BuckeyeCTF 2022 Writeups
CTFtime event link: https://ctftime.org/event/1740/
Writeups
- Web
- Misc
- Crypto
- Rev
- soda (Unsolved)
Background
- Starts: 11/4/2022, 8:00:00 PM EDT
- Ends: 11/6/2022, 8:00:00 PM EST
Frequently Asked Questions
What is the format?
Teams will compete to earn points by completing challenges from various categories. Past categories have included cryptography, reverse engineering, web exploitation, and binary exploitation. There are prizes for some divisions.
How big are the teams? What if I don't have a team?
See the table above. There will be a team-forming event prior to CTF weekend, and we also anticipate many Ohio State teams forming at the kickoff event.
I've never done a CTF before, can I still participate?
Absolutely! Above all, a CTF is an opportunity to learn something new. There will be problems appropriate for all experience levels, and you can count on teammates to help you if you get stuck.
OSU Students: check out Cyber Security Club — if you want a head start, we have a training CTF you can try right now!
Who runs BuckeyeCTF?
BuckeyeCTF is run by a small number of dedicated students from the Cyber Security Club @ The Ohio State University.
I have a question not listed here
Contact info@osucyber.club with any additional questions or join our discord.
Overview
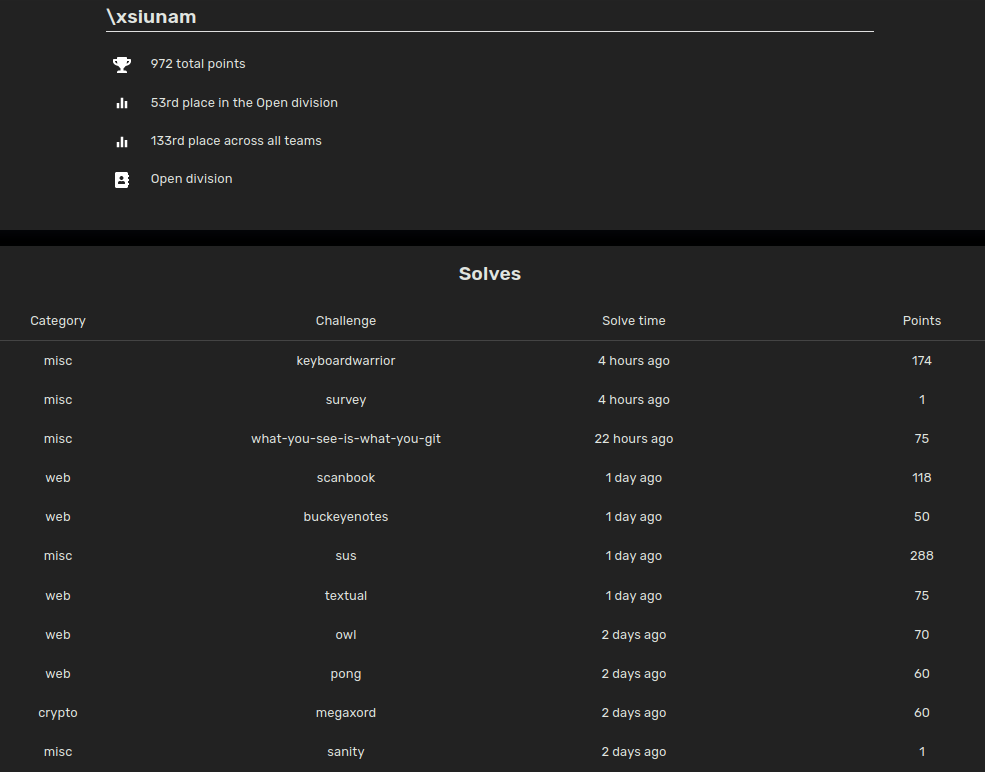
- Solved: 9 (Not Including 1 Point Challenges)
- Points: 972
- Rank: 133rd/688
- Total Teams: 688
- Overall Difficulty To Me: Very Hard
What I've learned in this CTF
- Web:
- SQL Injection & Bypass (buckeyenotes)
- Abusing JavaScript Variables (pong)
- Stealing Cookies via Discord Bot XSS (owl)
- Exploiting LaTeX (textual)
- IDOR (Insecure Direct Object References) (scanbook)
- Misc:
- Audio Steganography (sus)
- Git Log Forensics (what-you-see-is-what-you-git)
- Inspecting BlueTooth Packets (keyboardwarrior)
- Reversing Pokemon Save File?? (pocket-monsters) (Unsolved)
- Crypto:
- Brute Forcing XOR Key (megaxord)
- Rev:
- Reversing Java Application (soda) (Unsolved)