DownUnderCTF 2023 Writeup
CTFTime event link: https://ctftime.org/event/1954

Writeups
- misc:
- osint:
- web:
Background
- Starts: 01 September 2023, 17:30 HKT
- Ends: 03 September 2023, 17:30 HKT
DownUnderCTF is the largest online Australian run Capture The Flag (CTF) competition with over 4100+ registered users and over 1900+ registered teams (2022). Its main goal is to try to up-skill the next generation of potential Cyber Security Professionals and increase the CTF community's size here in Australia. Prizes are only for Australian Secondary or Tertiary school students. However, our CTF is online and open for anyone to play worldwide.
Categories:
- crypto
- pwn
- web
- rev
- misc
- blockchain
- osint
Overview
- Team: ARESx
- Team Solves: 27/68
- Individual Solves: 10/68
- Score: 3075/14341
- Rank: 92/2110
- Overall Difficulty To Me: ★★★★★☆☆☆☆☆

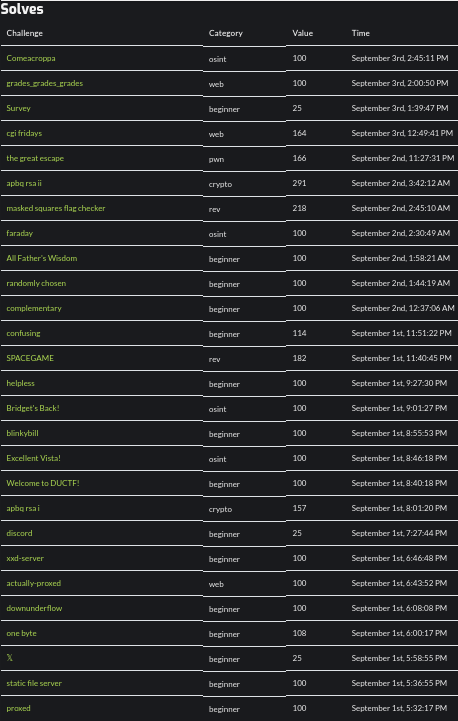
What I've learned in this CTF
- misc:
- Python built-in function
help()shell escape (helpless)
- Python built-in function
- osint:
- Extracting image's metadata via
exiftool(Excellent Vista!) - Reverse image search (Bridget's Back!, Comeacroppa)
- Extracting image's metadata via
- web:
- Proxying via
X-Forwarded-Forheader (proxed) - Exploiting path traversal vulnerability (static file server)
- Exploiting file upload vulnerability with 16 characters chunk (xxd-server)
- Double proxying via
X-Forwarded-Forheader (actually-proxed) - Sign arbitrary JWT via flawed signing process (grades_grades_grades)
- Exploiting Perl's
param()flaw (cgi fridays)
- Proxying via