RITSEC CTF 2023 Writeups
CTFTime event link: https://ctftime.org/event/1860

Writeups
- BIN-PWN:
- ret2win (Unsolved)
- Crypto:
- Forensics:
- Red Team Activity 1 - 4
- Web of Lies (Unsolved)
- Missing Piece Part 1 (Unsolved)
- Steganography:
- Web:
- Reversing:
- Chandi Bot:
Background
- Starts: 31 March 2023, 16:00 UTC
- Ends: 02 April 2023, 16:00 UTC
RITSEC CTF 2023 is a security-focused competition that features the following categories: BIN\PWN, Crypto, Reversing, Forensics, Web, Misc, and more. We welcome beginners and more advanced security friends! There will be three brackets: RIT students, other college students, and everyone else.
Categories:
- BIN-PWN
- Crypto
- Misc
- Forensics
- Steganography
- Web
- Reversing
- Chandi Bot
Overview
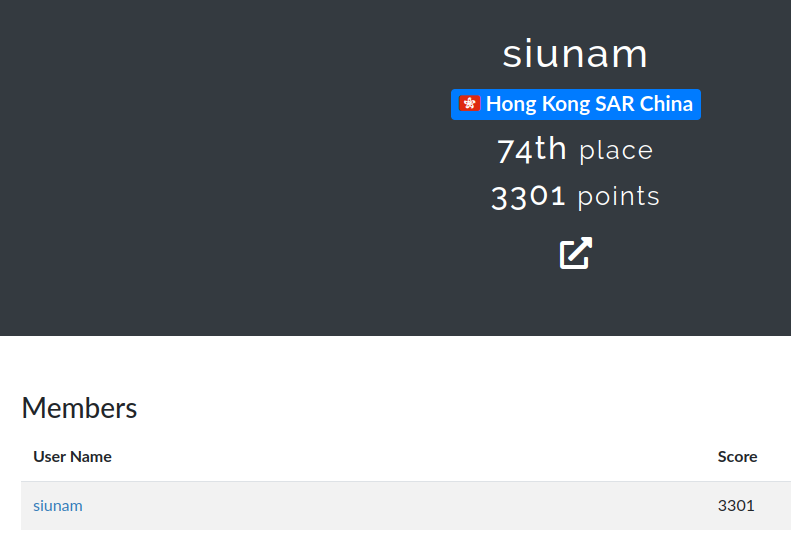
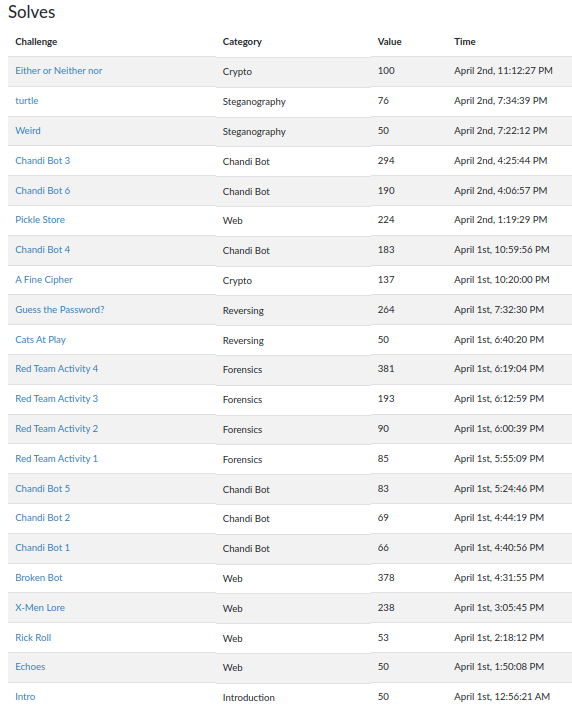
- Solved: 22/42
- Score: 3301/9362
- Rank: 74/717
- Overall Difficulty To Me: ★★★★☆☆☆☆☆☆
What I've learned in this CTF
- BIN-PWN:
- ret2win (Unsolved)
- Crypto:
- Many Time Pad XOR (Either or Neither nor)
- Deciphering Affine Cipher (A Fine Cipher)
- Forensics:
- Analysing Post-Exploitation Activity (Red Team Activity 1 - 4)
- Web of Lies (Unsolved)
- Missing Piece Part 1 (Unsolved)
- Steganography:
- Web:
- OS Command Injection (Echoes)
- Inspecting Source Pages (Rick Roll)
- XML External Entity (XXE) Injection (X-Men Lore)
- Insecure Deserialization In Python's Pickle Library (Pickle Store)
- Leaking Sensentive Information Via Telegram Bot API (Broken Bot)
- Reversing:
- Using
stringsTo List Out All The Strings Inside A File (Cats At Play) - Brute Forcing SHA256 Hash With Salt (Guess the Password?)
- Using
- Chandi Bot:
- Chandi Bot 1 - 6
- Extracting Hidden Information In An Image File (Chandi Bot)
- Exploiting Logic Vulnerability (Chandi Bot)
- Leaking Sensitive Information In Git Repository (Chandi Bot)