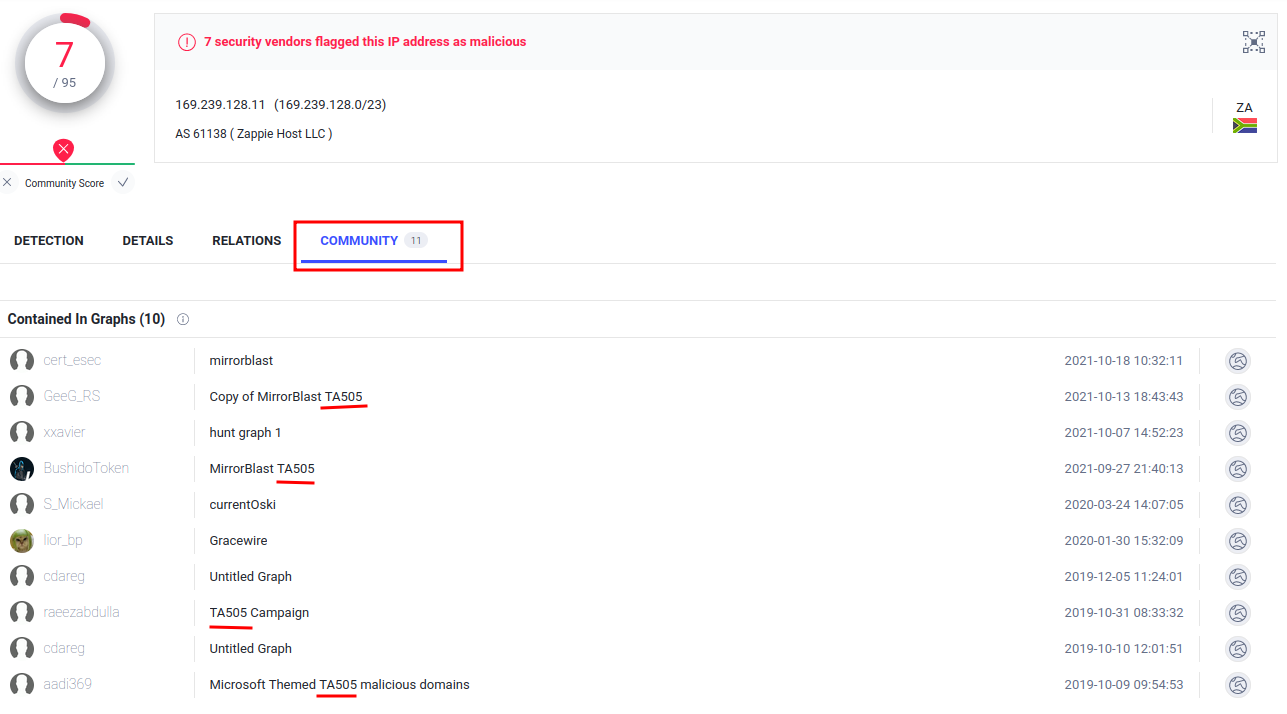
- Answer:
TA505
Question 6 - What is the malware family?
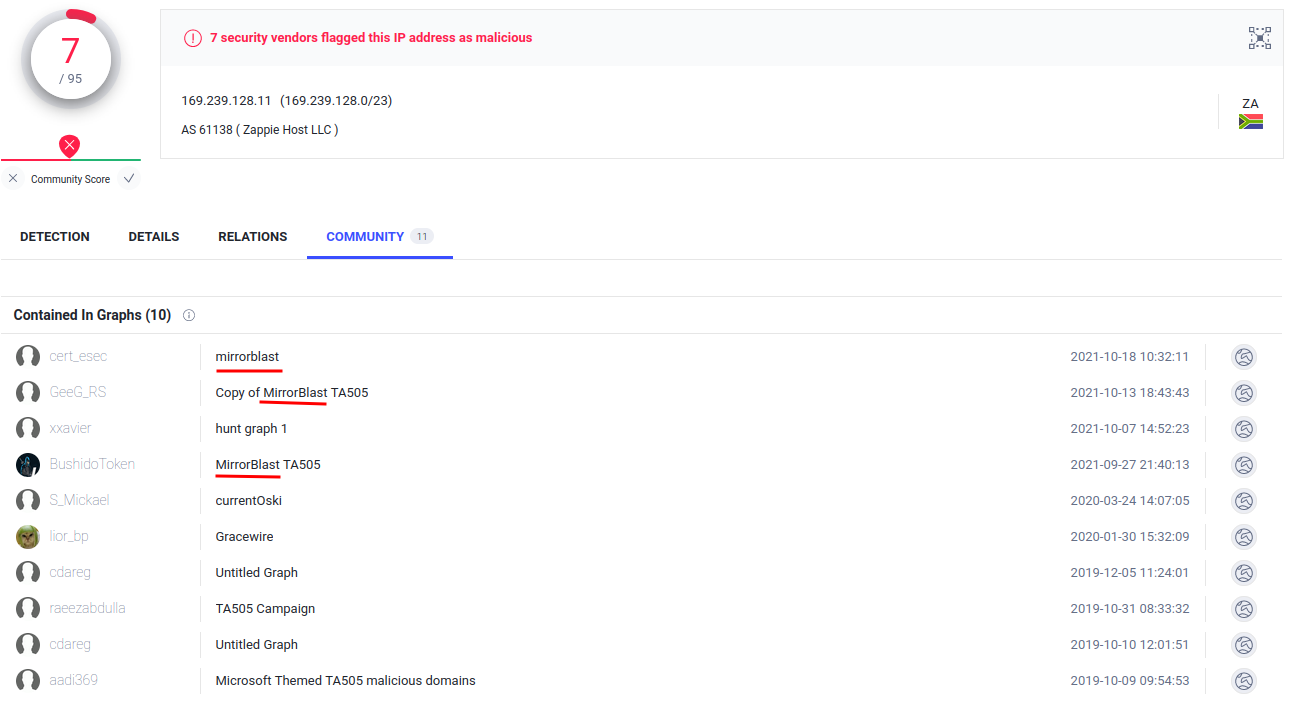
- Answer:
MirrorBlast
Question 7 - Do a search in VirusTotal for the domain from question 4. What was the majority file type listed under Communicating Files?
Go to VirusTotal Search:
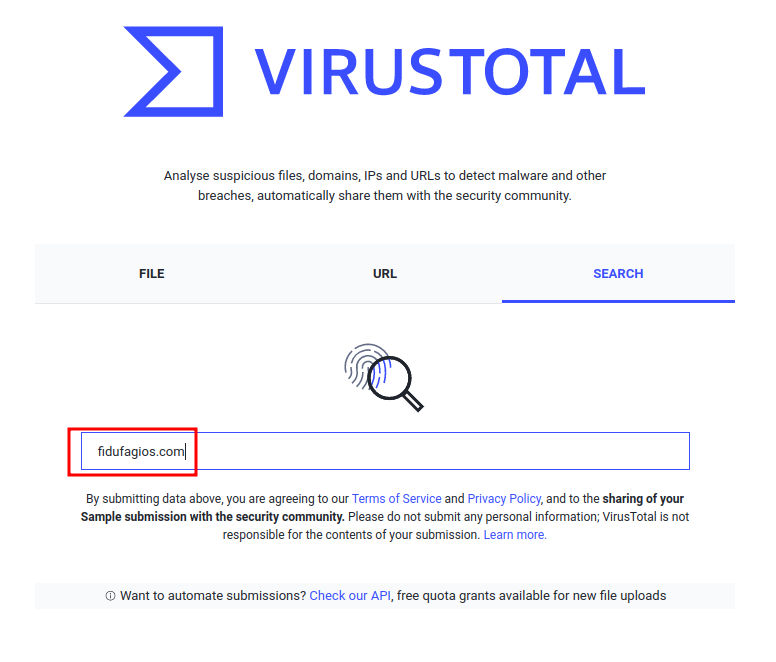
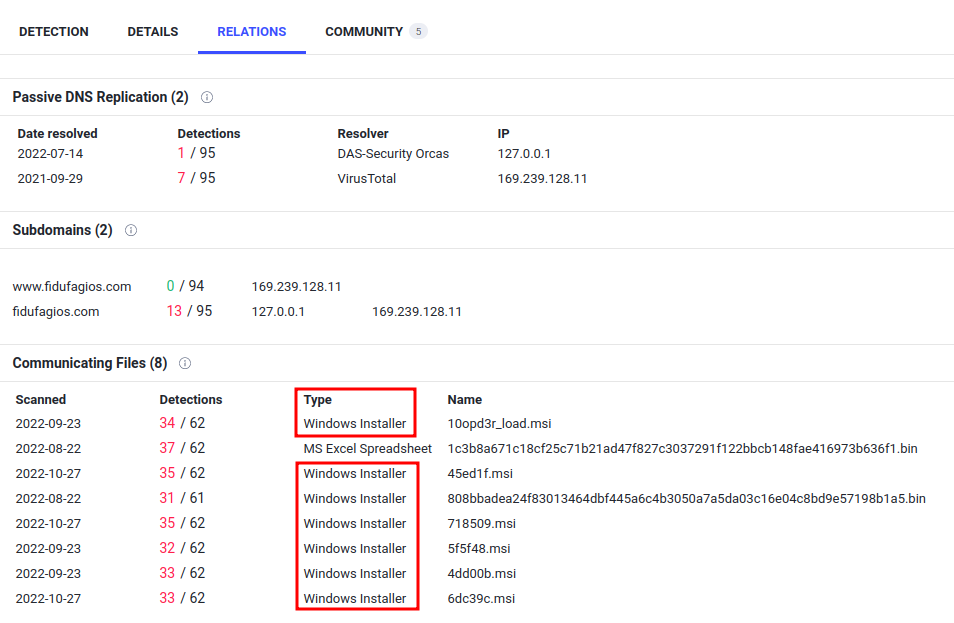
- Answer:
Windows Installer
Question 8 - Inspect the web traffic for the flagged IP address; what is the user-agent in the traffic?
Let's go back to Brim. Here, we can use the above domain fidufagios.com as the filter:
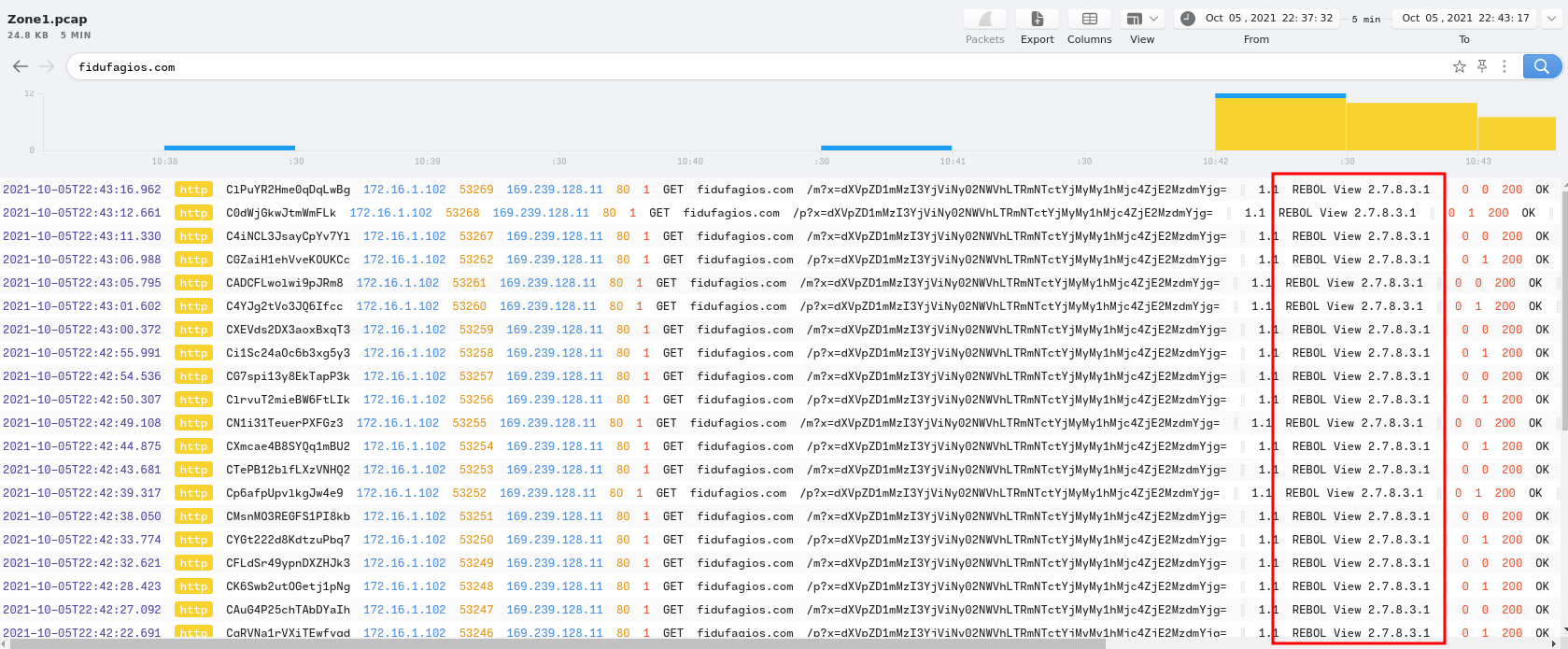
- Answer:
REBOL View 2.7.8.3.1
Question 9 - Retrace the attack; there were multiple IP addresses associated with this attack. What were two other IP addresses? Enter the IP addressed defanged and in numerical order. (format: IPADDR,IPADDR)
Let's use the "HTTP Requests" query to filter all the HTTP requests!
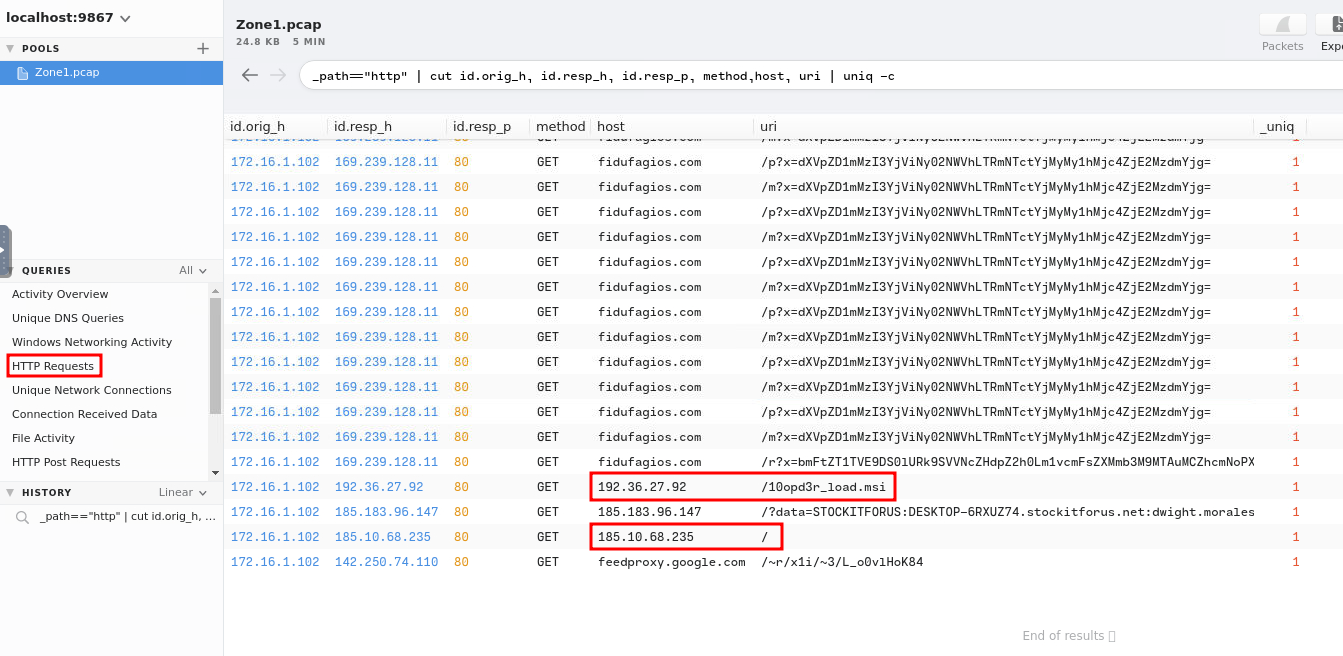
Those 2 IPs look weird!
- Answer:
185[.]10[.]68[.]235,192[.]36[.]27[.]92
Question 10 - What were the file names of the downloaded files? Enter the answer in the order to the IP addresses from the previous question. (format: file.xyz,file.xyz)
We already saw 1 in the previous answer:

Next, we can use the "File Activity" query:
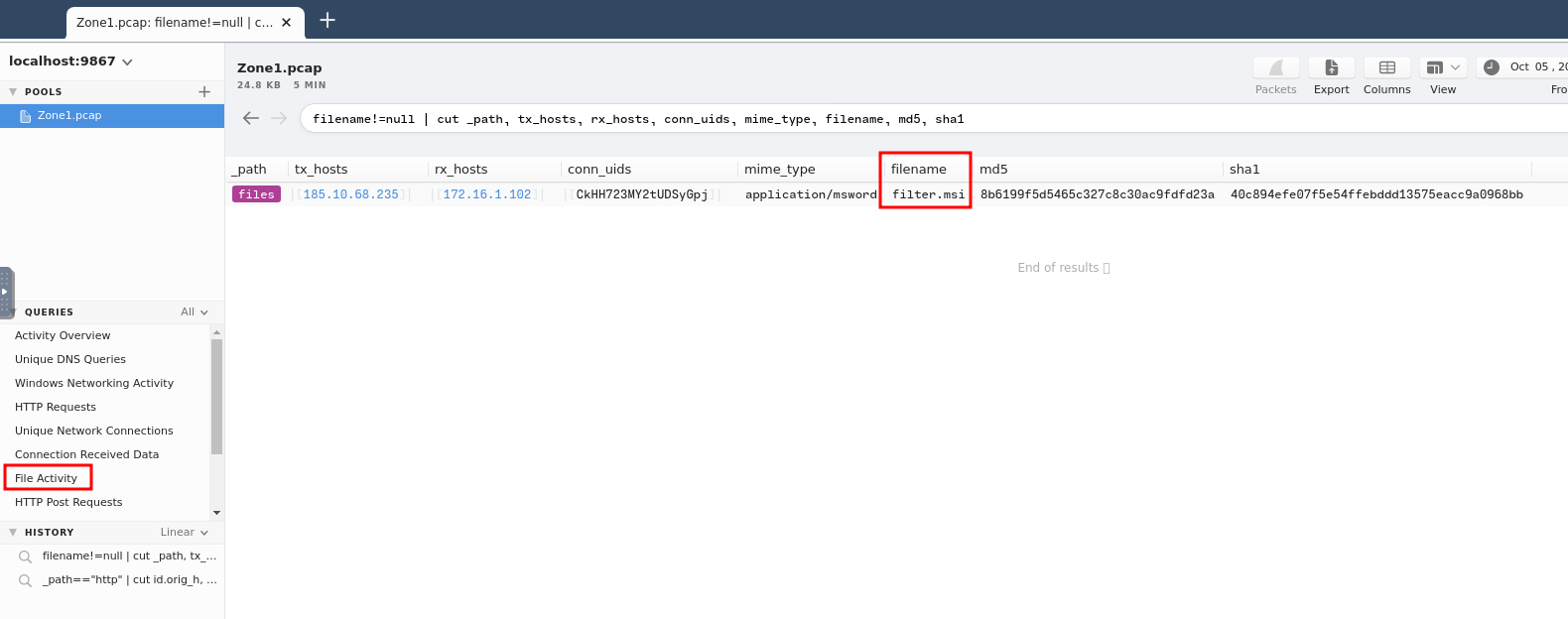
- Answer:
filter.msi,10opd3r_load.msi
Question 11 - Inspect the traffic for the first downloaded file from the previous question. Two files will be saved to the same directory. What is the full file path of the directory and the name of the two files? (format: C:\path\file.xyz,C:\path\file.xyz)
Since Brim doesn't show file's full path, I'll inspect them in WireShark:
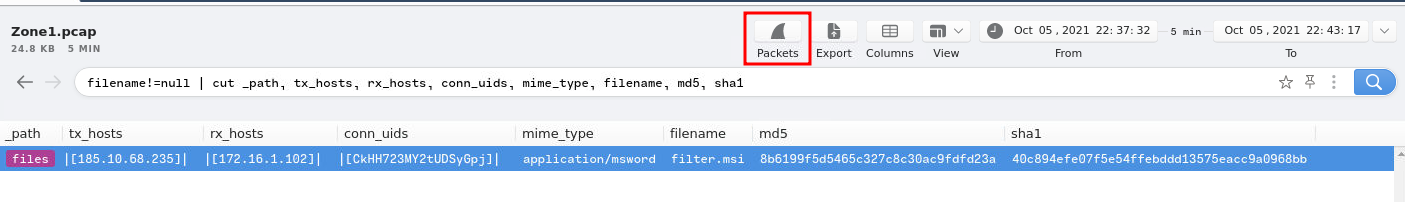

Let's follow the TCP stream!
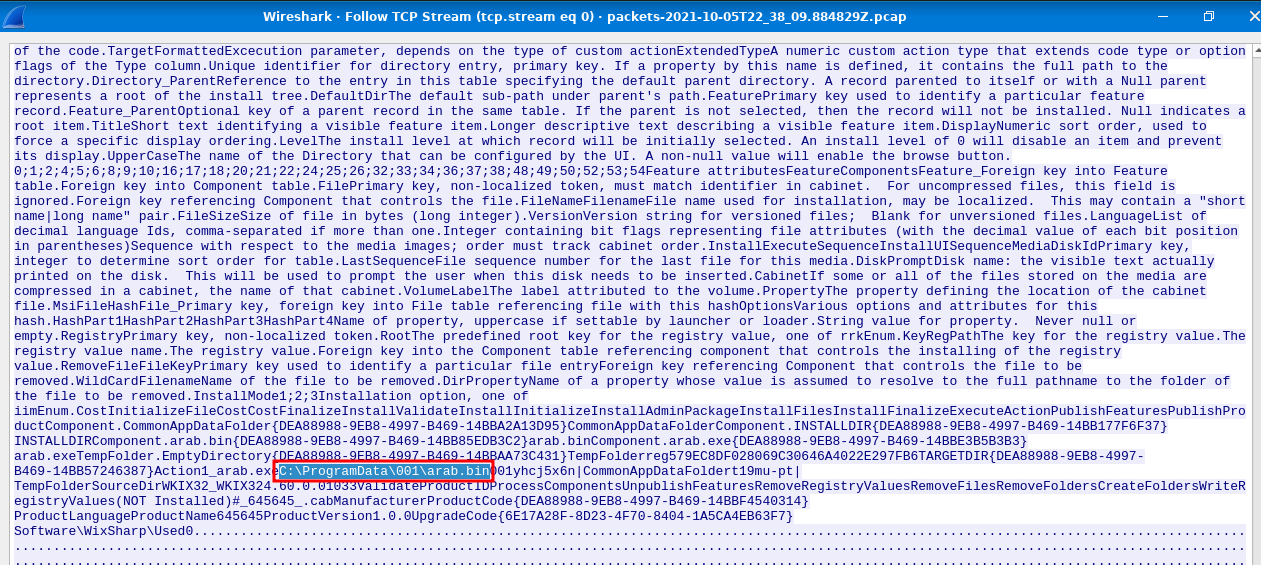
Found it!
- Answer:
C:\ProgramData\001\arab.bin,C:\ProgramData\001\arab.bin
Question 12 - Now do the same and inspect the traffic from the second downloaded file. Two files will be saved to the same directory. What is the full file path of the directory and the name of the two files? (format: C:\path\file.xyz,C:\path\file.xyz)
Again, view the second downloaded file in WireShark:
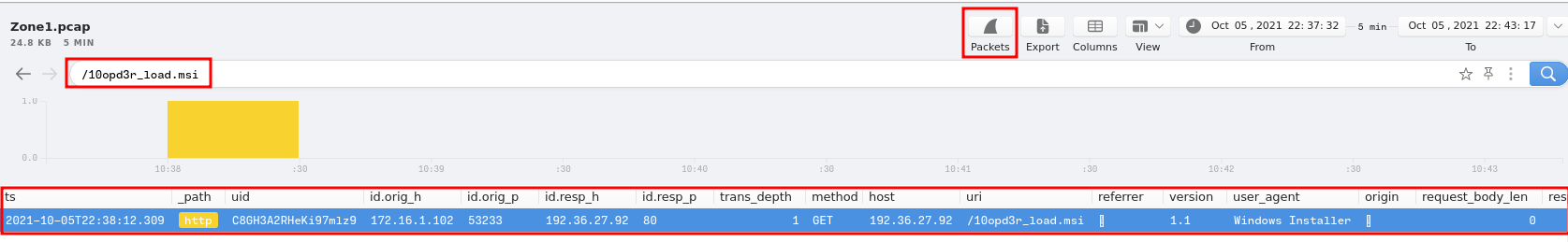
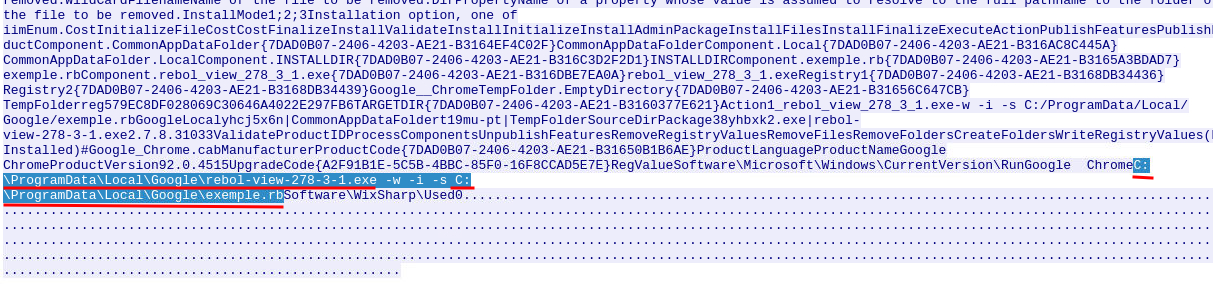
Found it!
- Answer:
C:\ProgramData\Local\Google\rebol-view-278-3-1.exe,C:\ProgramData\Local\Google\exemple.rb
Conclusion
What we've learned:
- Inspecting Malicious Traffics in Brim
- Searching Malicious Domain/IP in VirusTotal
- WireShark Packet Analysis